SAML 2.0 - Azure AD Integration
- Login to your “Microsoft Azure Portal”.
- Select “Enterprise Applications” from the left menu.
- Click the “New Application” button on the Enterprise Applications page.
- Click the “Create your own application” button.
- Fill in the application name as “kondukto-saml” and click the “Create” button.
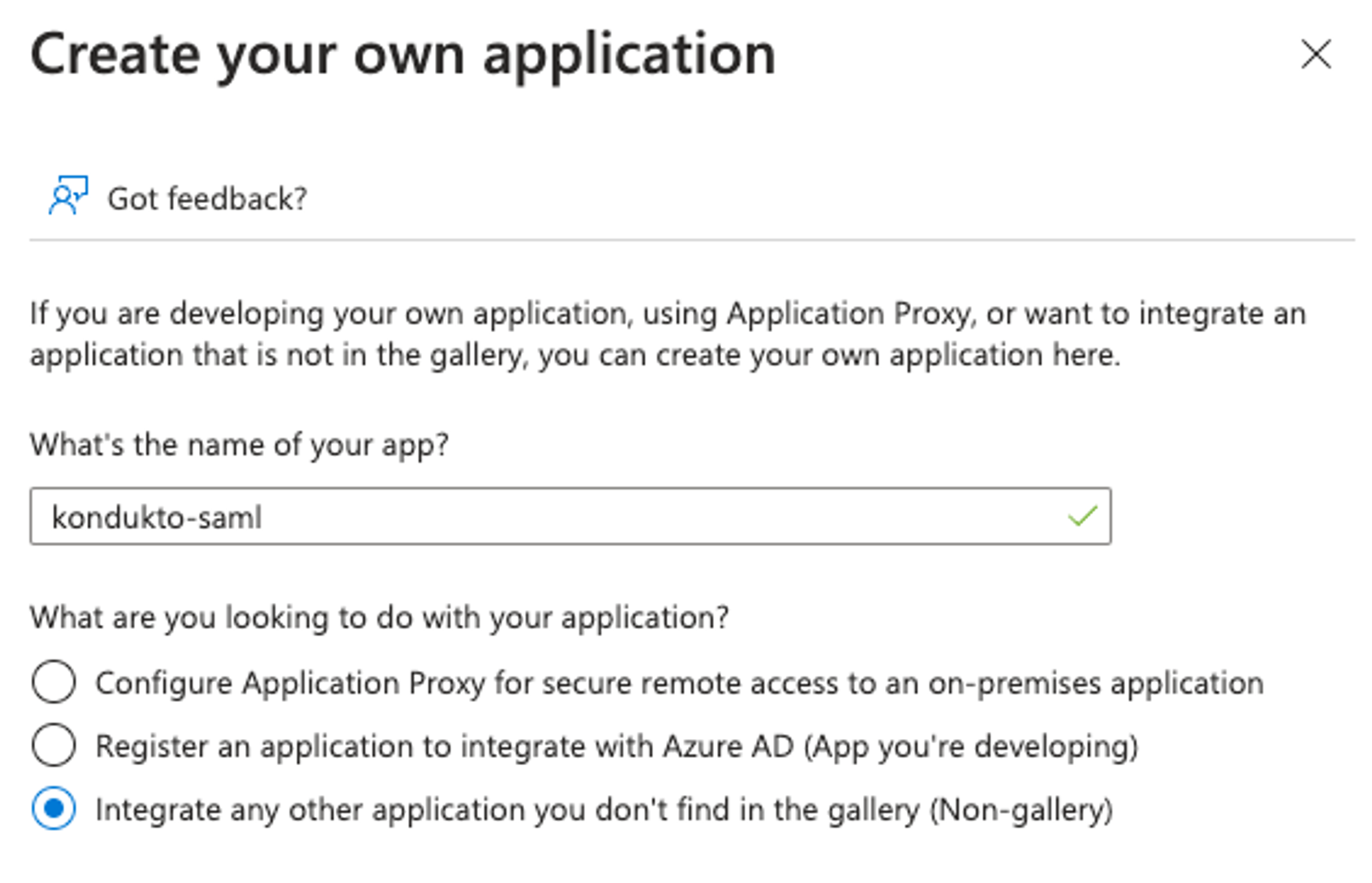
- Select “Set up single sign on” in the “kondukto-saml” enterprise application page.
