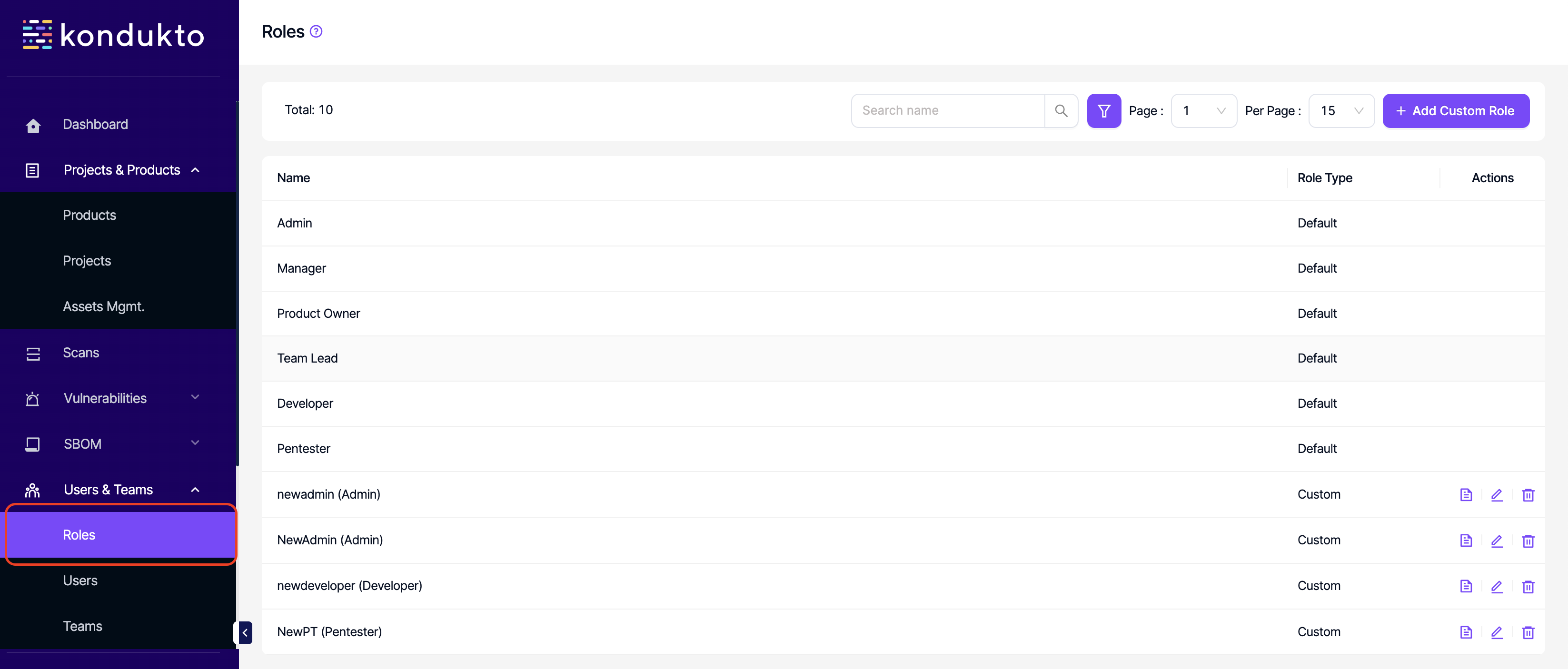
Roles
There are 6 built-in roles on Kondukto which are;
- Admin
- Manager: Responsible for business units and products.
- Product Owner: Responsible for products. At a project level, has only read-only permissions for the dashboard, vulnerabilities and SBOM of projects under relevant products.
- Team Lead: Responsible for projects. At a product level, can only access products that are associated with a project that their team is assigned to or they are granted access to as a user.
- Developer: A view-only role that only has access to projects. The only action they can take is sending suppression requests.
- Pentester: Can only access projects to import vulnerabilities.
To see permission of each role, please visit https://docs.kondukto.io/docs/user-permission-matrix.
Custom roles can also be created in this section.
When creating a custom role, a parent role needs to be selected to inherit base permissions from.
New permissions can not be added to the existing permissions of the parent role but the existing permissions can removed.
Therefore, when creating a custom role, the parent role should be selected with care so that the custom role with required permissions can be created with minimum effort.
If there is uncertainty about the required permissions of a custom role, selecting admin as the parent role is recommended as it has the widest base permissions available.
- Global Dashboard: Read: This permission controls the user's ability to view the Dashboard menu on the side navigation menu.
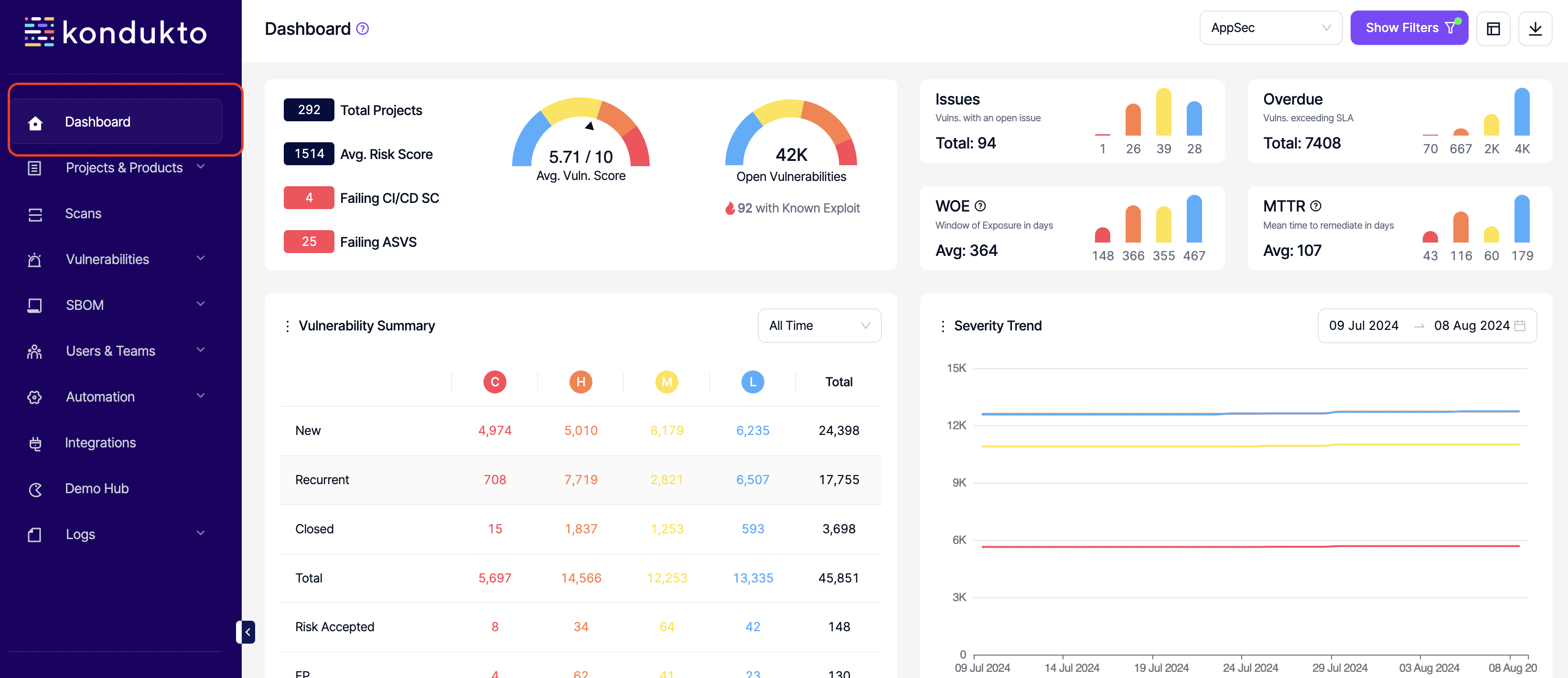
PRODUCT PERMISSIONS
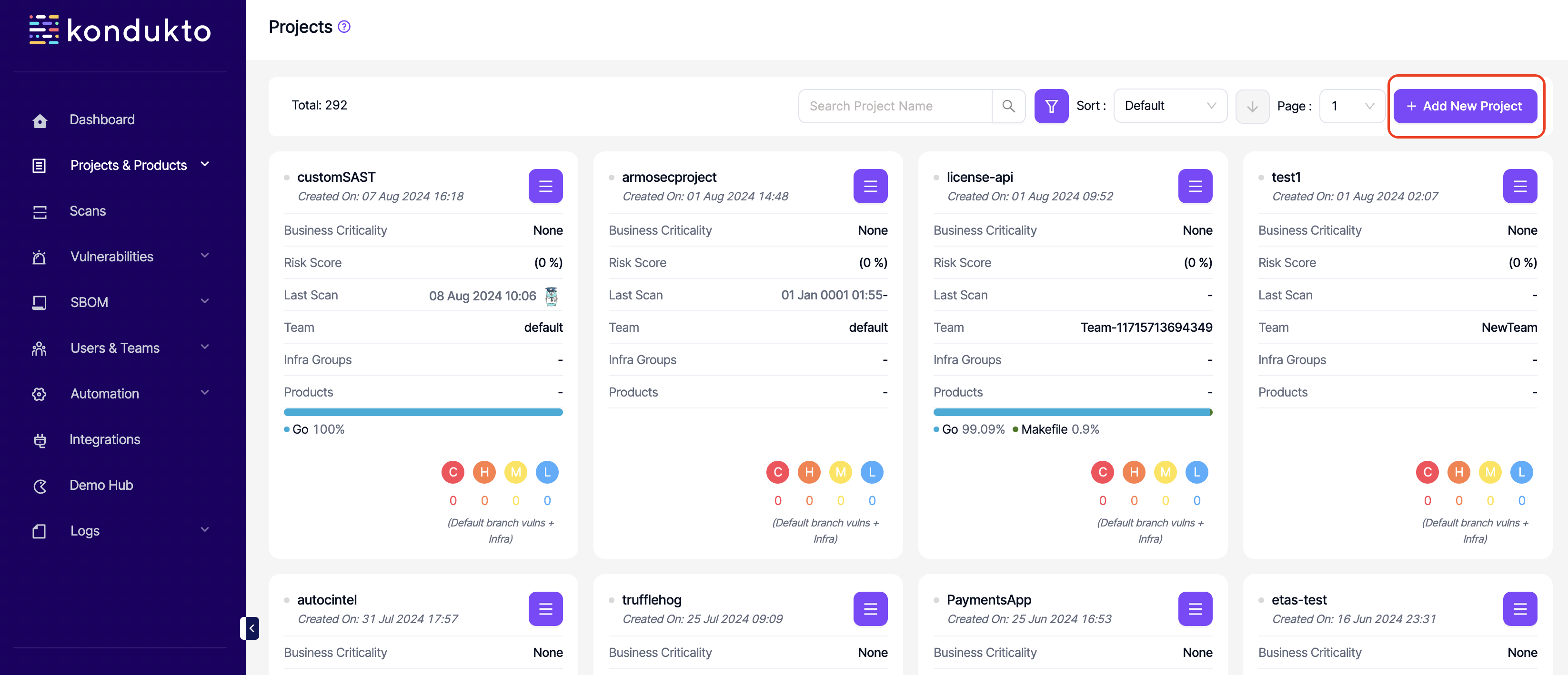
- Products: Read: This permission controls the user's ability to view the Products section on the side navigation menu and therefore the ability to access products. All product related permissions should be removed to be able to remove this permission.
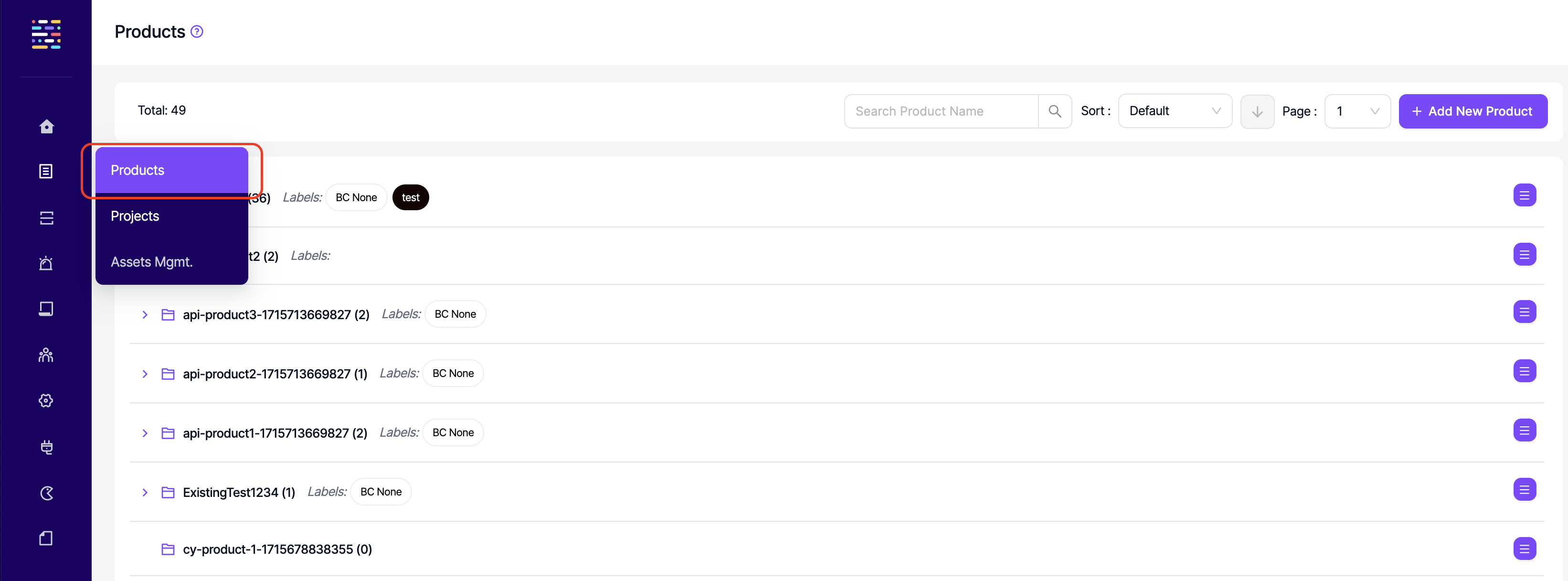
- Products: Add: This permission controls the user's ability to add new products.
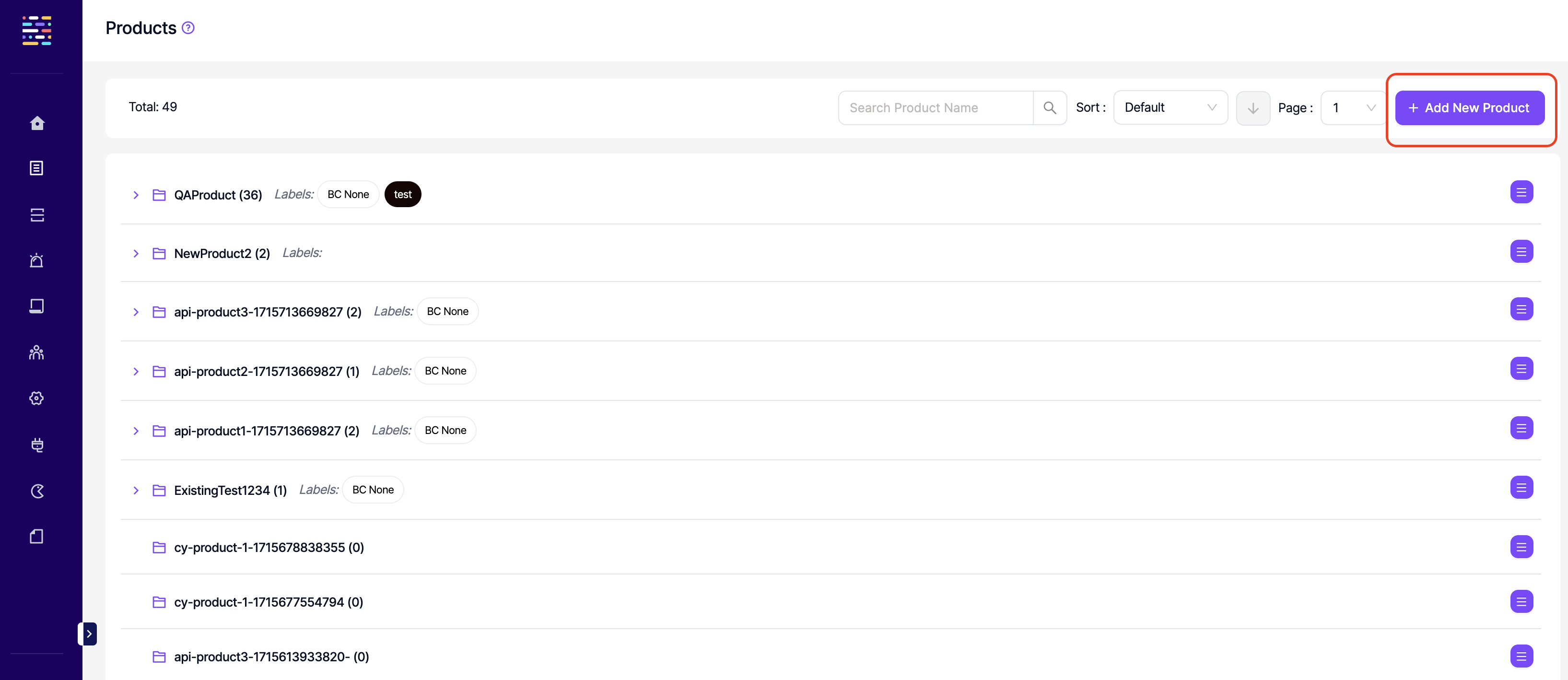
- Products: Write: This permission controls the user's ability to edit products.
