AppSec Vulnerabilities
This is the screen where users can drill down into the details of vulnerabilities discovered in the scans performed on the projects under the selected product, take action on vulnerabilities or export them.
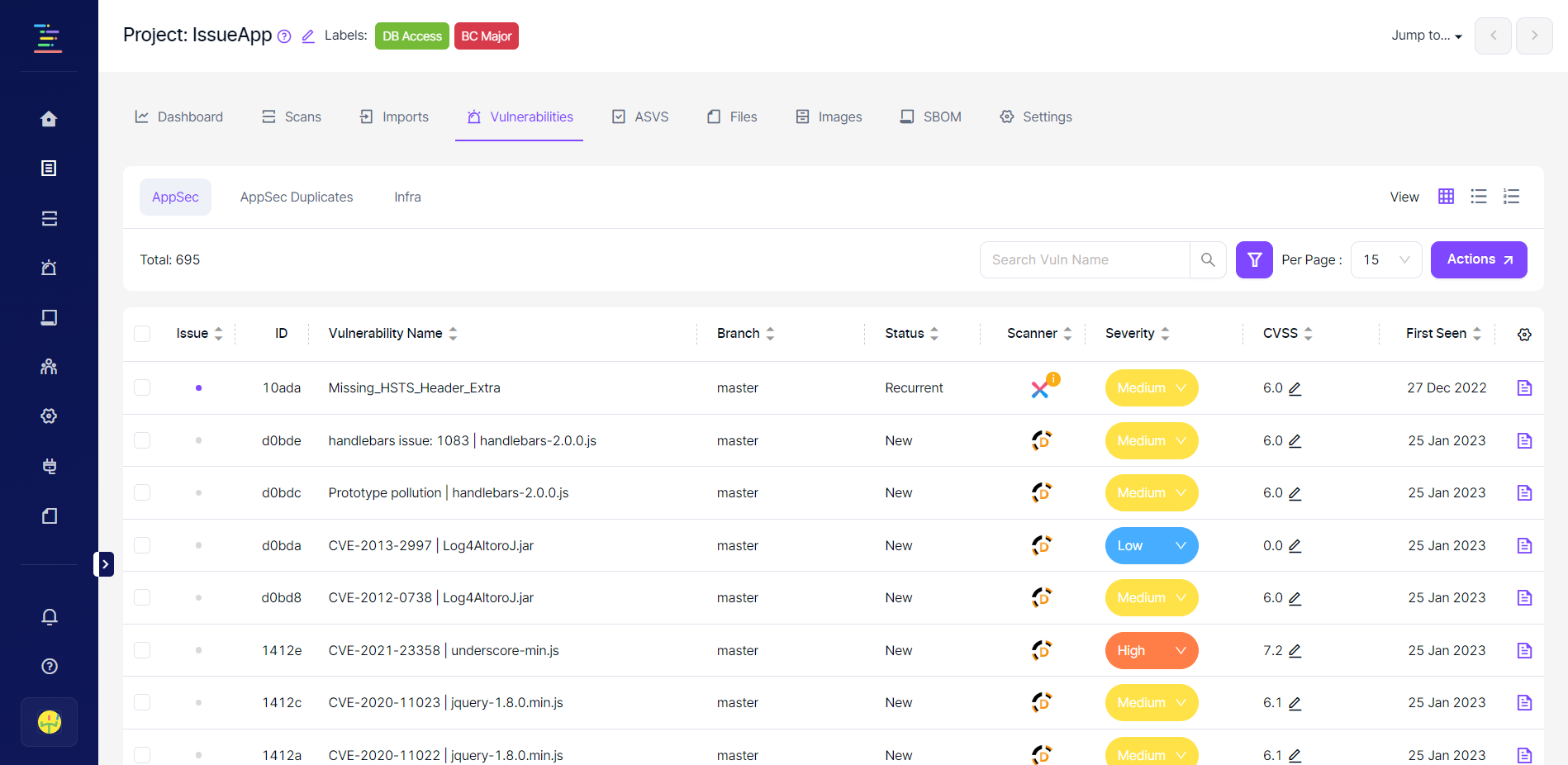
All vulnerabilities identified in the projects under the selected product since the platform's inception are listed in this section.
Blue circles to the left of each row in the table indicate a ticket has already been created on the issue manager for that vulnerability, and its status is still open on the issue manager.
The grey circle represents a vulnerability for which a ticket has not yet been created on the issue manager.
When the circle is red, that means the issue status on the issue manager is closed.