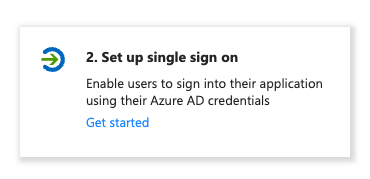
- Select “SAML” as a single sign-on method.
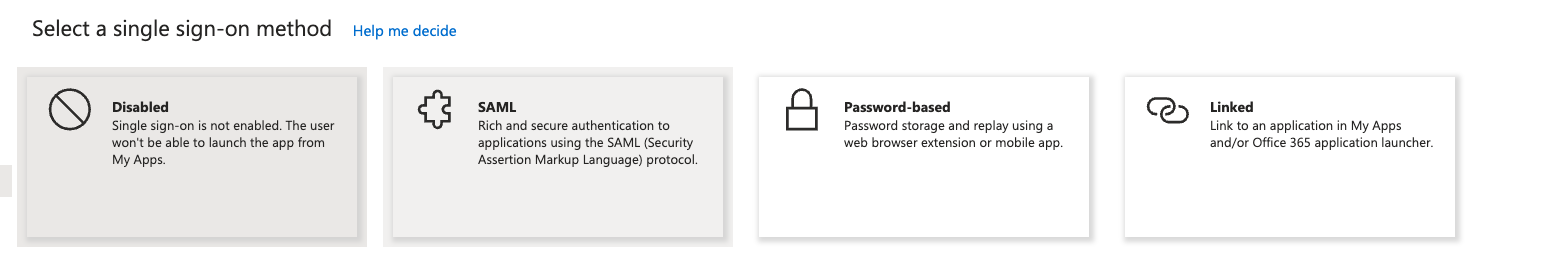
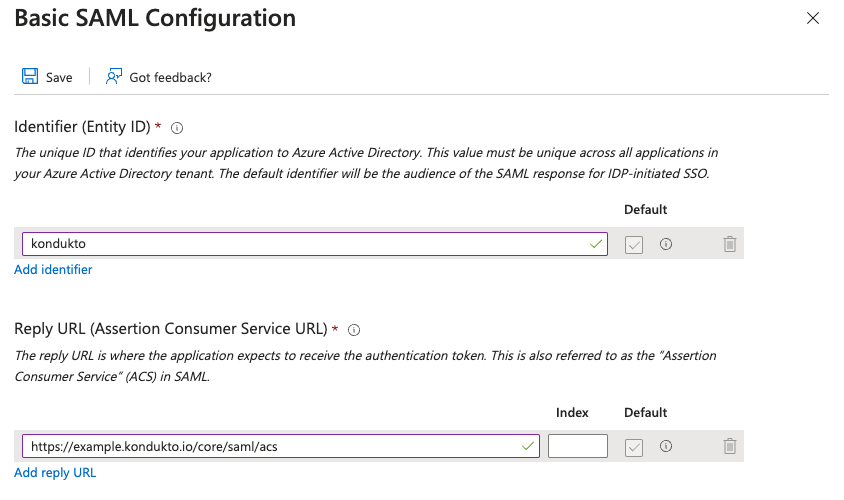
- Click the “Edit” button in the “Basic SAML Configuration” panel.
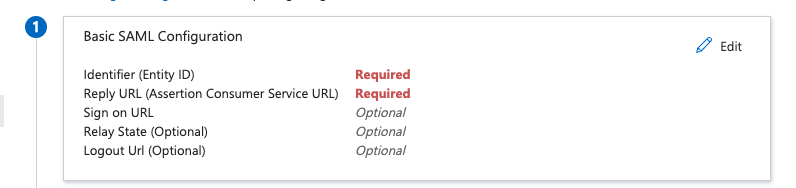
- Fill “Entity ID” and “Assertion Consumer Service URL” fields and click the “Save” button.
- Click the “Edit” button in the “Attributes & Claims” panel.