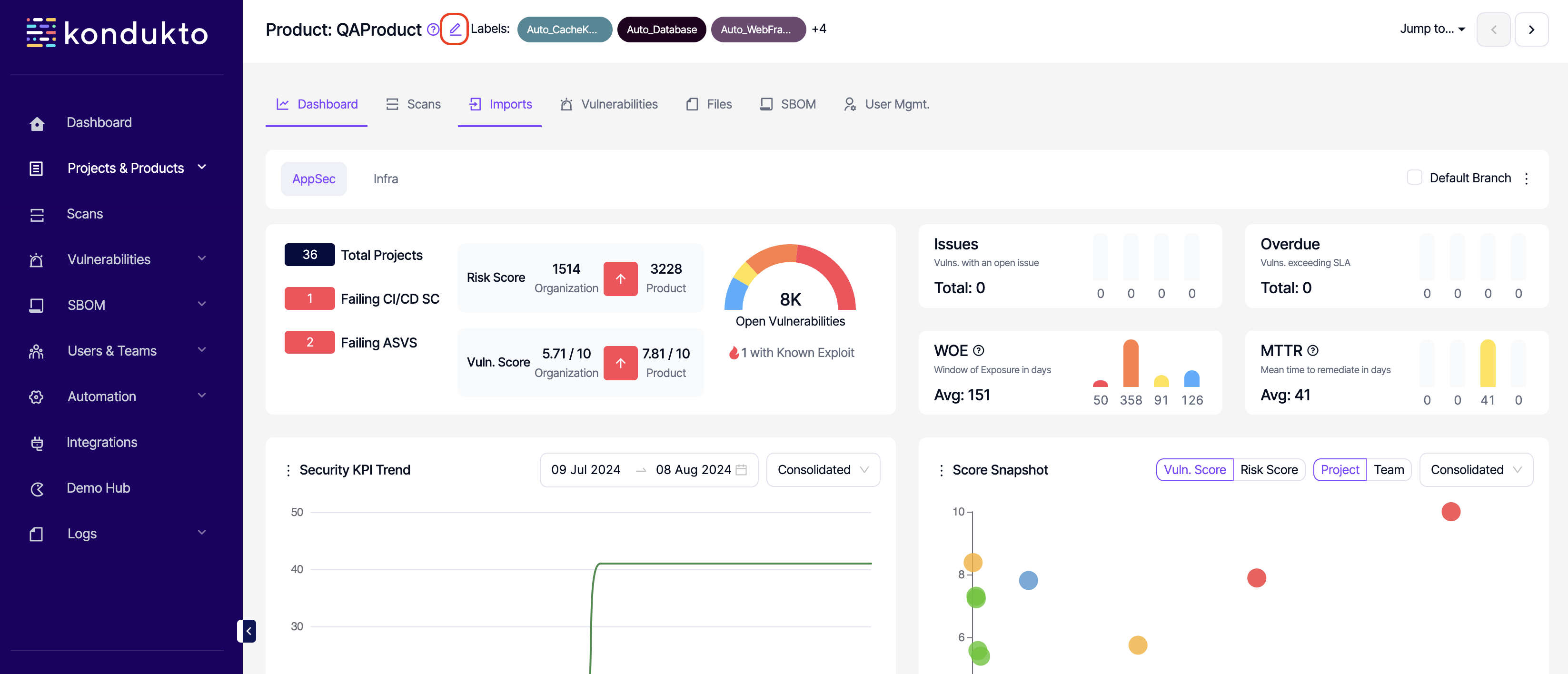
- Products: Delete: This permission controls the user's ability to delete products.
- Product Dashboard: Read: This permission controls the user's ability to view dashboard section under products.
- Product Files: Read: This permission controls the user's ability to view files section under products.
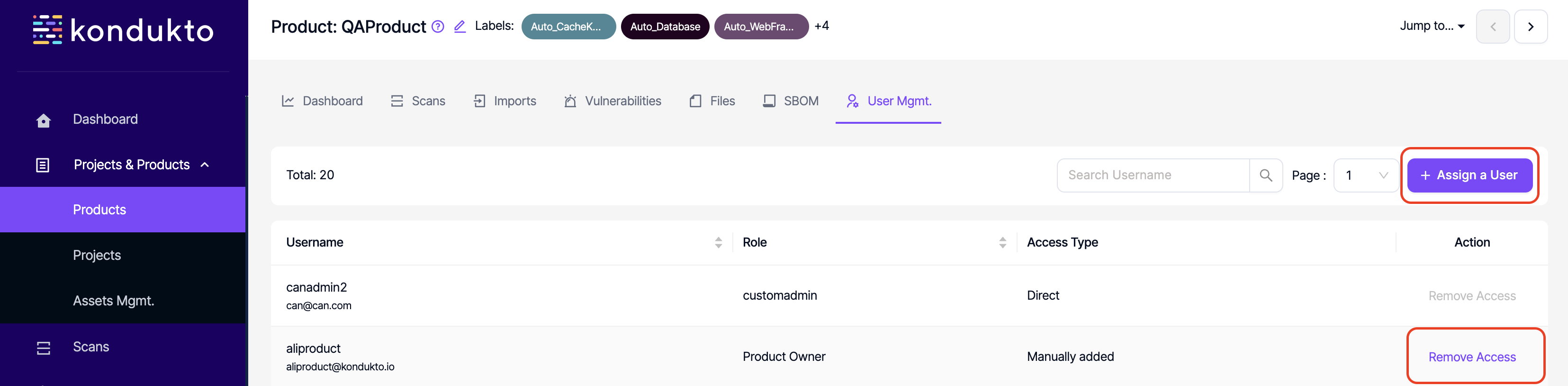
- Product User Mgmt.: Read: This permission controls the user's ability to view user mgmt. section.
- Product User Mgmt.: Write: This permission controls the user's ability to add, delete users or remove access of users in the user mgmt. section under products.
PROJECT PERMISSIONS
- Projects: Add: This permission controls the user's ability to add new projects manually.
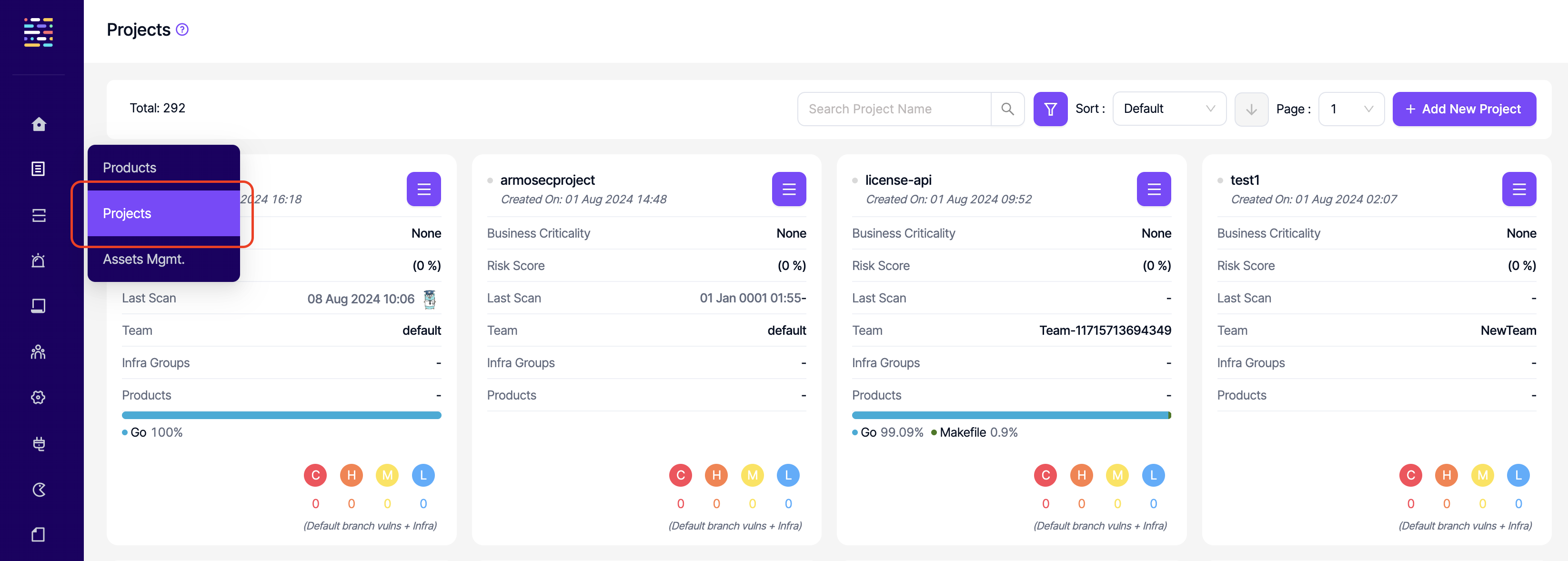
- Projects: Read: This permission controls the user's ability to view the Projects section on the side navigation menu and therefore the ability to access projects. All project related permissions should be removed to be able to remove this permission.
- Projects: Delete: This permission controls the user's ability to delete projects.
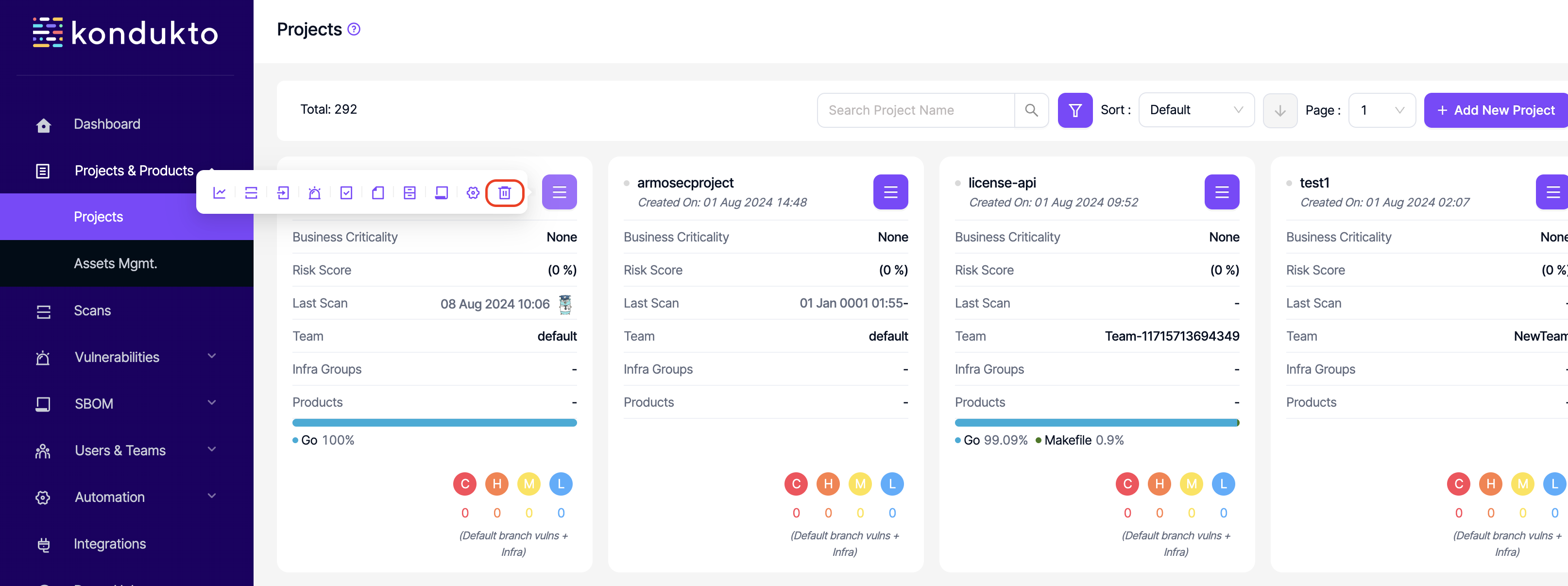
- Projects: Write: This permission controls the user's ability to edit existing projects.
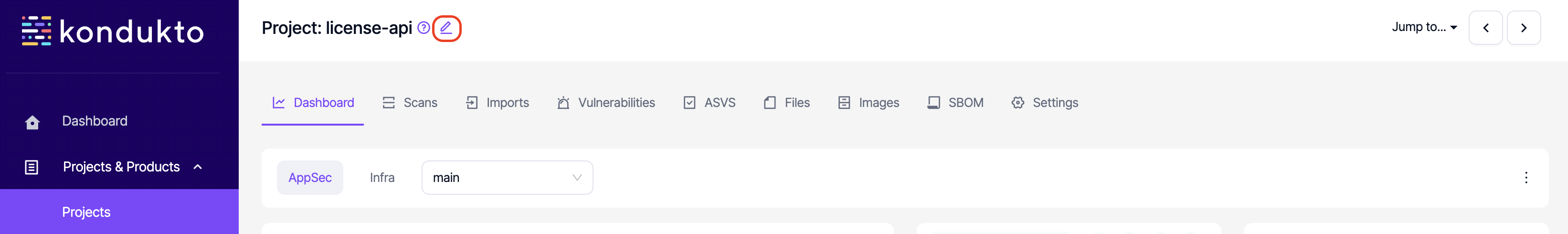
- Project Dashboard: Read: This permission controls the user's ability to view dashboard under projects.
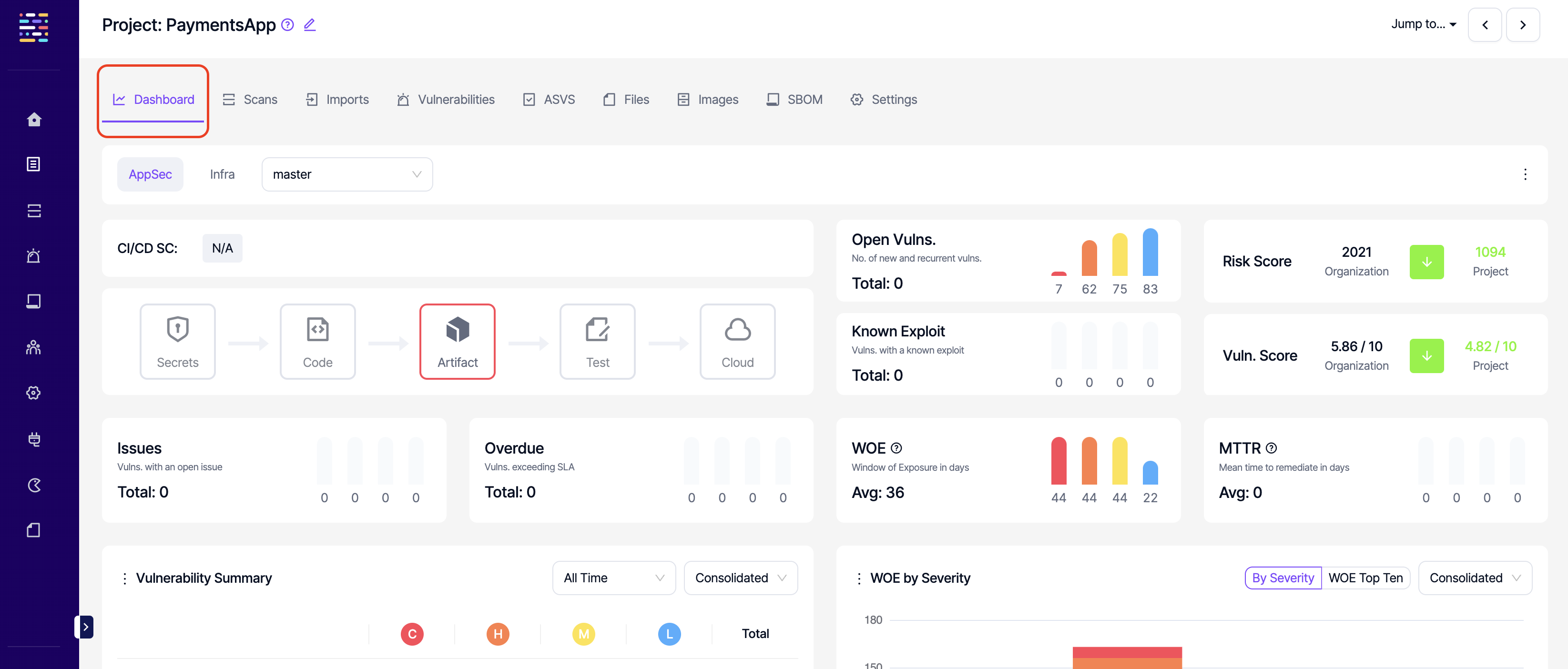
- Project ASVS: Read: This permission controls the user's ability to view ASVS section under projects.