If the circle is already blue, selecting these vulnerabilities is impossible when the "Assign Issue" bulk action is clicked in the top left corner.
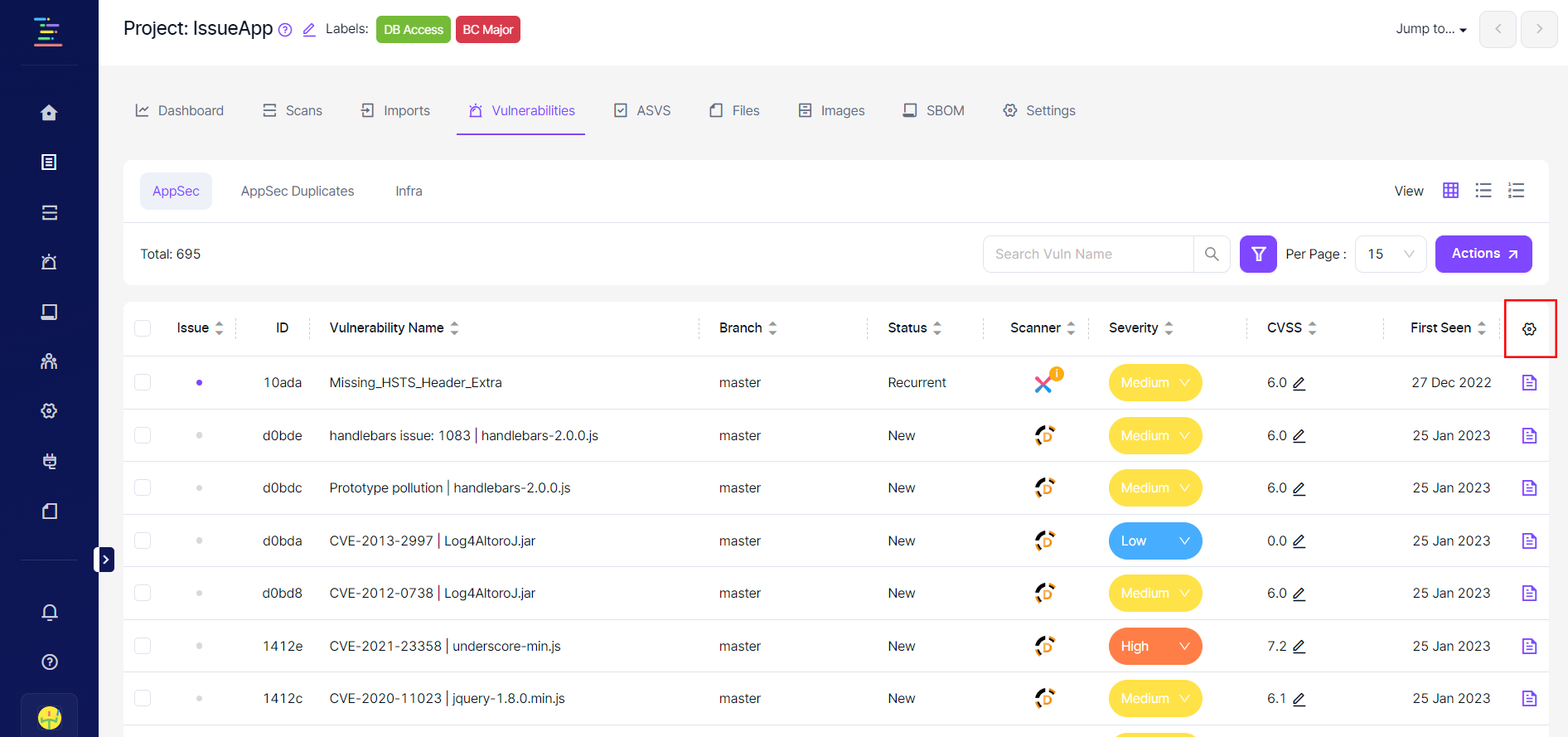
Columns on the table can be modified by clicking the icon on the upper right corner of the vulnerability table, as seen in the screenshot below.