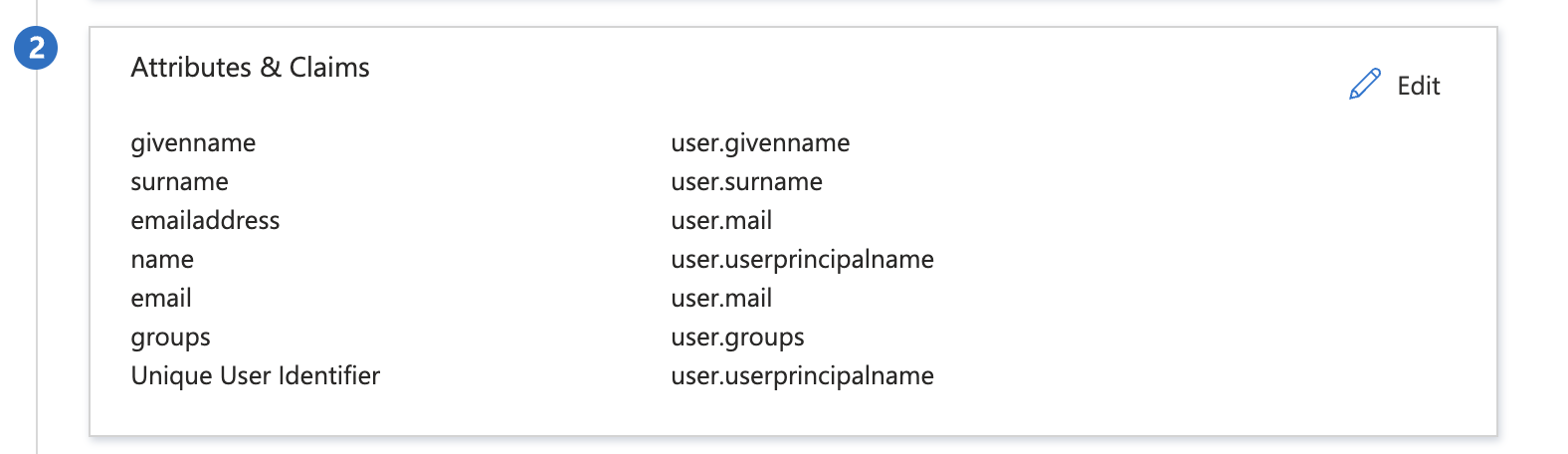
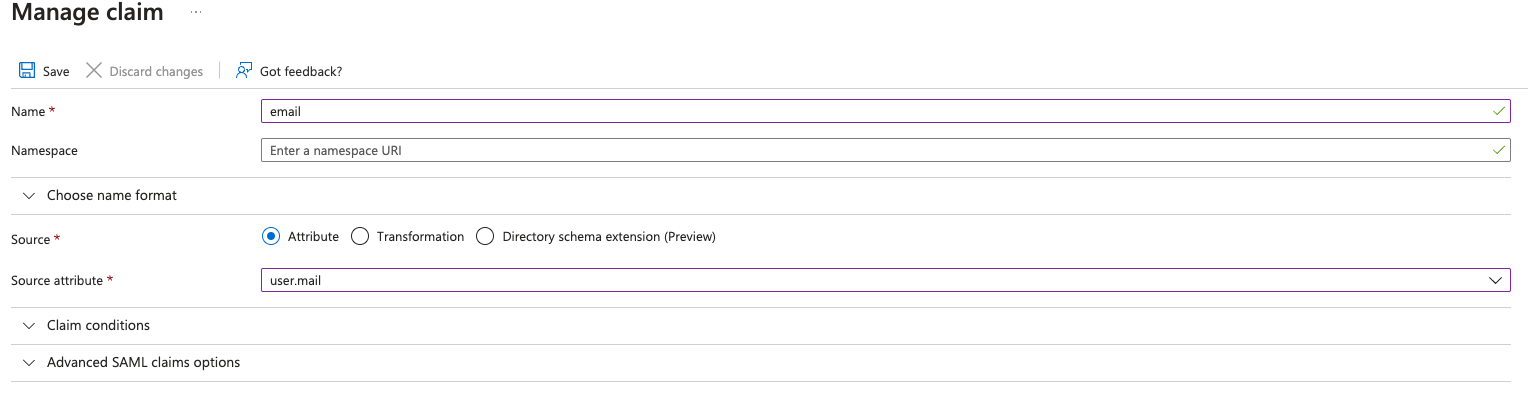
- Click the “Add new claim” button
- Add “user.mail” attributes as “email” claim and click the “Save” button.