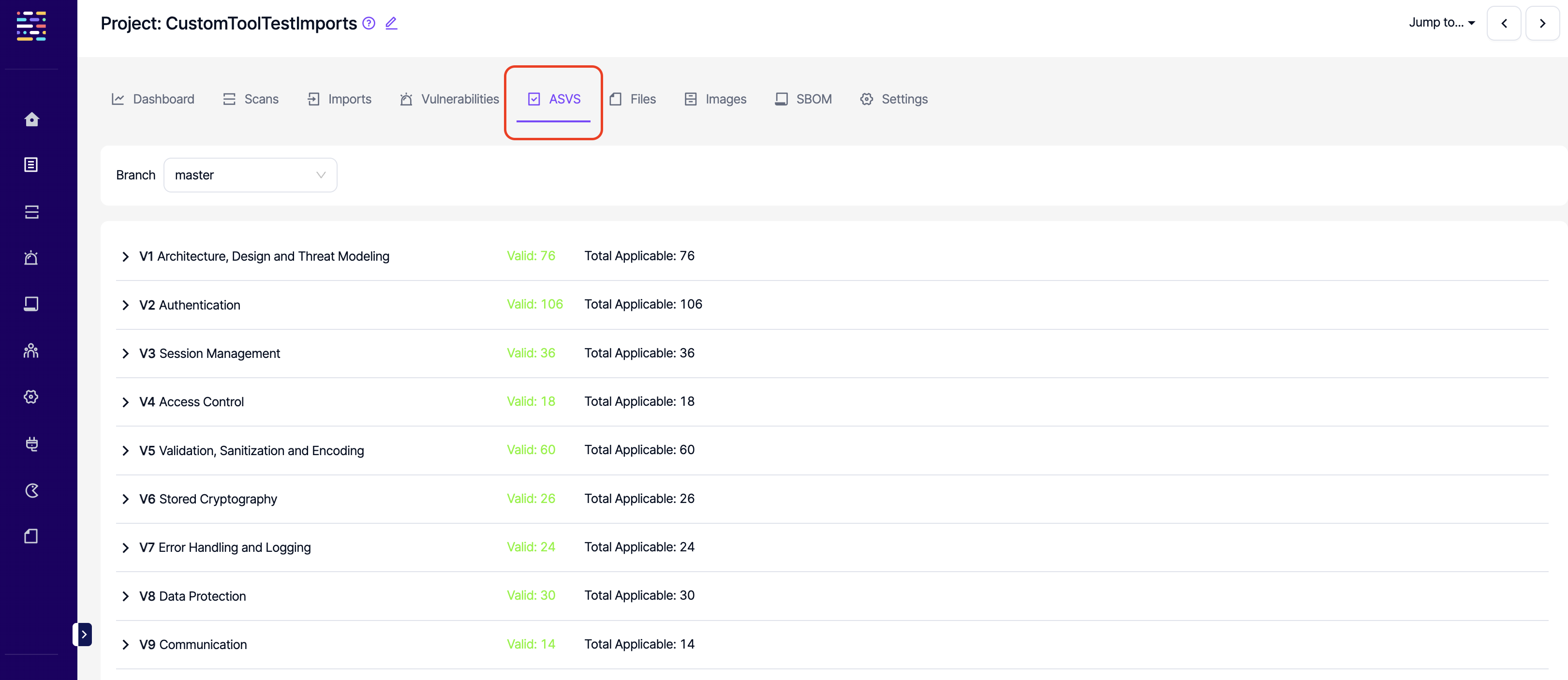
Project Files: Read: This permission controls the user's ability to view Files section under projects.
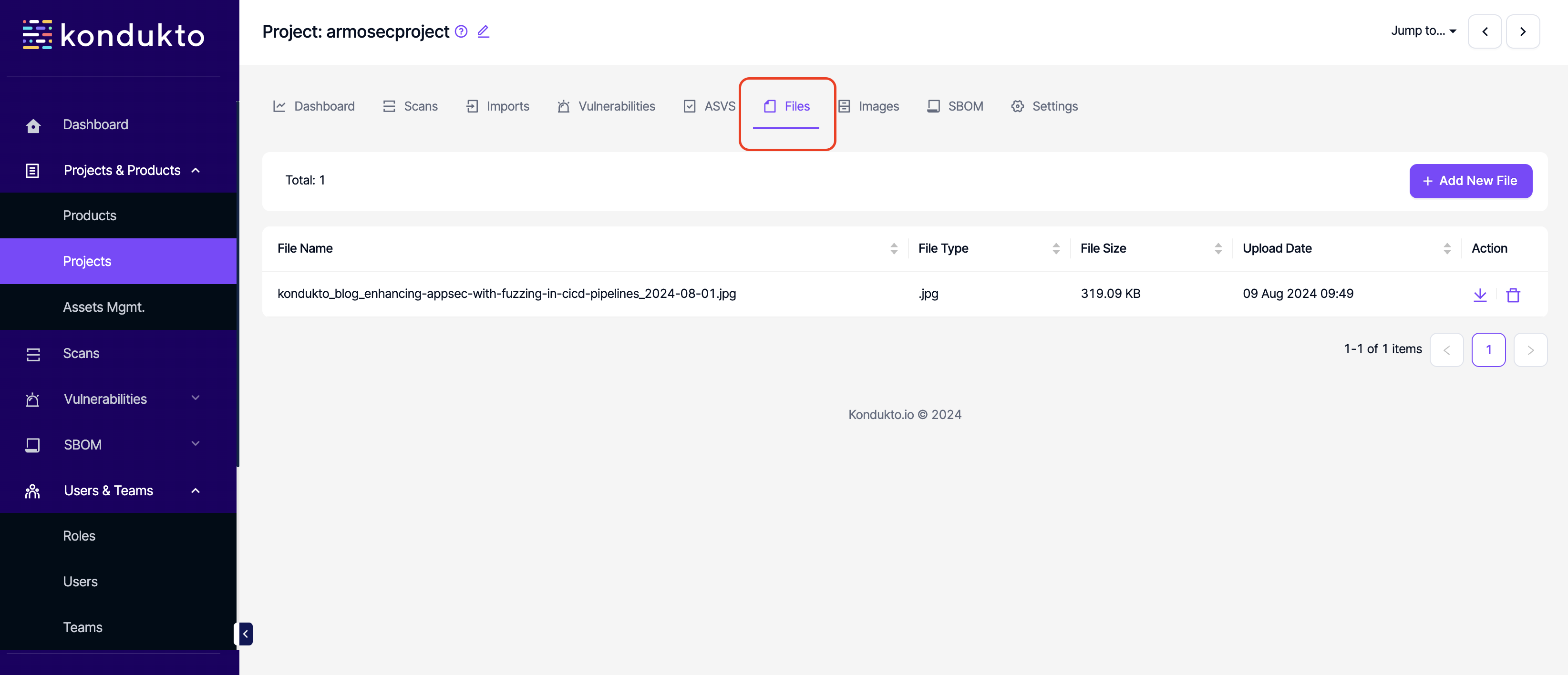
- Project Files: Write: This permission controls the user's ability to add new files to projects.
- Project Files: Delete: This permission controls the user's ability to delete files from projects.
- Project Images: Read: This permission controls the user's ability to view Images section under projects.
- Project Settings: Read: This permission controls the user's ability to view the Settings section under projects.
- Project Settings: Write: This permission controls the user's ability to edit project settings. It could be used for permissions related to changing the repo URL of a project, assigning scanners to a project or assigning automation rules to a project. When disabled, Save and Add buttons will not be available under any of the sections in project settings.
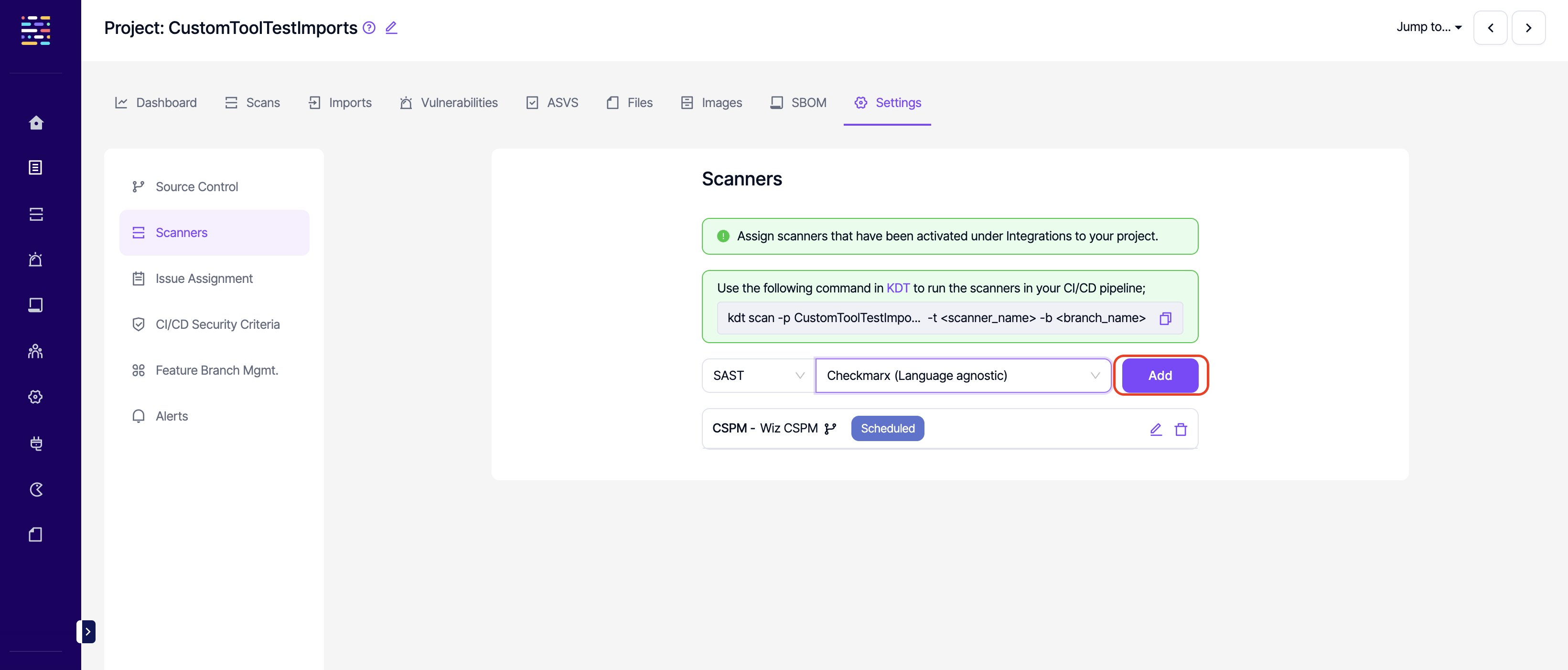
ASSETS MGMT. PERMISSIONS
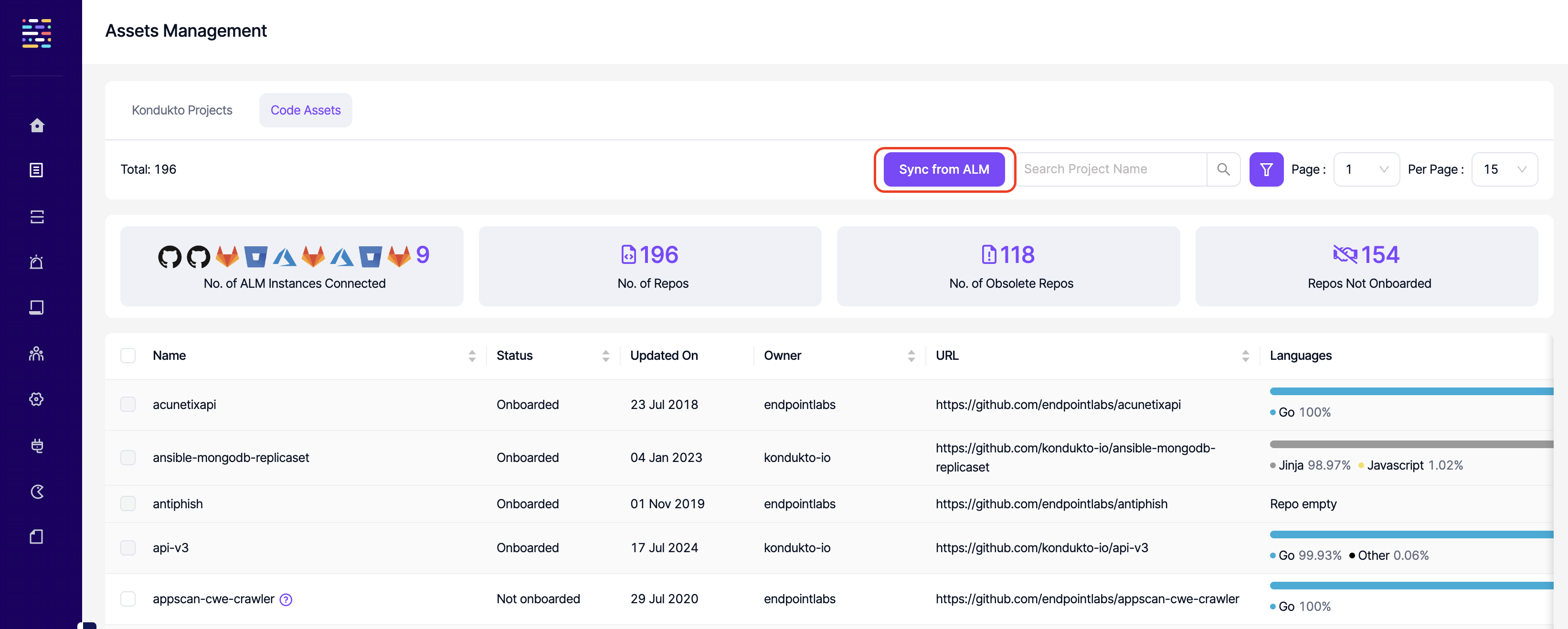
- Assets Mgmt.: Read: This permission controls the user's ability to view the Assets Mgmt. section on the side navigation menu. Projects:Read permission should also be available for this section to be visible.
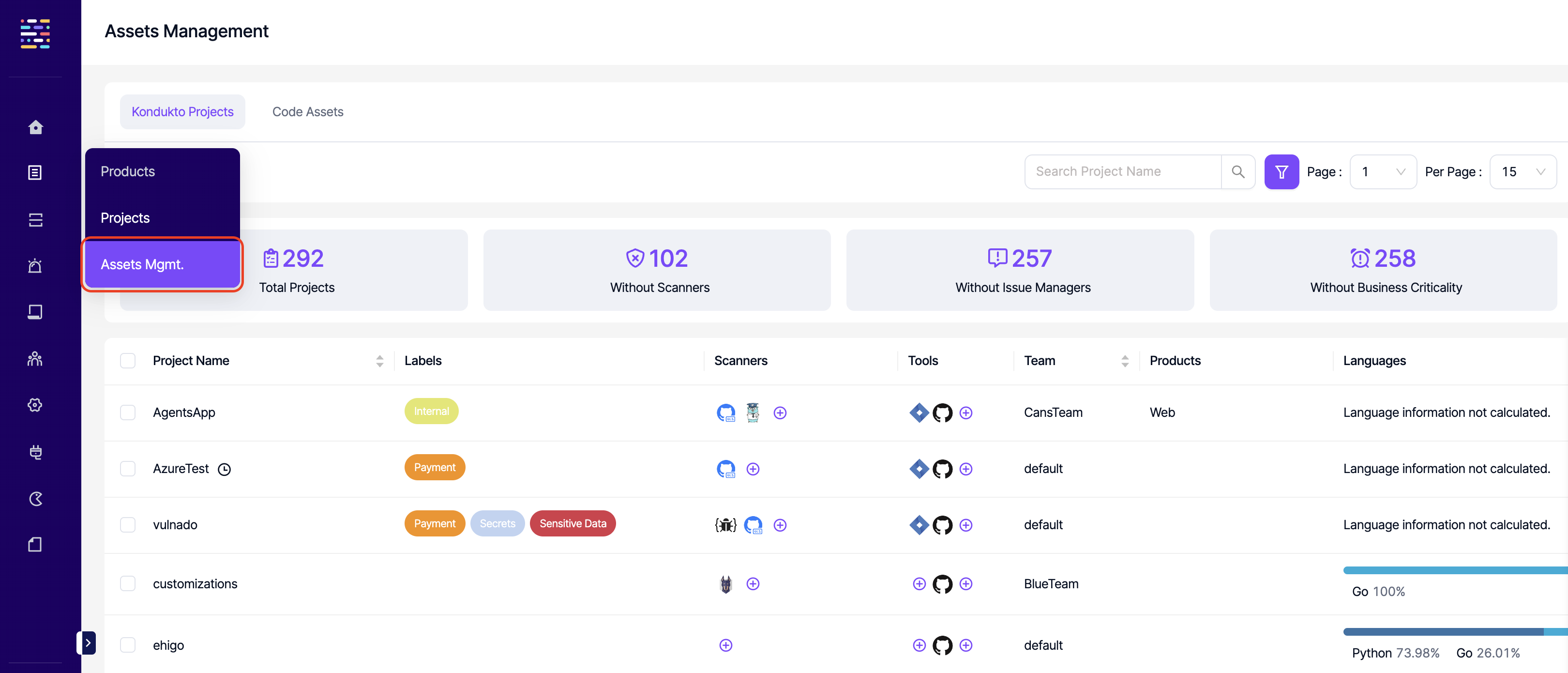
- Code Assets: Read: This permission controls the user's ability to view the Code Assets section under Assets Mgmt.