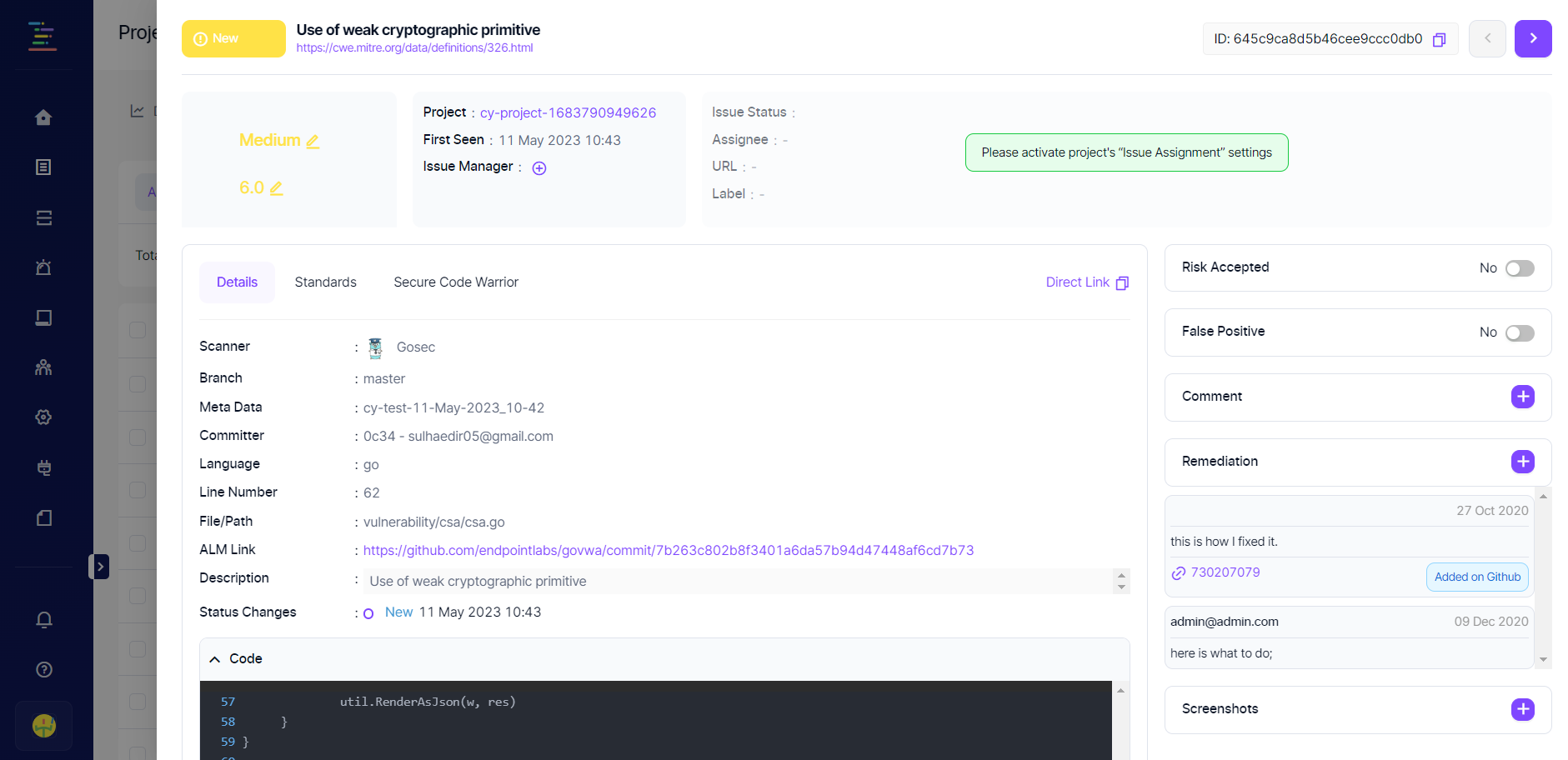
Additional vulnerability details can be seen by clicking the page icon on each row's rightmost side. Details presented vary depending on the tool that has identified the vulnerability.