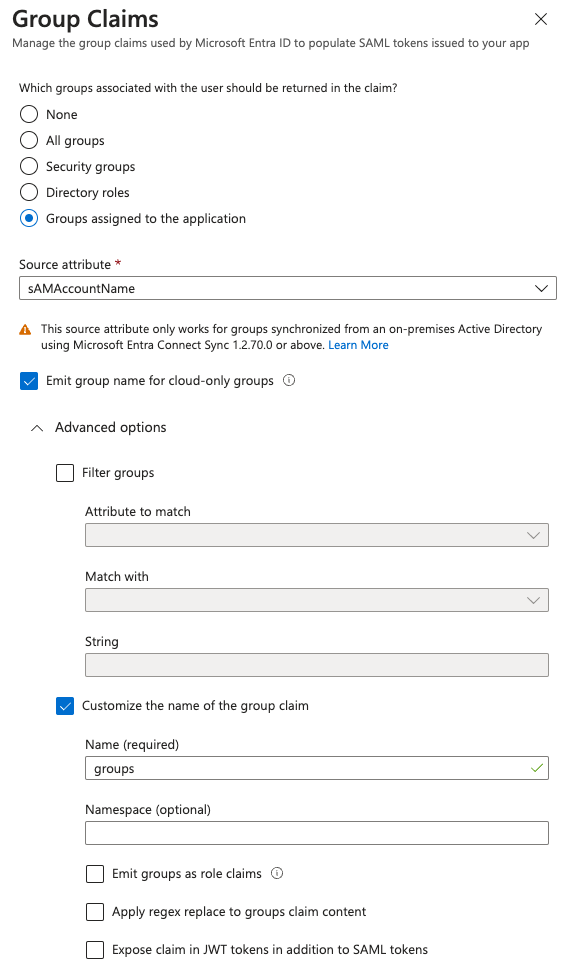
- Click the “Add a group claim” button.
- Add the groups assigned to the application as “groups” claim and click the “Save” button.
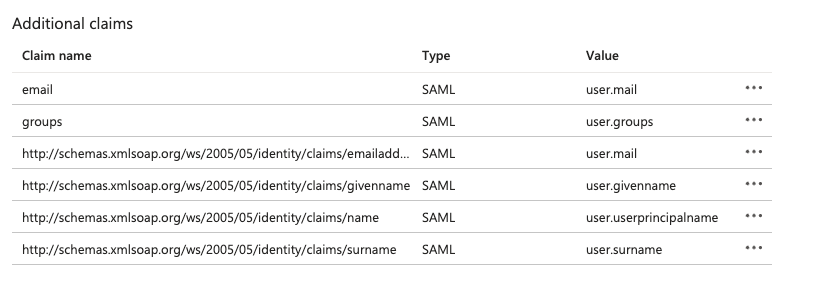
- Make sure “email” and “groups” claims are listed in the “Additional claims” table.
- Return to the “Set up Single Sign-On with SAML” page.

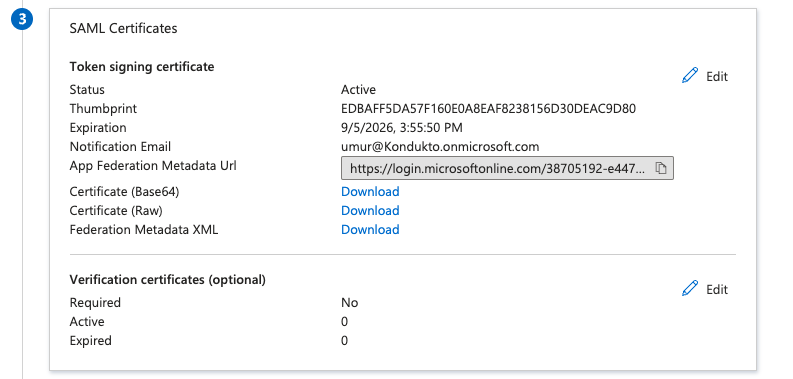
- Download the “SAML Certificate” in Base64 format to a safe place.
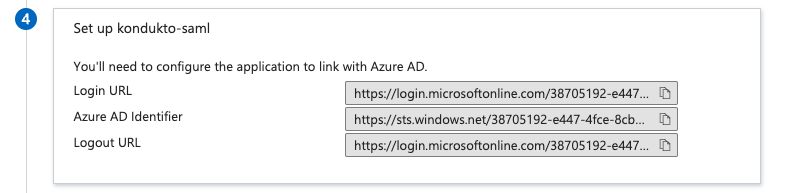
- Copy “Login URL” and “Azure AD Identifier” values to a safe place.
- Login to your Kondukto application with an admin user.
- Select “Integrations” from the left menu.