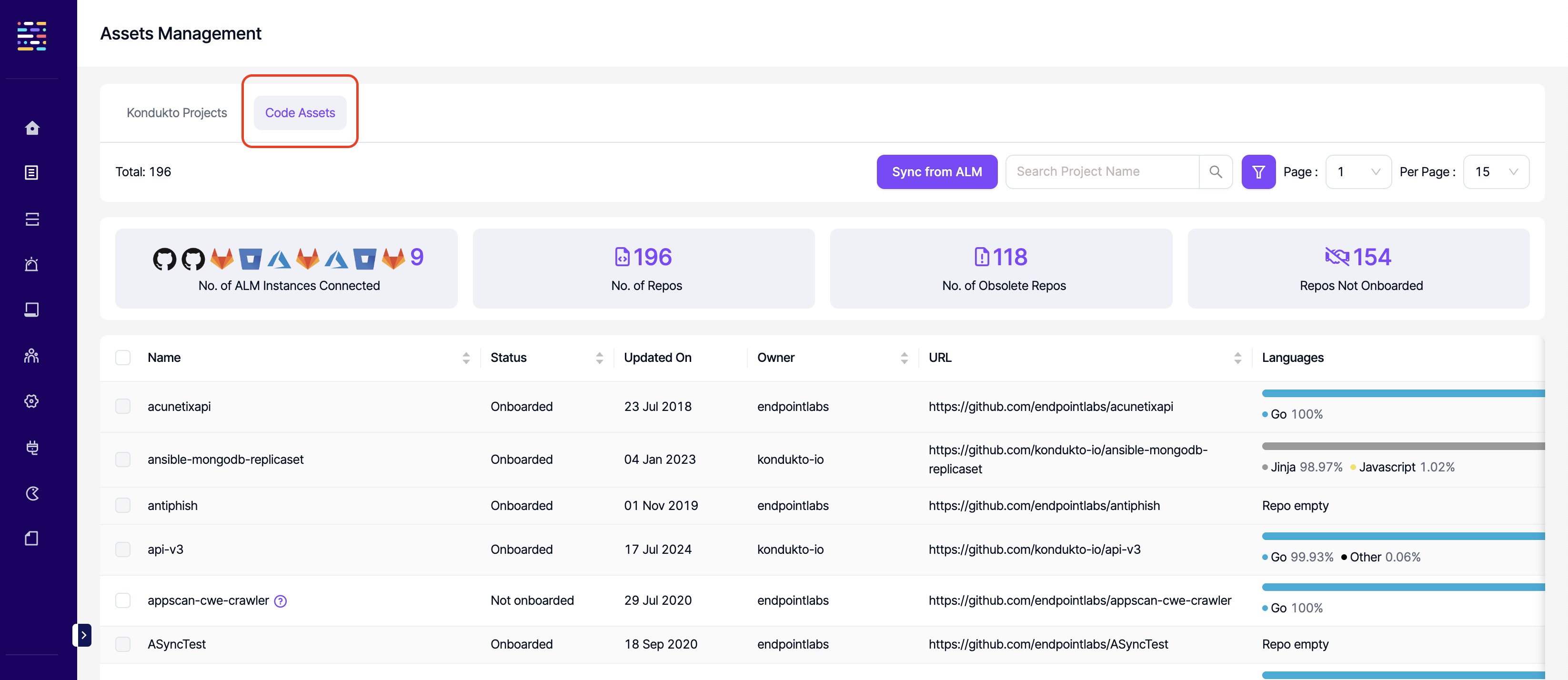
- Code Assets: Write: This permission controls the user's ability to create projects on the ALM tool as projects on Kondukto.
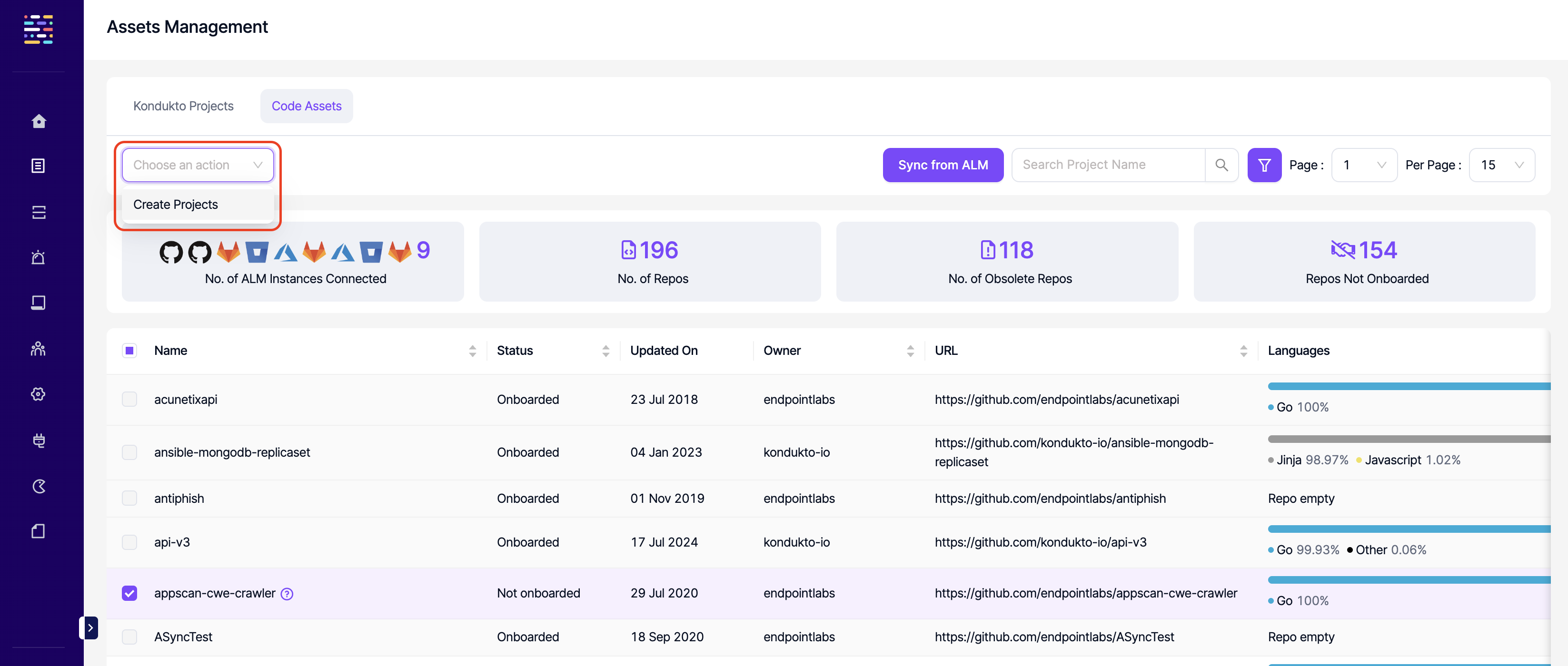
- Code Assets: Sync: This permission controls the user's ability to sync projects that are available on the ALM tools integrated with Kondukto.
SCANS PERMISSIONS
- Scans: Read: This permission controls the user's ability to view the Scans section on the side navigation menu and also the Scans tab in the projects and products the user has access to.
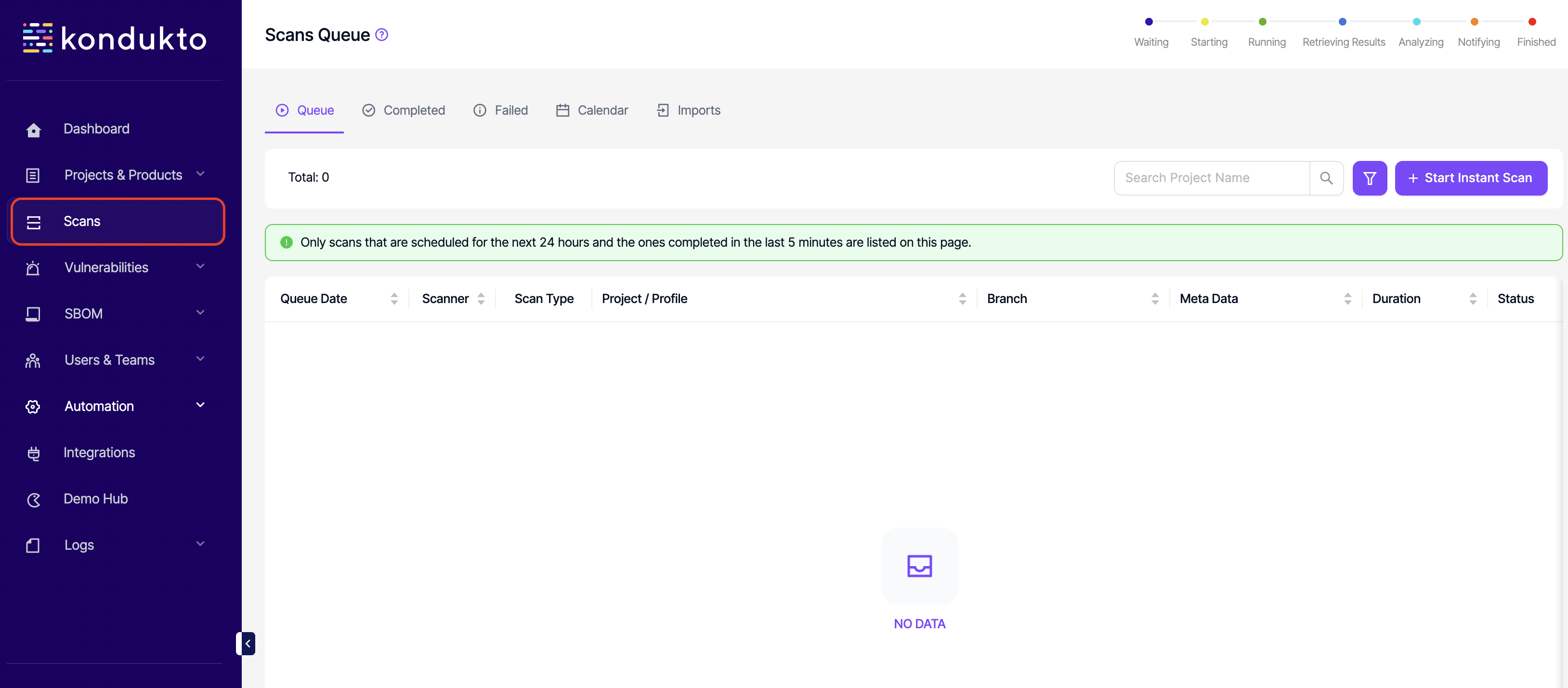
- Scans: Write: This permission controls the user's ability to kick off new scans or restart previous scans on the UI. The same permission also affects scanning permissions at a project level.
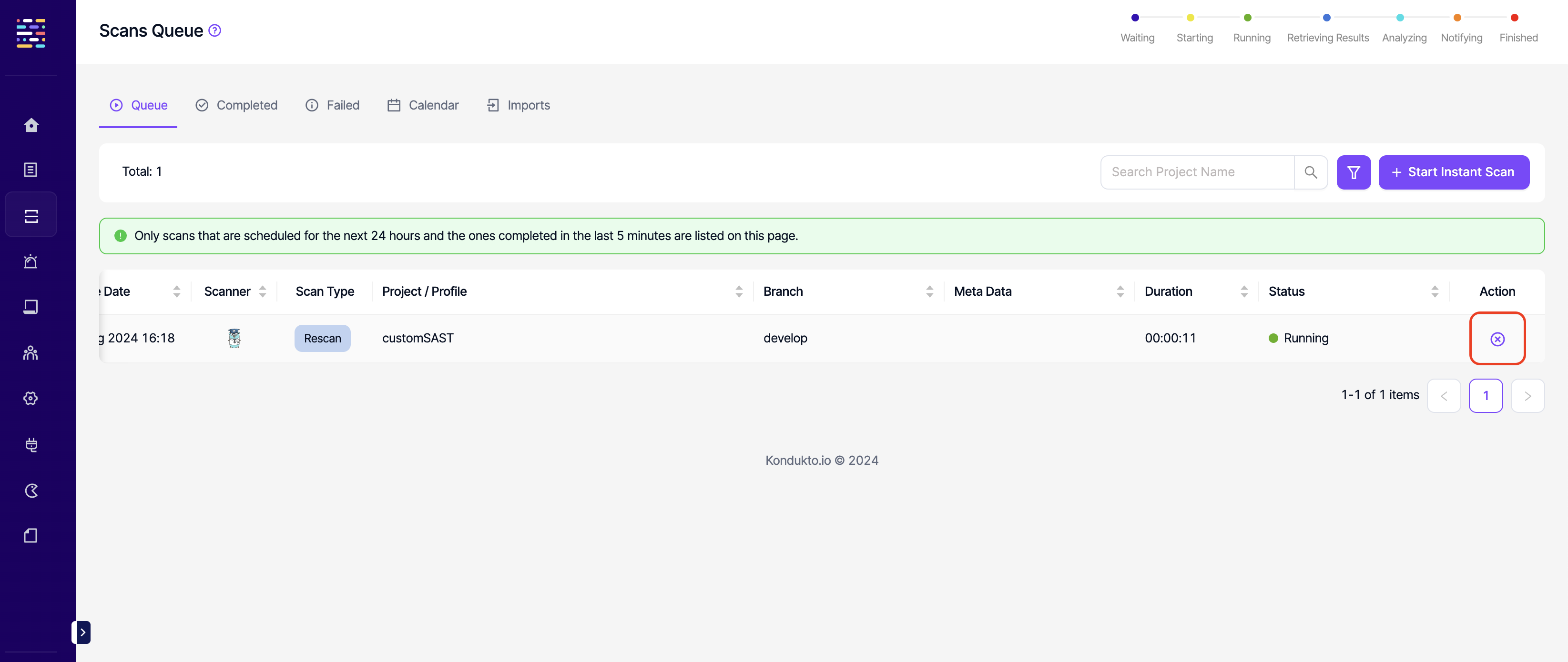
- Scans: Delete: This permission controls the user's ability to cancel scans that are running on Kondukto.
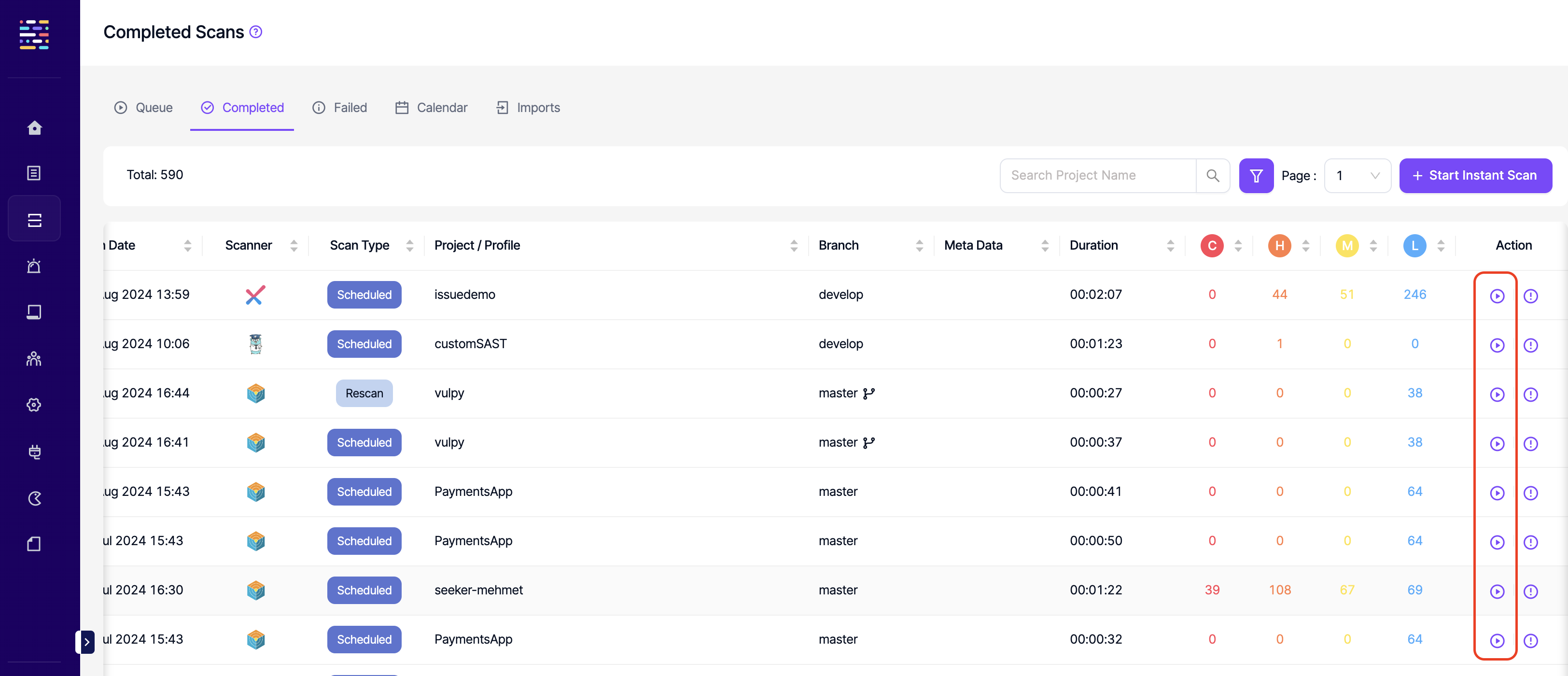
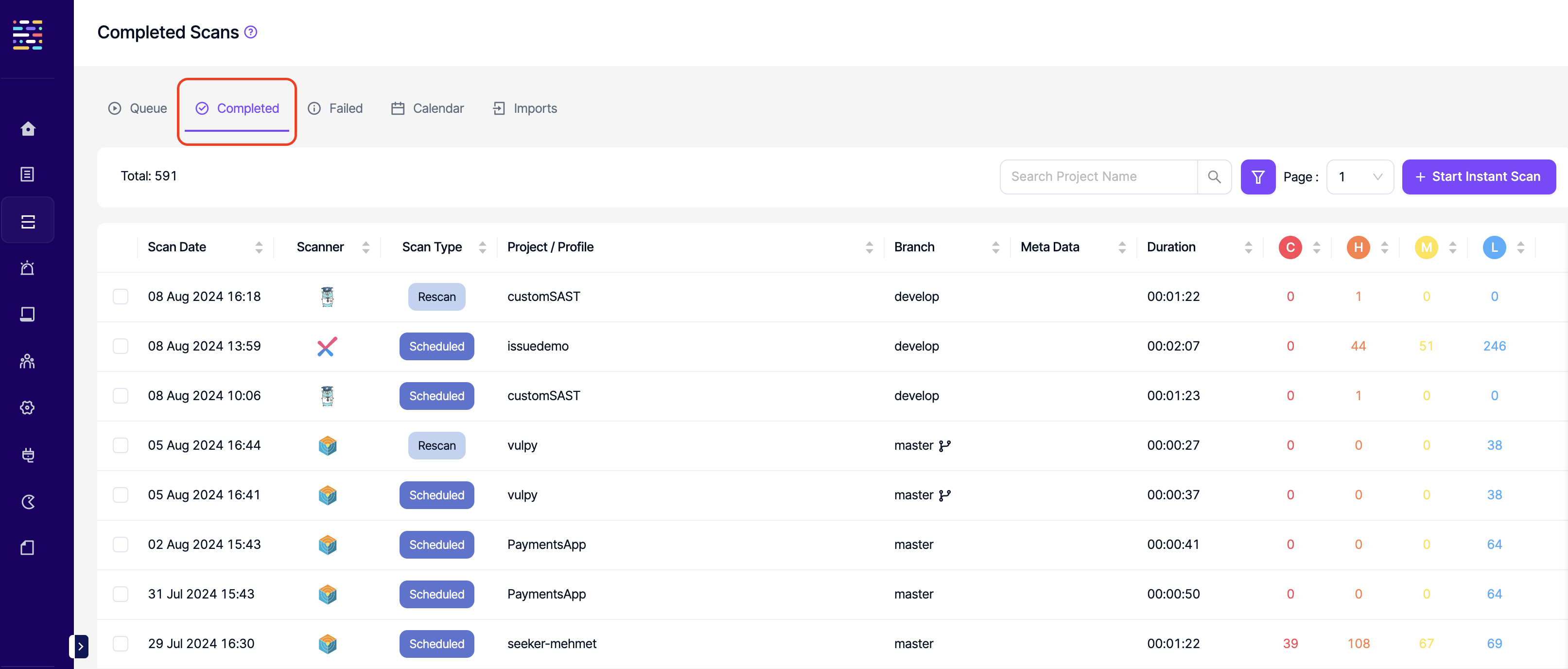
- Completed Scans: Read: This permission controls the user's ability to view Complete tab under Scans. The same permission also affects viewing completed scans at a project level.
