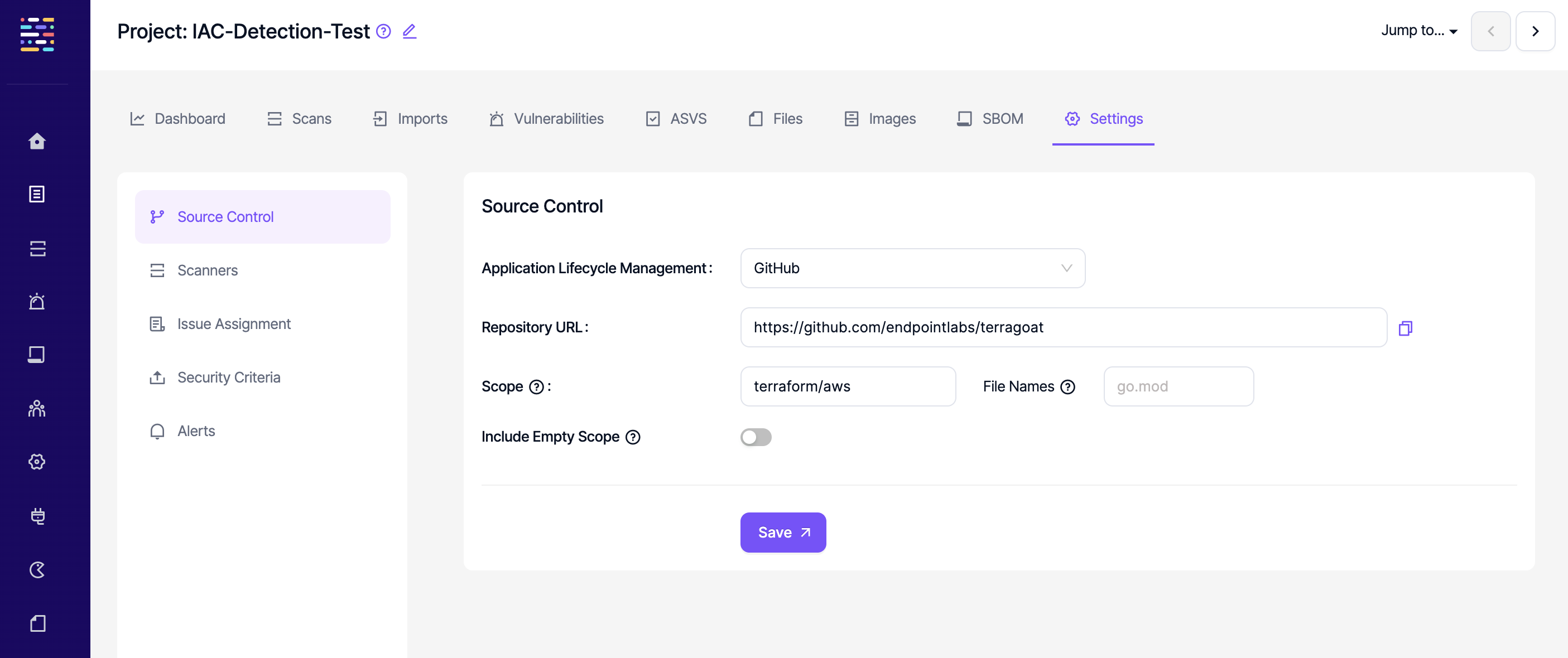
Source Control
This step needs to be completed to be able to perform scans using open-source SAST, SCA, and IaC scanners and to find committers of SAST and IaC vulnerabilities.
Kondukto can identify developers who have introduced vulnerabilities discovered by SAST and IaC tools and provide the committer benchmark view only if the source control information is provided.
Users can disable software development platform integration in this tab by selecting "None" in the ALM drop-down menu. The repository URL of a project can also be changed here, which will be effective starting from the following scan.
If the project is scanned using the same scanner after updating the repo URL, Kondukto will switch the status of all vulnerabilities previously discovered by the scanner to closed after the new scan, as they will not be re-discovered and assumed to be fixed due to the change in the repo URL.
For mono repo projects, scope and file name fields can be used for Kondukto to include only vulnerabilities discovered under specified paths or files in the project.