- Select “Single Sing-On Tools” on the integrations page.
- Activate the “SAML” integration.
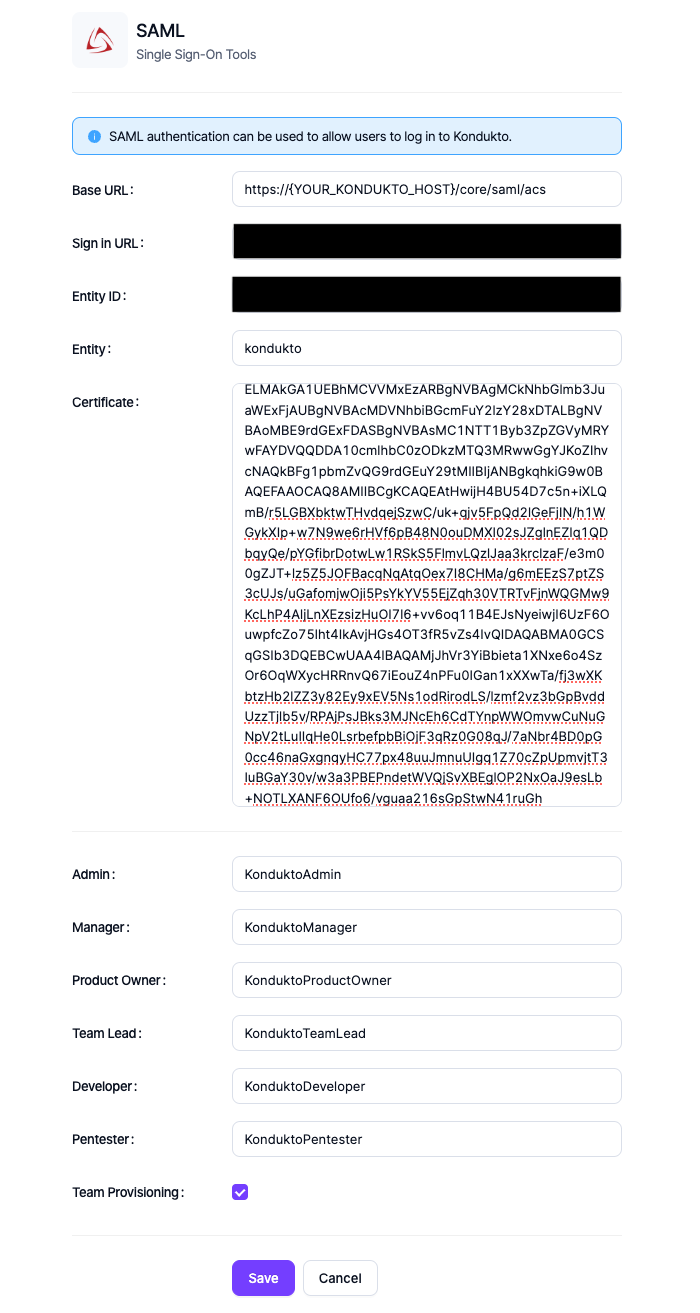
- Fill in the SAML integration fields and click the “Save” button.
- Base URL: https://{YOUR_KONDUKTO_HOST}/core/saml/acs
- Sign In URL: The copied “Login URL” value in step 18.
- Entity ID: The copied “Azure AD Identifier” value in step 18.
- Entity: kondukto
- Certificate: The downloaded “Certificate (Base64)” value in step 17.
- Admin: The Azure AD group name whose members are going to have an admin role in Kondukto
- Manager: The Azure AD group name whose members are going to have a manager role in Kondukto
- Product Owner: The Azure AD group name whose members are going to have a product owner role in Kondukto
- Team Lead: The Azure AD group name whose members are going to have a team lead role in Kondukto
- Developer: The Azure AD group name whose members are going to have a developer role in Kondukto
- Pentester: The Azure AD group name whose members are going to have a pentester role in Kondukto
- Team Provisioning: If checked, Azure AD groups will be created as a team in Kondukto.
- On the “kondukto-saml” enterprise application “Overview” page, click the “Assign users and groups” panel and assign the Azure AD groups that are mapped with Kondukto roles.
- Click the “Login with SAML” button on the Kondukto application login page to log in with a user of the Azure AD “kondukto-saml” app.

- Log in to the Azure AD user credentials to log in to the Kondukto application.
Updated 3 months ago