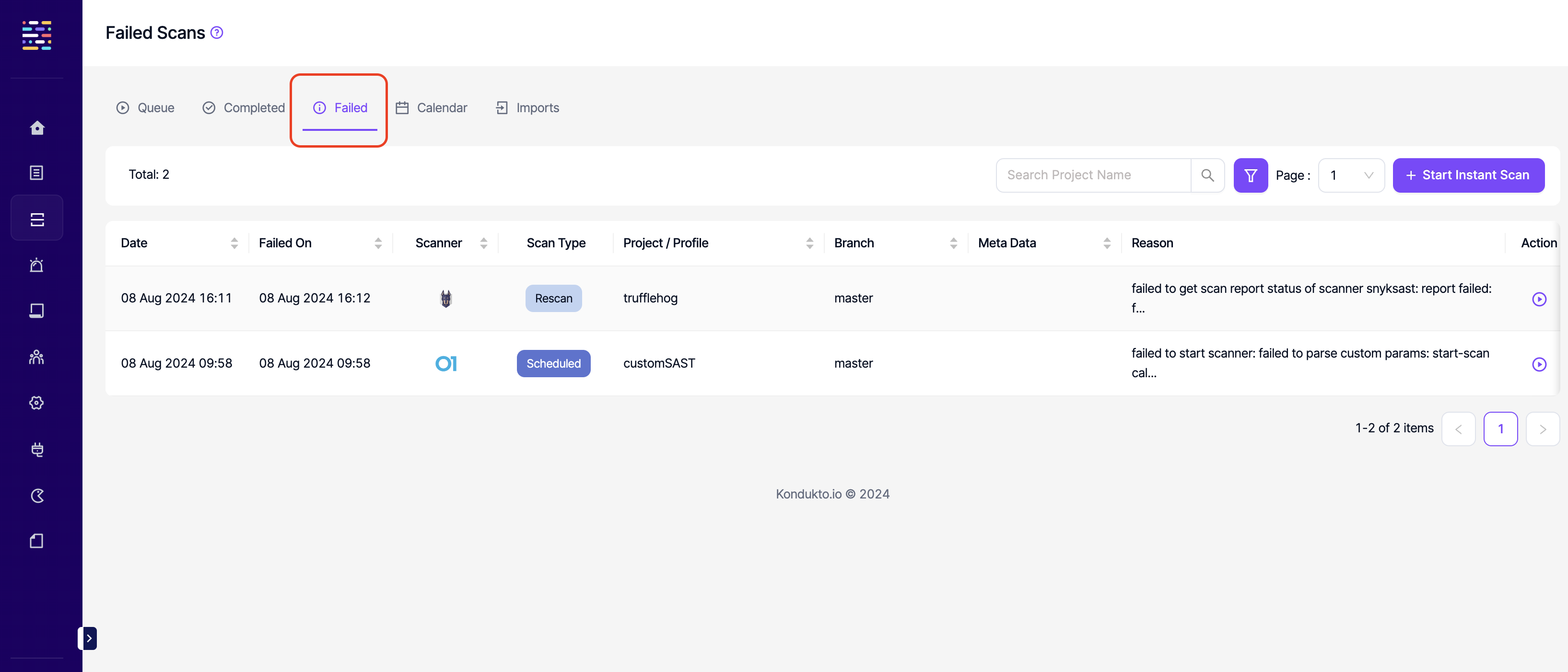
- Failed Scans: Read: This permission controls the user's ability to view Failed tab under Scans. The same permission also affects viewing failed scans at a project level.
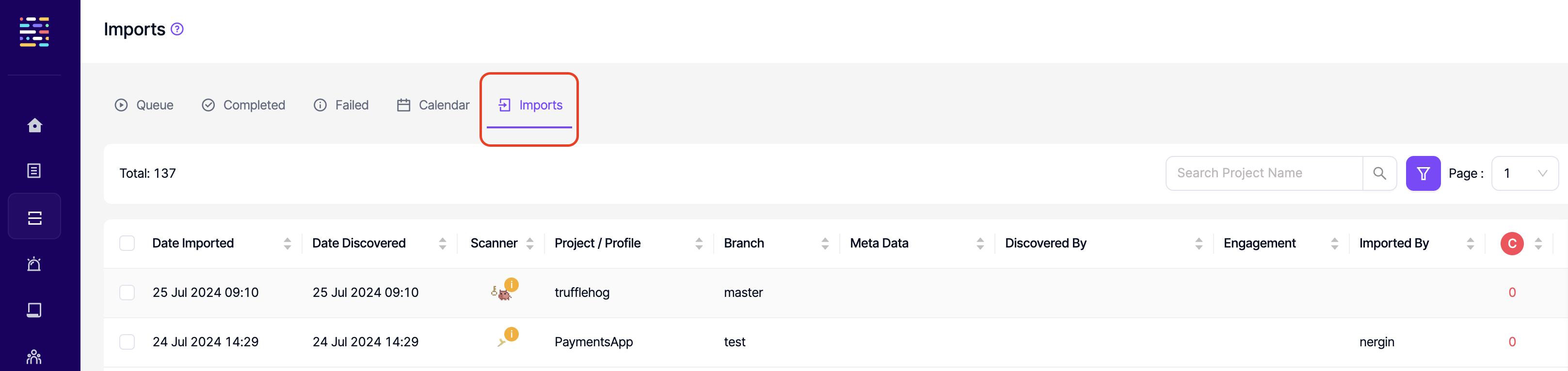
- Imports: Read: This permission controls the user's ability to view Imports tab under Scans. The same permission also affects viewing imports at a project level.
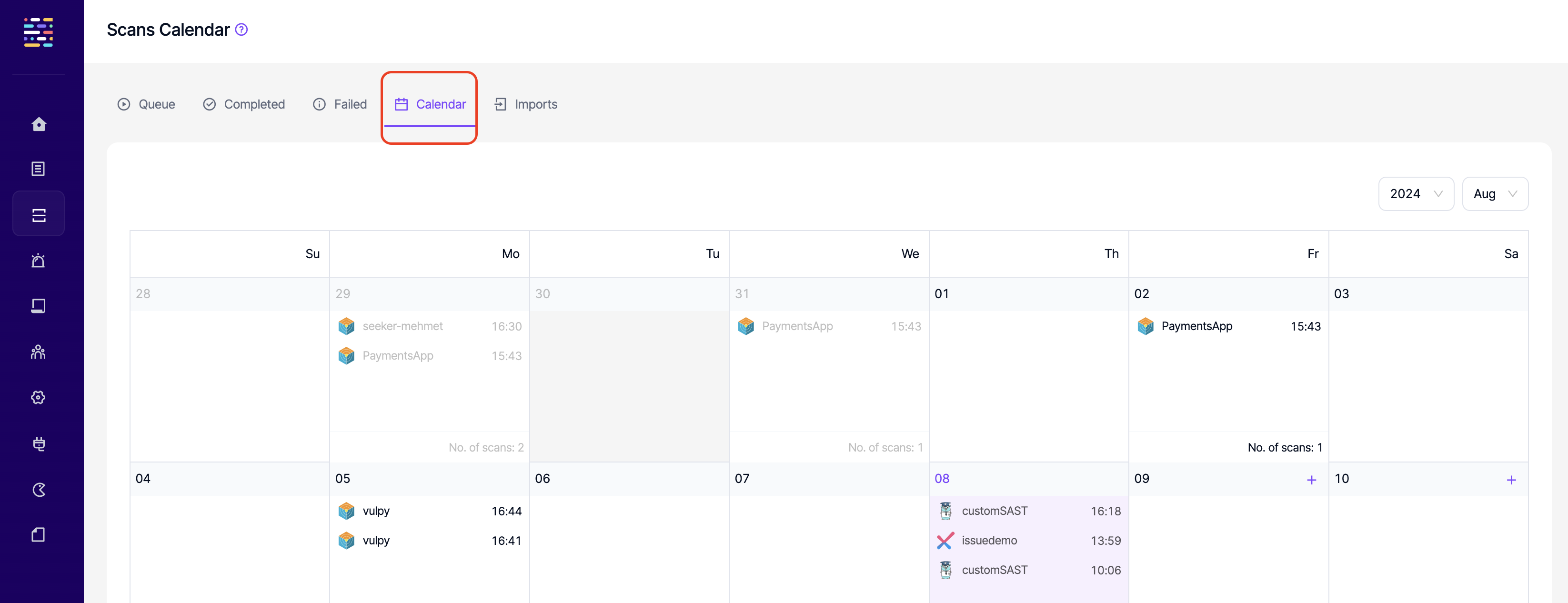
- Calendar: Read: This permission controls the user's ability to view Calendar tab under Scans.
VULNERABILITIES PERMISSIONS
- Vulnerabilities: Read: This permission controls the user's ability to view the Vulnerabilities section on the side navigation menu. The same permission also affects viewing vulnerabilities at a project and product level.
- Vulnerabilities: Add: This permission controls the user's ability to import vulnerabilities to projects.
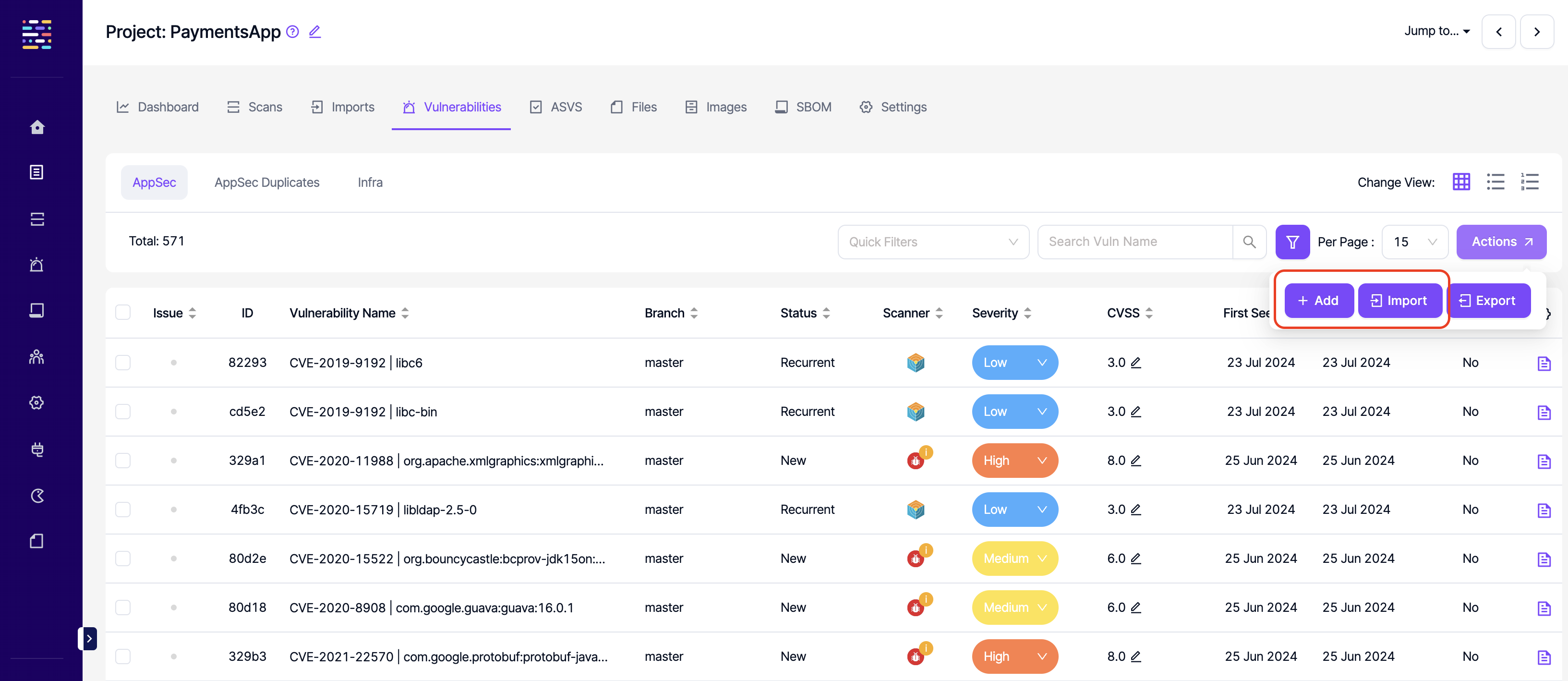
- Vulnerabilities: Write: This permission controls the user's ability to edit vulnerabilities (change severity or CVSS score).
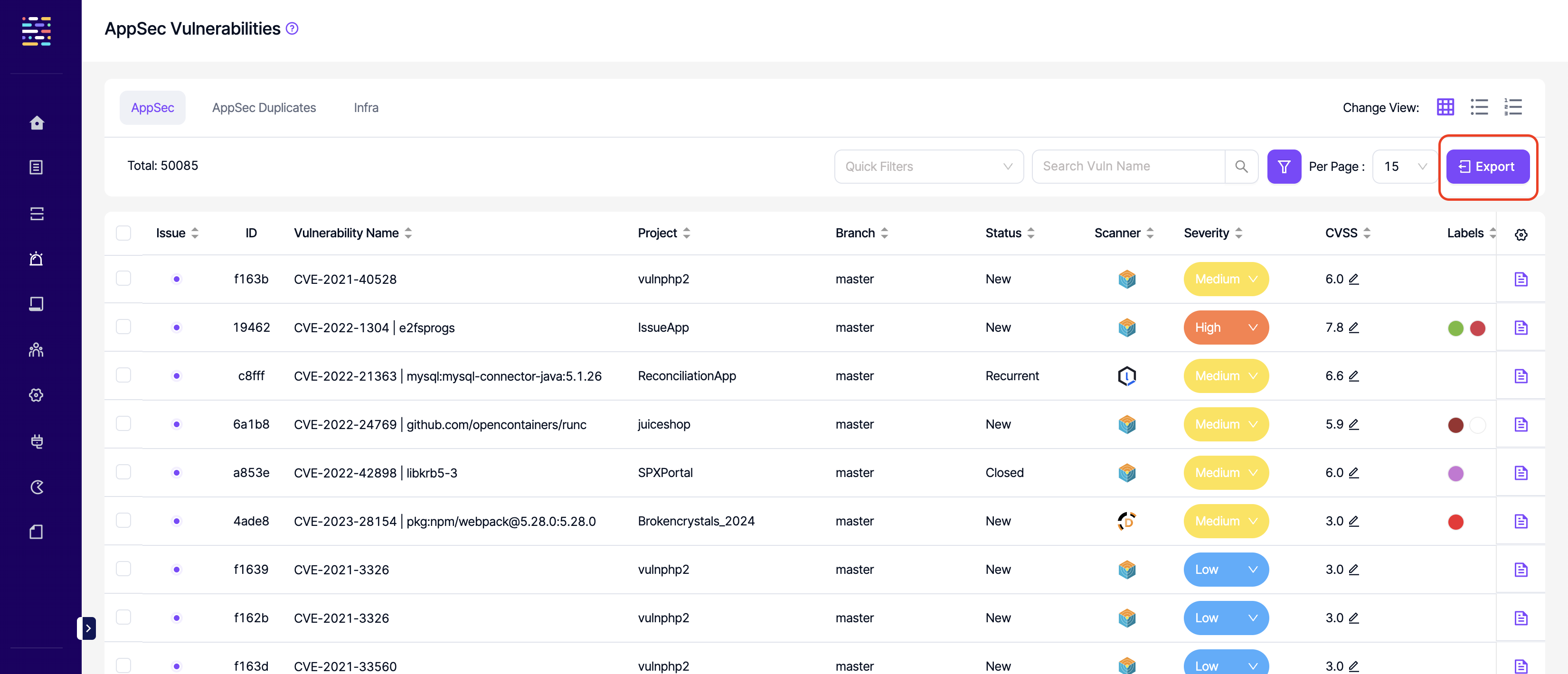
- Vulnerabilities: Export: This permission controls the user's ability to export vulnerabilities at a project, product or global level.