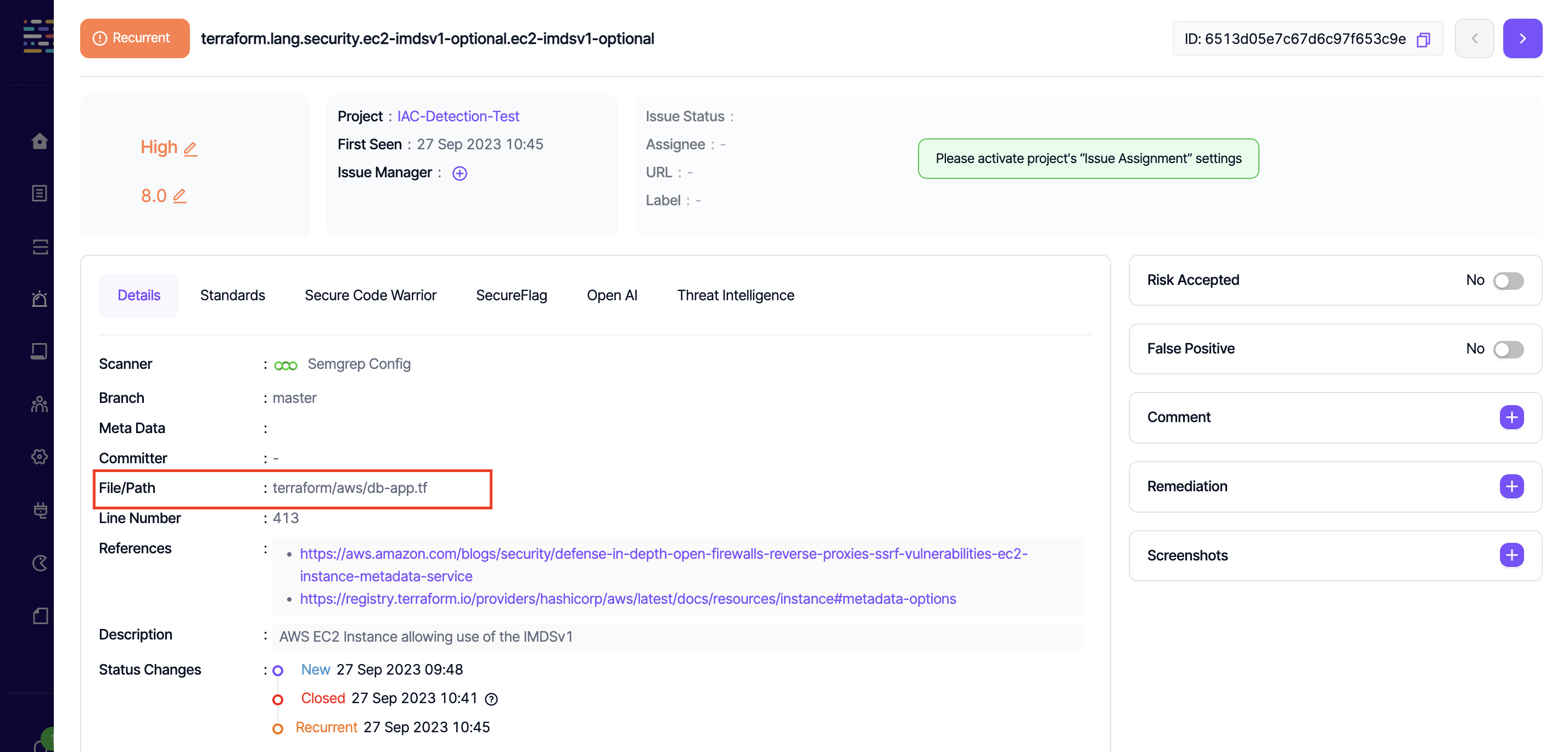
For a vulnerability discovered in the path "terraform/aws/db-app.tf", Kondukto would include it in the project if "terraform/aws" or "terraform" is entered in the Scope field.
However, entering "db-app.tf" in the File Names field would not make Kondukto capture the vulnerability in this project.
For certain vulnerabilities with no path but with only a file name, those file names can be entered in the "File Name" field so that Kondukto can automatically place those vulnerabilities under the project.
SCA vulnerabilities that contain ":" in the Dependency File field are not taken into account and they are included in the project regardless of the paths or files specified under source control settings.
Include empty scope toggle can be enabled to include vulnerabilities with no path in the project.
Updated 9 months ago