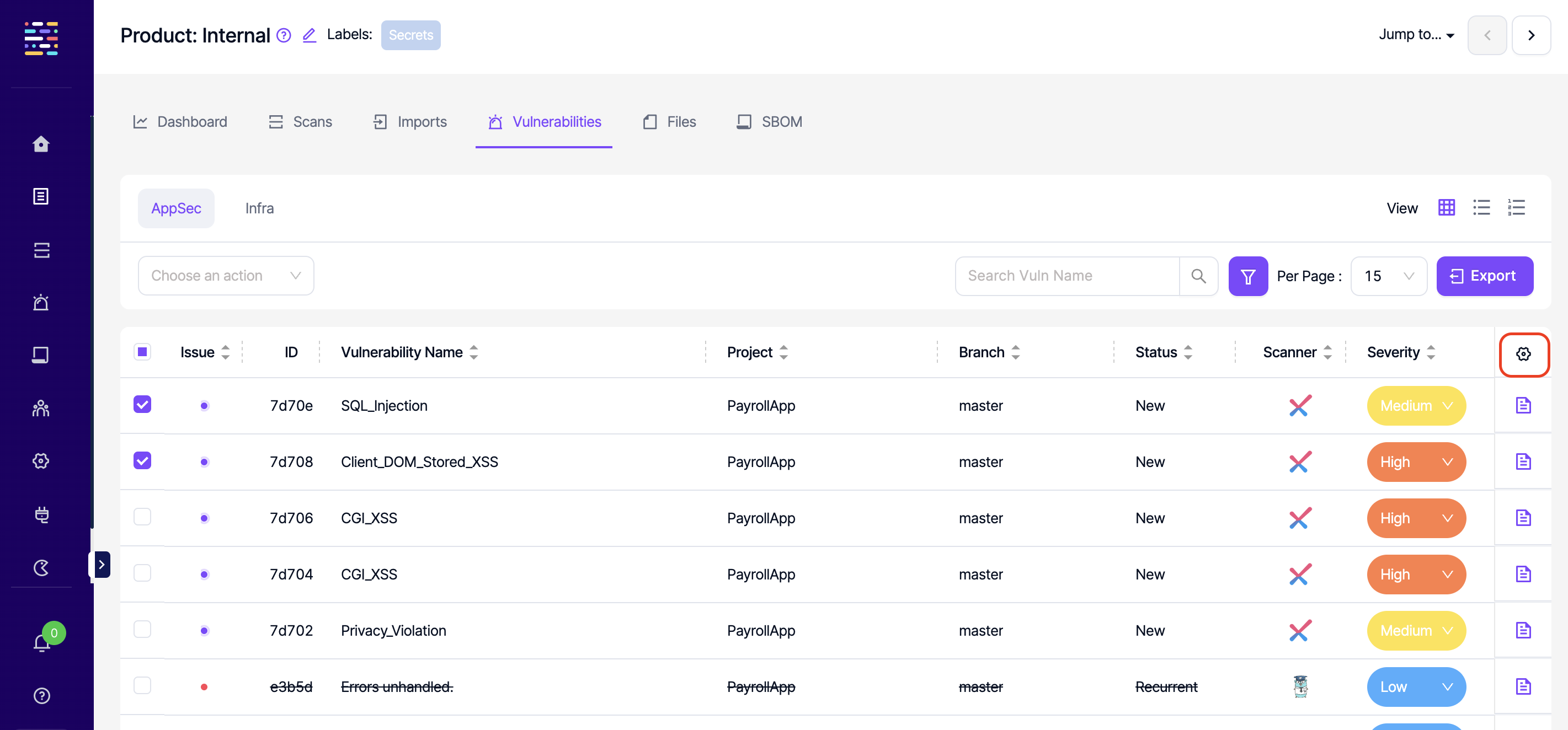
If an issue will be created manually, the checkbox to the left of the vulnerability is checked, and "Assign Issue" is selected in the "Choose an action" drop-down menu.
Clicking on this button opens a new modal where a selection can be made whether to create a single ticket on the issue manager for the selected vulnerabilities or create separate tickets for each vulnerability.
If multiple vulnerabilities are grouped into a single ticket, then certain automated workflows such as validation scans or reflecting the status of the vulnerability on the ticket will not work until the status of all vulnerabilities become "Closed" on Kondukto. However, if the ticket is closed on the issue manager, the issue status of vulnerabilities will be transitioned to "Closed" on Kondukto and a validation scan will be triggered if configured. If the same vulnerabilities are rediscovered in the validation scan, Kondukto will not be able to reopen the ticket.
Other possible bulk actions are; closing manually imported vulnerabilities, suppressing vulnerabilities (false-positive or risk accepted), and adding screenshots.
Team Lead and Admin level users can mark vulnerabilities as false positives by entering false-positive descriptions without requiring approval.
Developer-level users can only send a false positive request that their team leads or the admin must approve.
Vulnerabilities displayed on the table can also be exported in .csv format by clicking the Export button in the top right corner. The columns available on the table can be changed by clicking on the gear icon located in the top right corner of the table as seen in the screenshot below.
Vulnerability view can be changed using the view options as seen in the screenshot below.
Updated 8 months ago