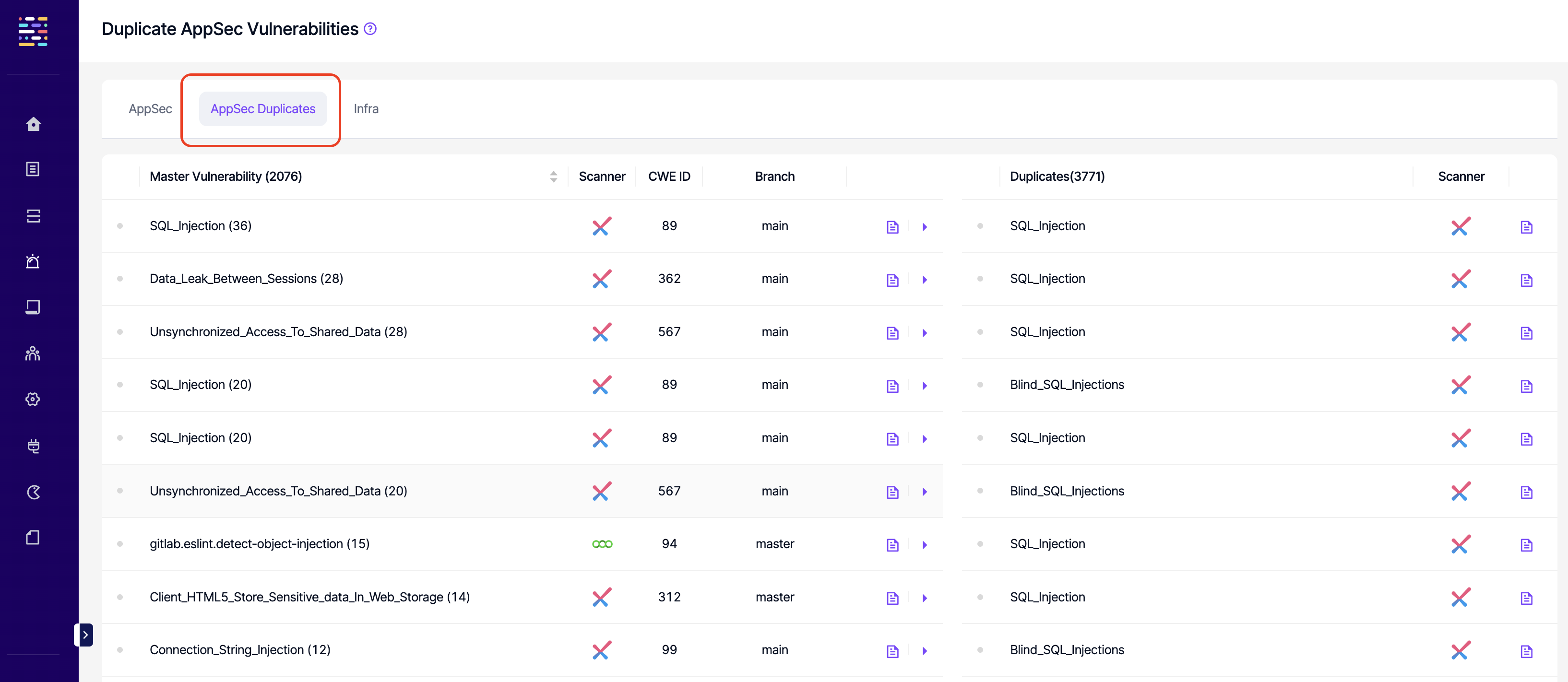
- Deduped Vulns.: Read: This permission controls the user's ability to view AppSec Duplicates tab under vulnerabilities at a project and global level.
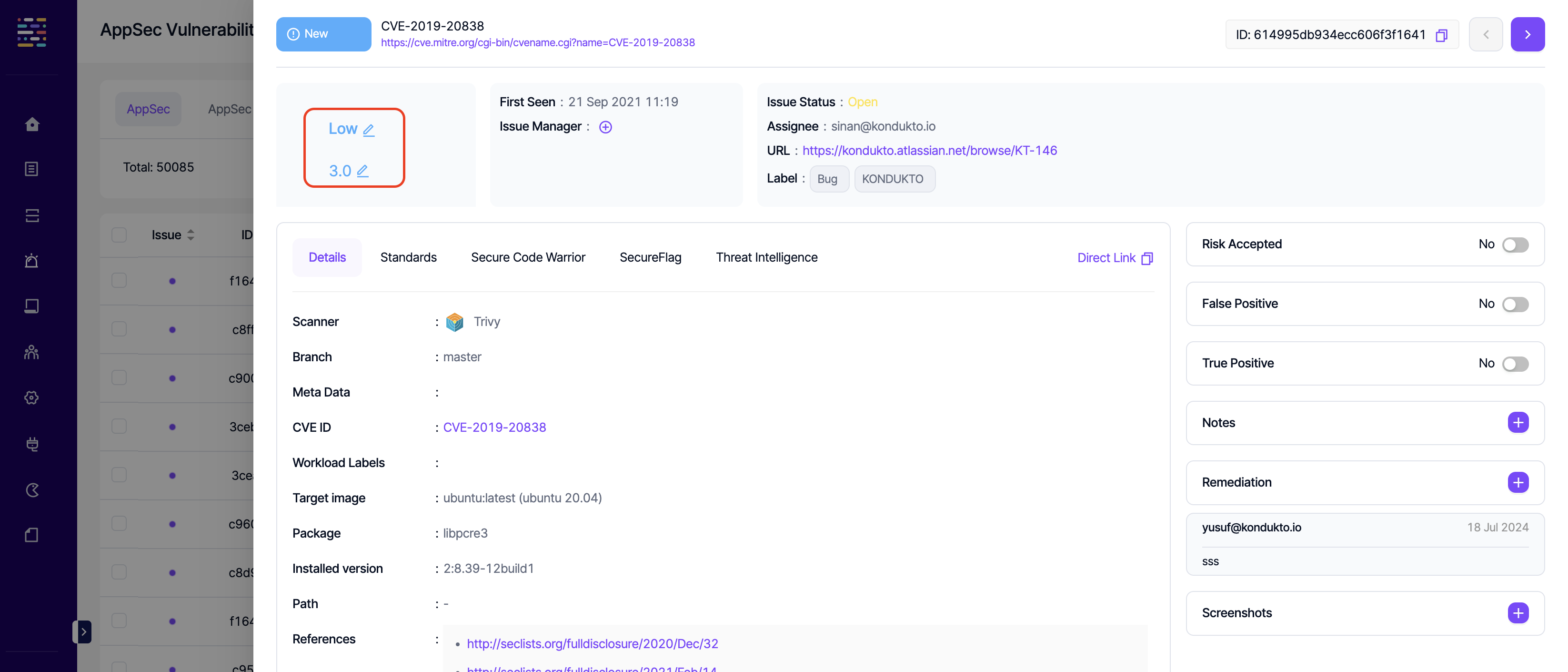
- Add Notes: Write: This permission controls the user's ability to kick off new scans or restart previous scans on the UI. The same permission also affects scanning permissions at a project level.
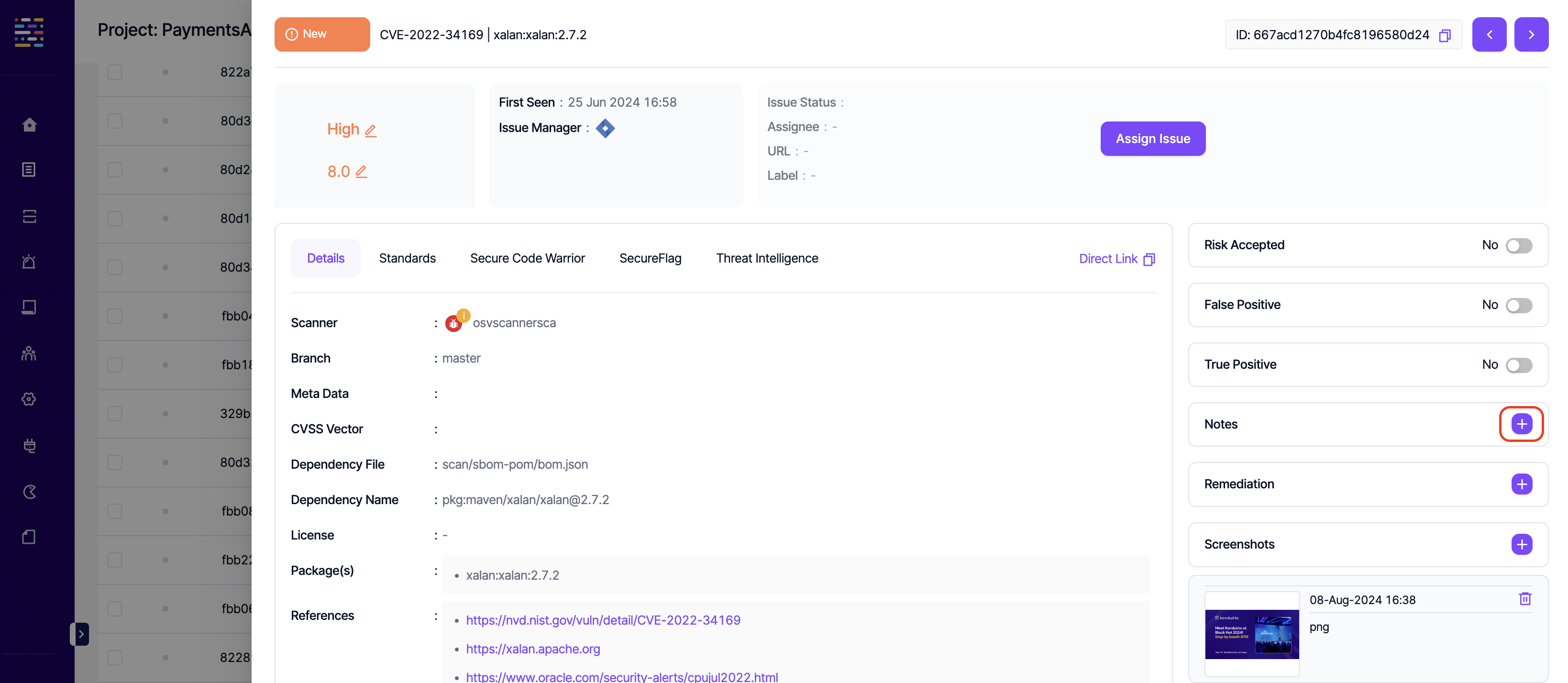
- Assign Issue: Write: This permission controls the user's ability to assign issues for vulnerabilities on the issue managers.
- Screenshot: Read: This permission controls the user's ability to view screenshots added to a vulnerability.
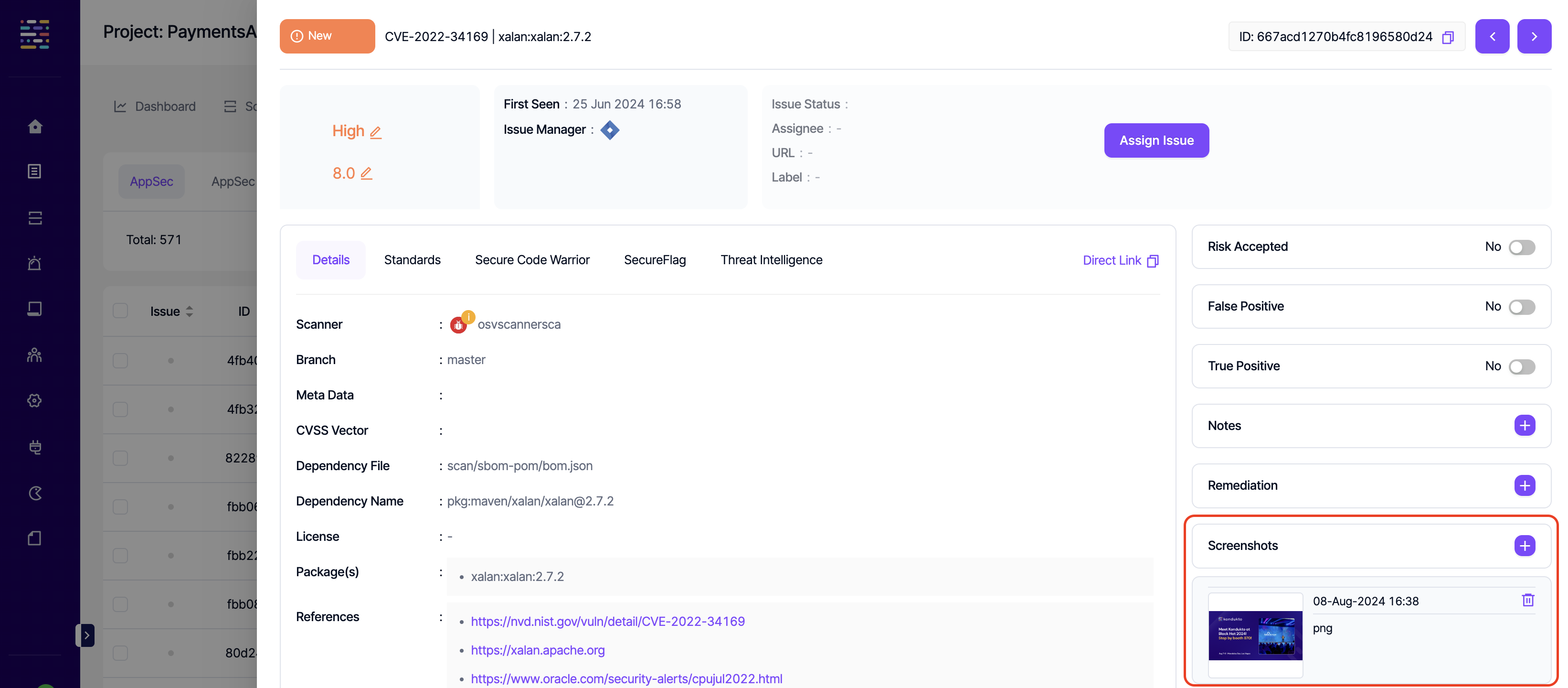
- Screenshot: Write: This permission controls the user's ability to add screenshots to a vulnerability.
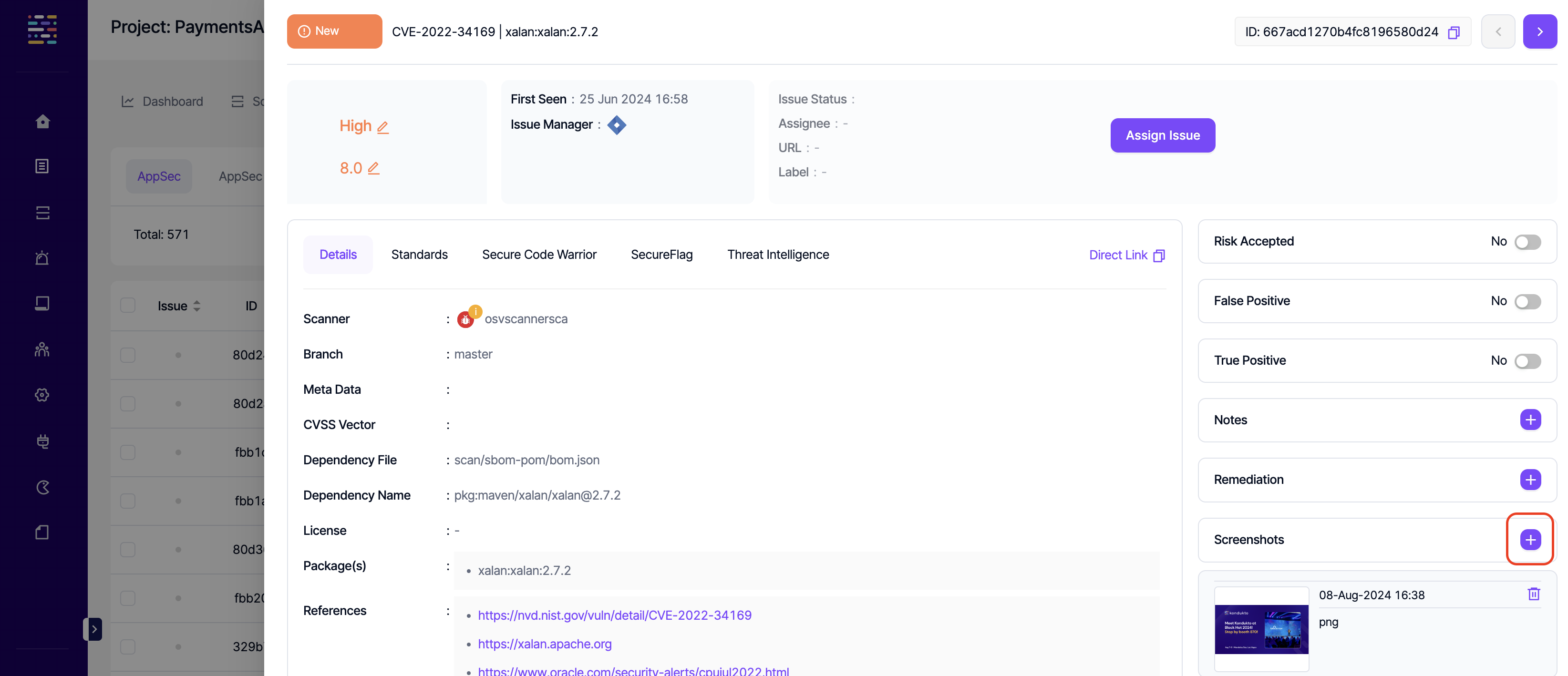
- Screenshot: Delete: This permission controls the user's ability to delete screenshots of a vulnerability.
SBOM PERMISSIONS
- SBOM: Read: This permission controls the user's ability to view the SBOM section on the side navigation menu. The same permission also affects viewing SBOM tab at a project and product level.
- SBOM Components: Read: This permission controls the user's ability to view the SBOM Components section on the side navigation menu. The same permission also affects viewing SBOM components at a project and product level.
- SBOM Components: Export: This permission controls the user's ability to export SBOM components.
USERS & TEAMS & ROLES PERMISSIONS
- Users: Read: This permission controls the user's ability to view User section on the side navigation menu.
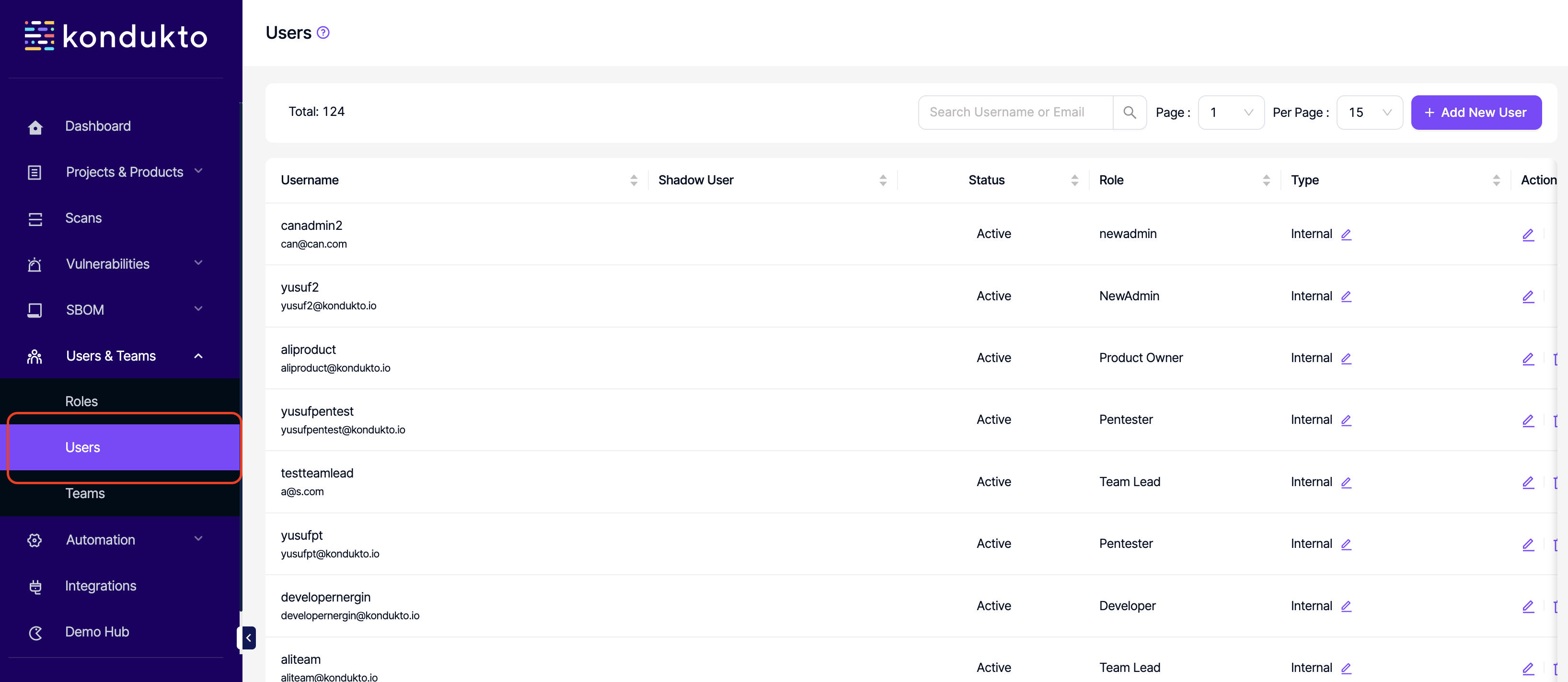
- Users: Write: This permission controls the user's ability to add new users to the platform and edit existing ones.
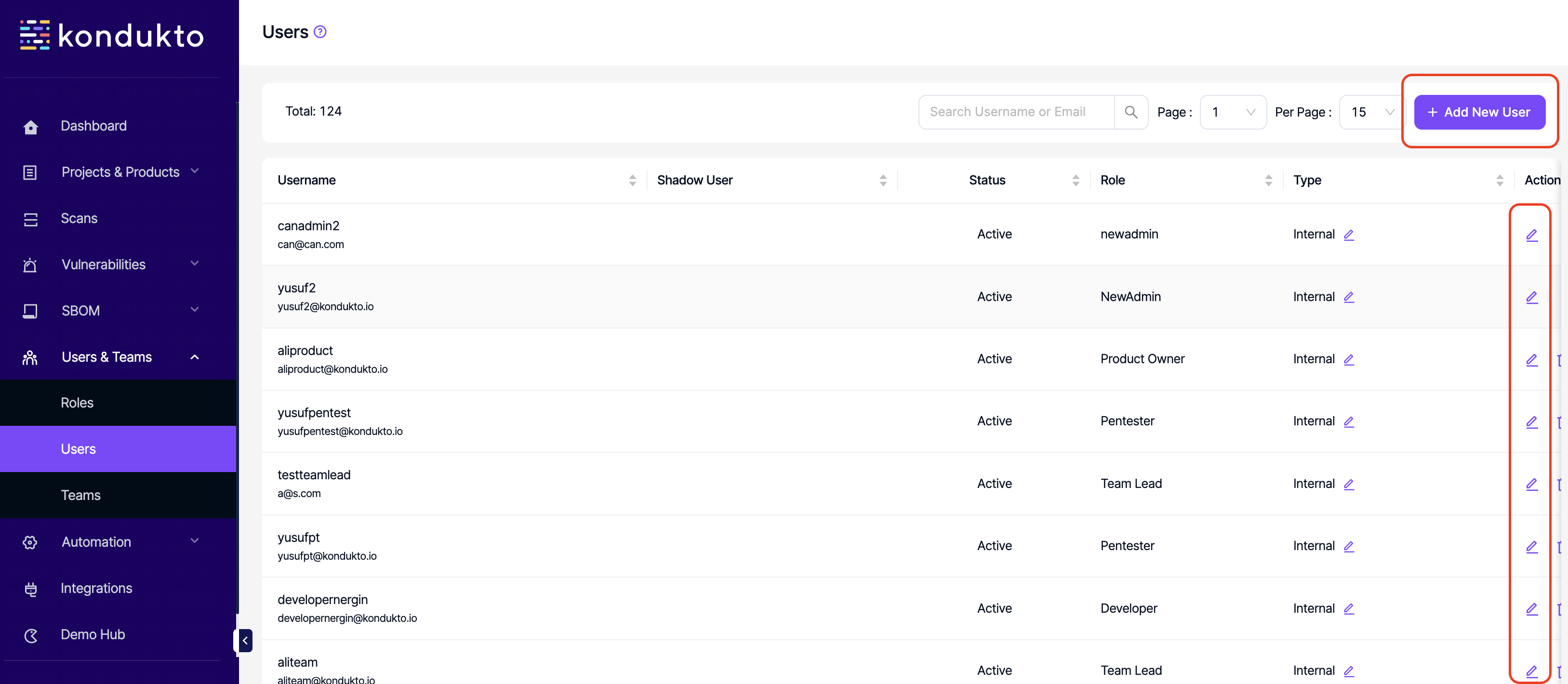
- Users: Delete: This permission controls the user's ability to delete users.
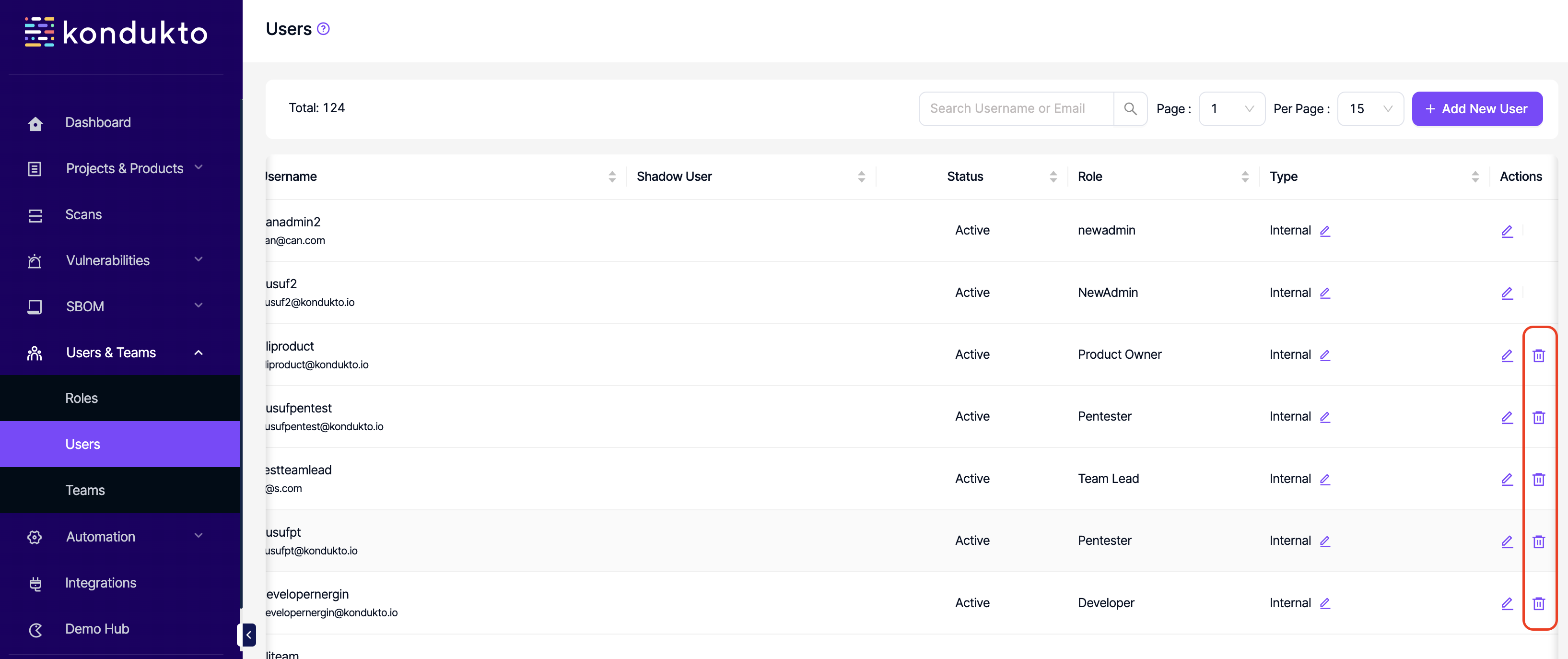
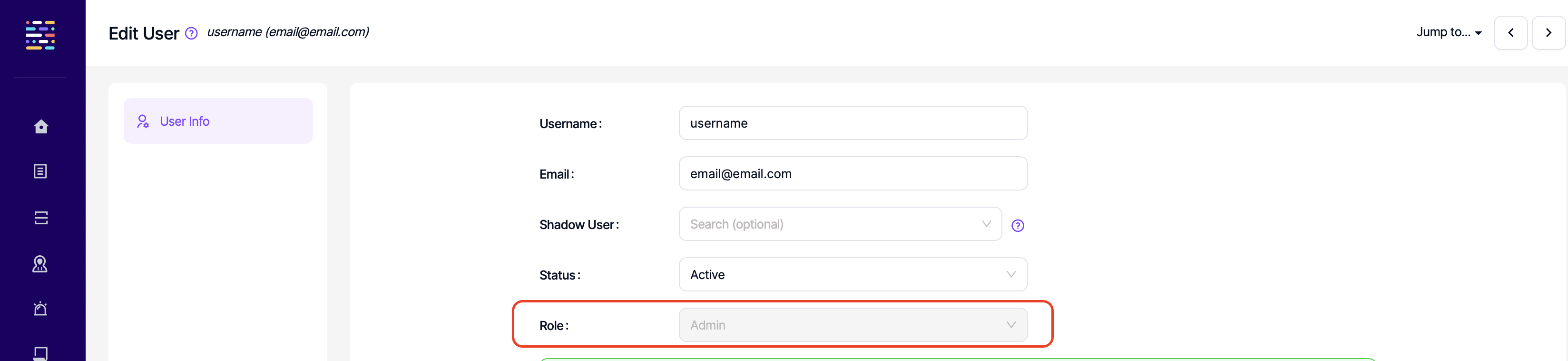
- Users: Change Role: This permission controls the user's ability to edit roles of other users.
- User Mgmt.: Read: This permission controls the user's ability to view teams, projects and products that are assigned to a user.
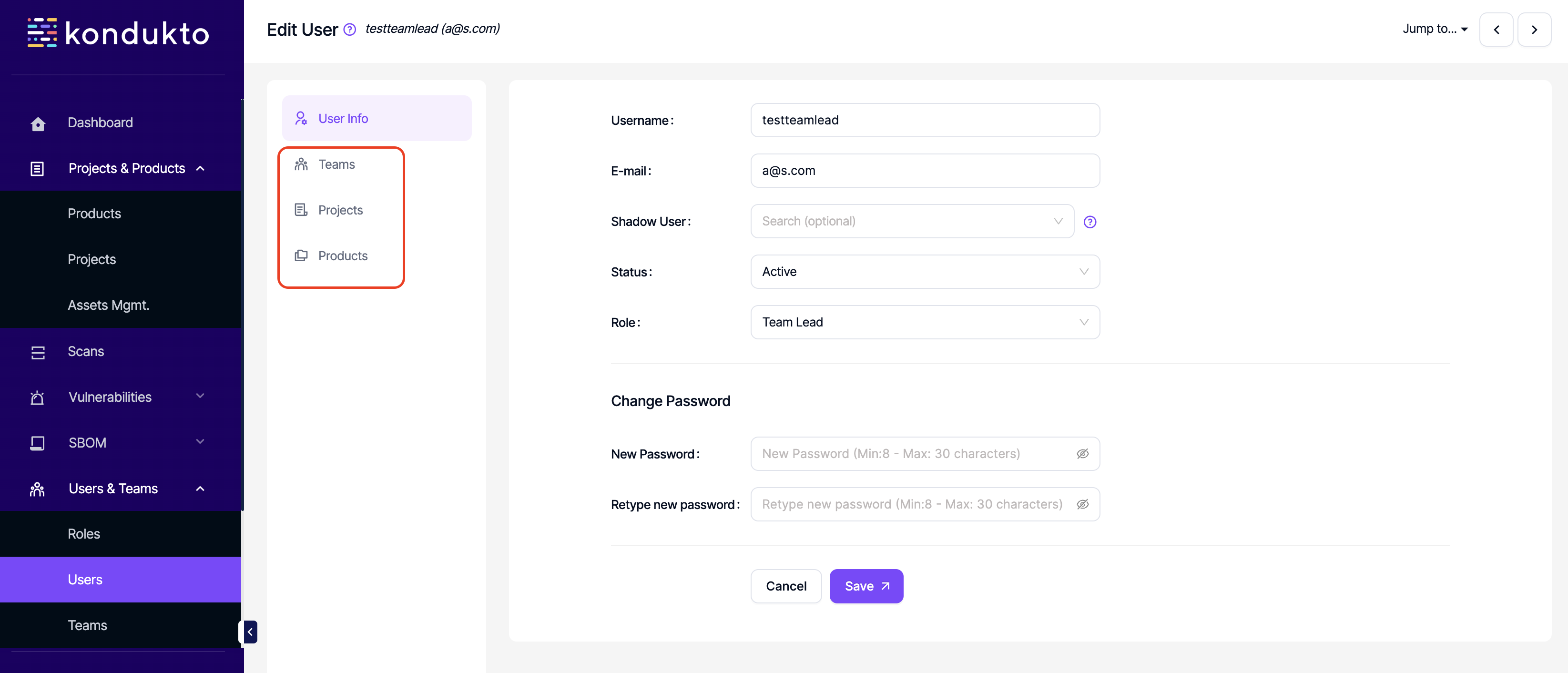
- User Mgmt.: Write: This permission controls the user's ability to assign projects and products to a user under Users section.
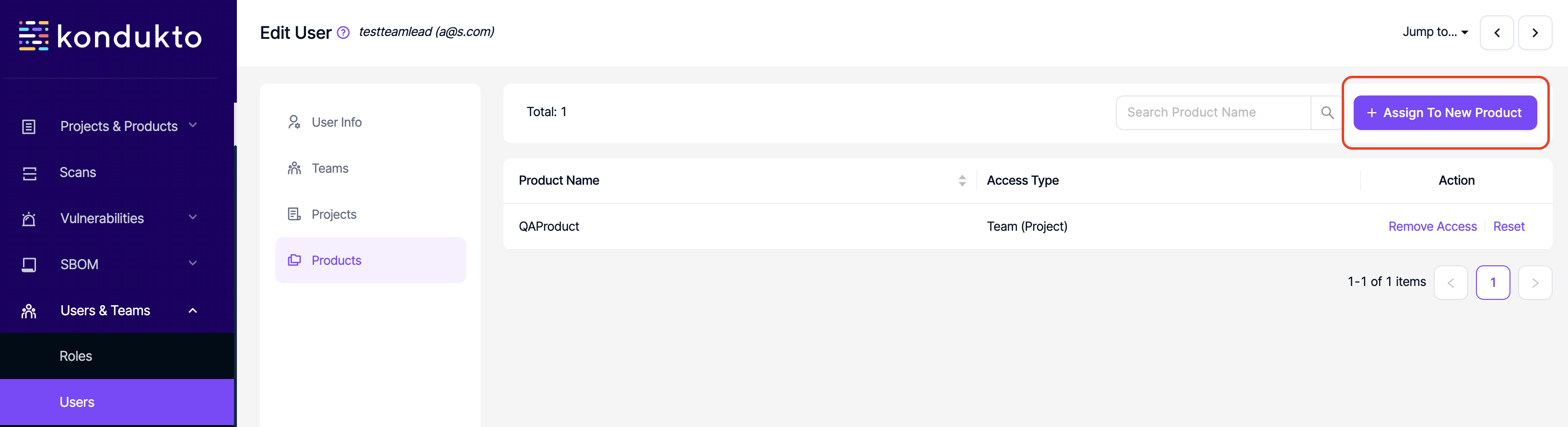
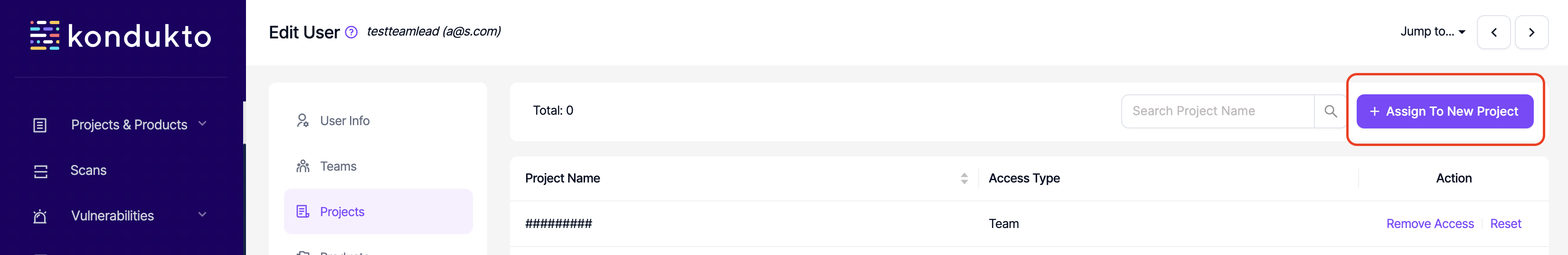
- Teams: Read: This permission controls the user's ability to view Teams section on the side navigation menu.
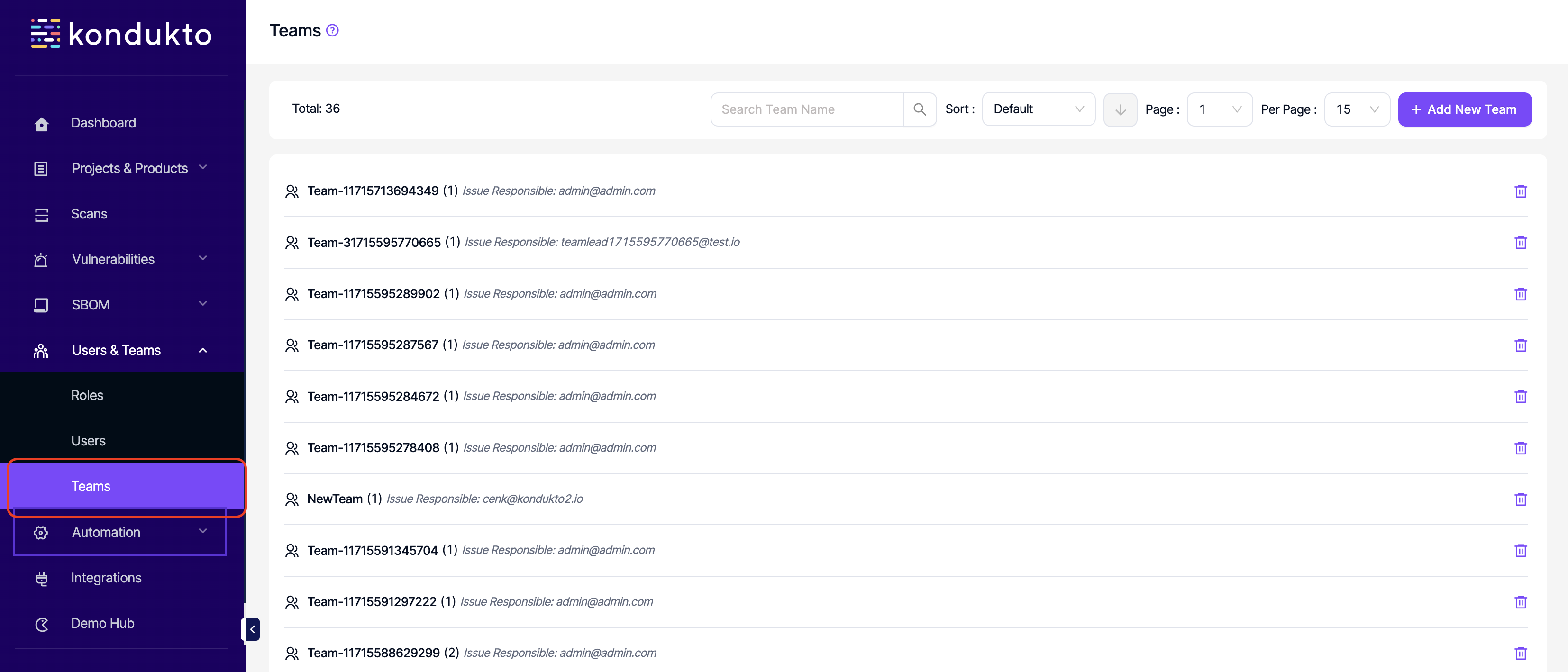
- Teams: Write: This permission controls the user's ability to add new teams and to add new members to teams.
- Teams: Delete: This permission controls the user's ability to delete teams and delete team members from teams.
- Roles: Read: This permission controls the user's ability to view Roles section on the side navigation menu.
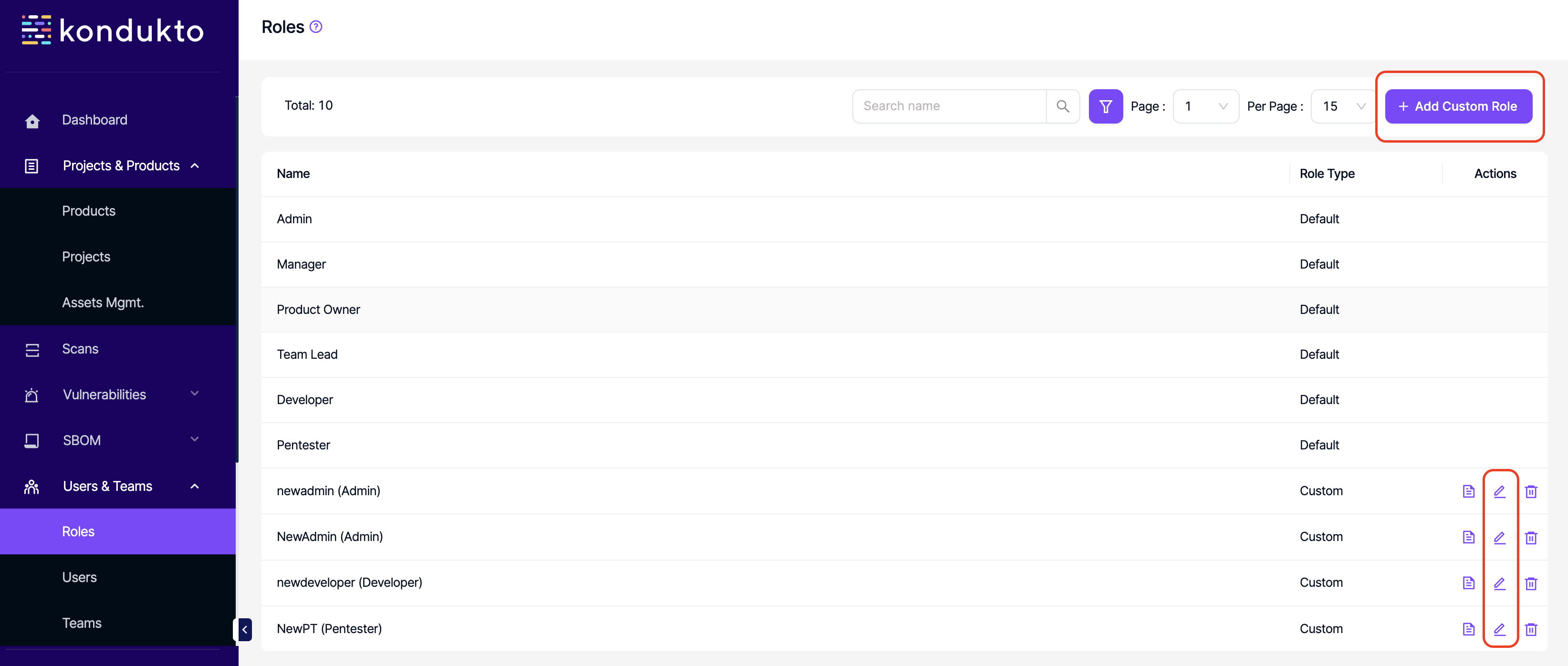
- Roles: Write: This permission controls the user's ability to create new roles and edit existing custom roles.
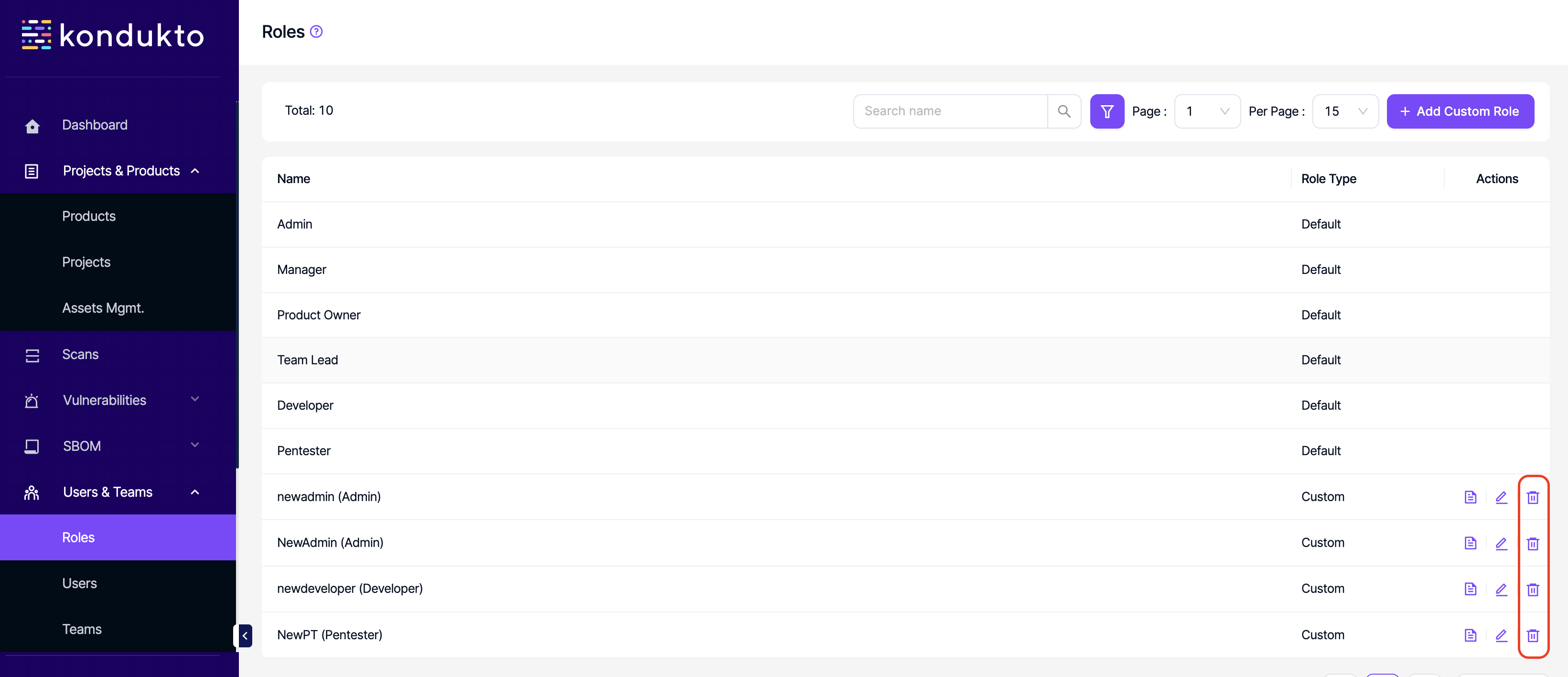
- Roles: Delete: This permission controls the user's ability to delete custom roles.
AUTOMATION PERMISSIONS
- Automation Setup: Read: This permission controls the user's ability to view Automation Setup section under Automation.
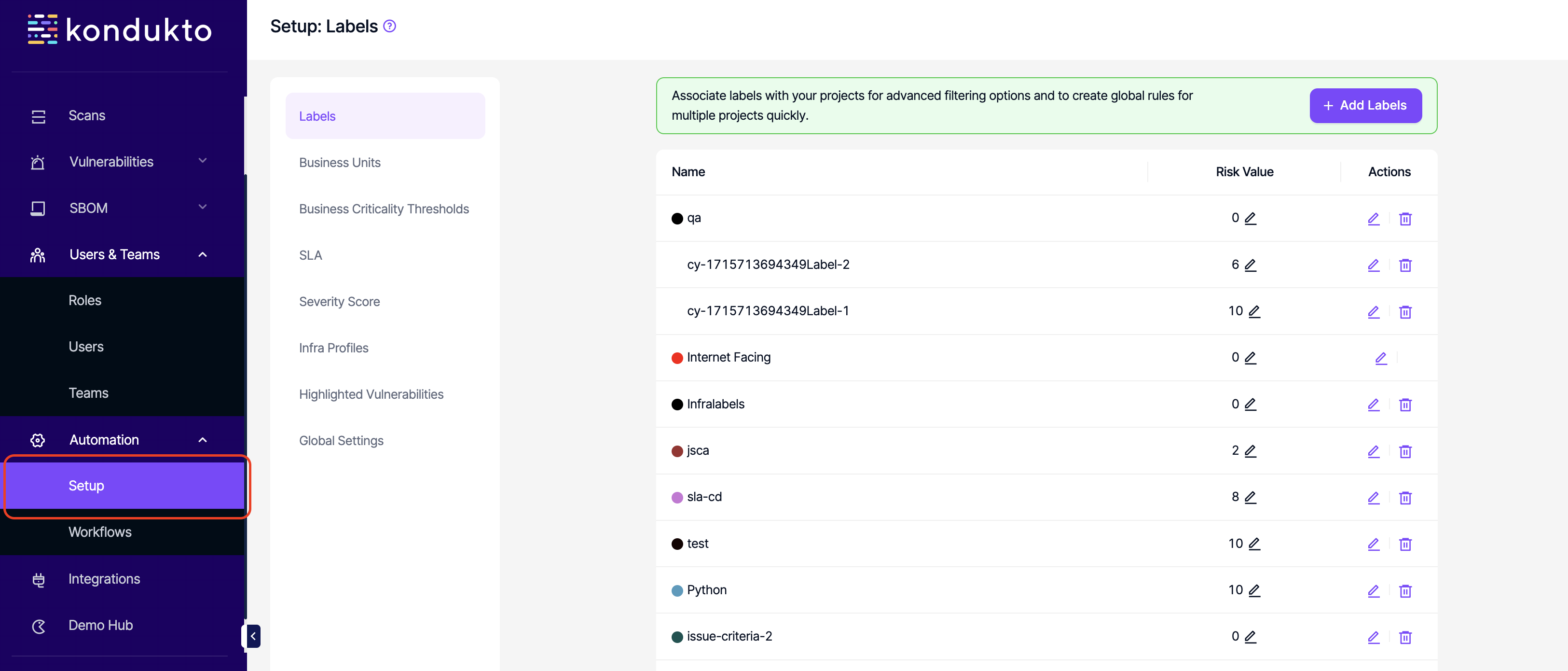
- Automation Setup: Write: This permission controls the user's ability to add or edit labels, business units, business criticality thresholds, SLA, severity score, infra profiles and highlighted vulnerabilities.
- Automation Setup: Delete: This permission controls the user's ability to delete labels, business units, SLA, infra profiles and highlighted vulnerabilities.
- Automation Workflows: Read: This permission controls the user's ability to view Automation Workflows section under Automation.
- Automation Workflows: Write: This permission controls the user's ability to add or edit automation rules and reports.
- Automation Workflows: Delete: This permission controls the user's ability to delete automation rules and reports.
- Remediation DB: Read: This permission controls the user's ability to view Remediation DB under Automation Rules.
- Remediation DB: Write: This permission controls the user's ability to add or edit entries under Remediation DB.
- Remediation DB: Delete: This permission controls the user's ability to delete entries under Remediation DB.
INTEGRATIONS PERMISSIONS
- Integrations: Read: This permission controls the user's ability to view Integrations on the side navigation menu.
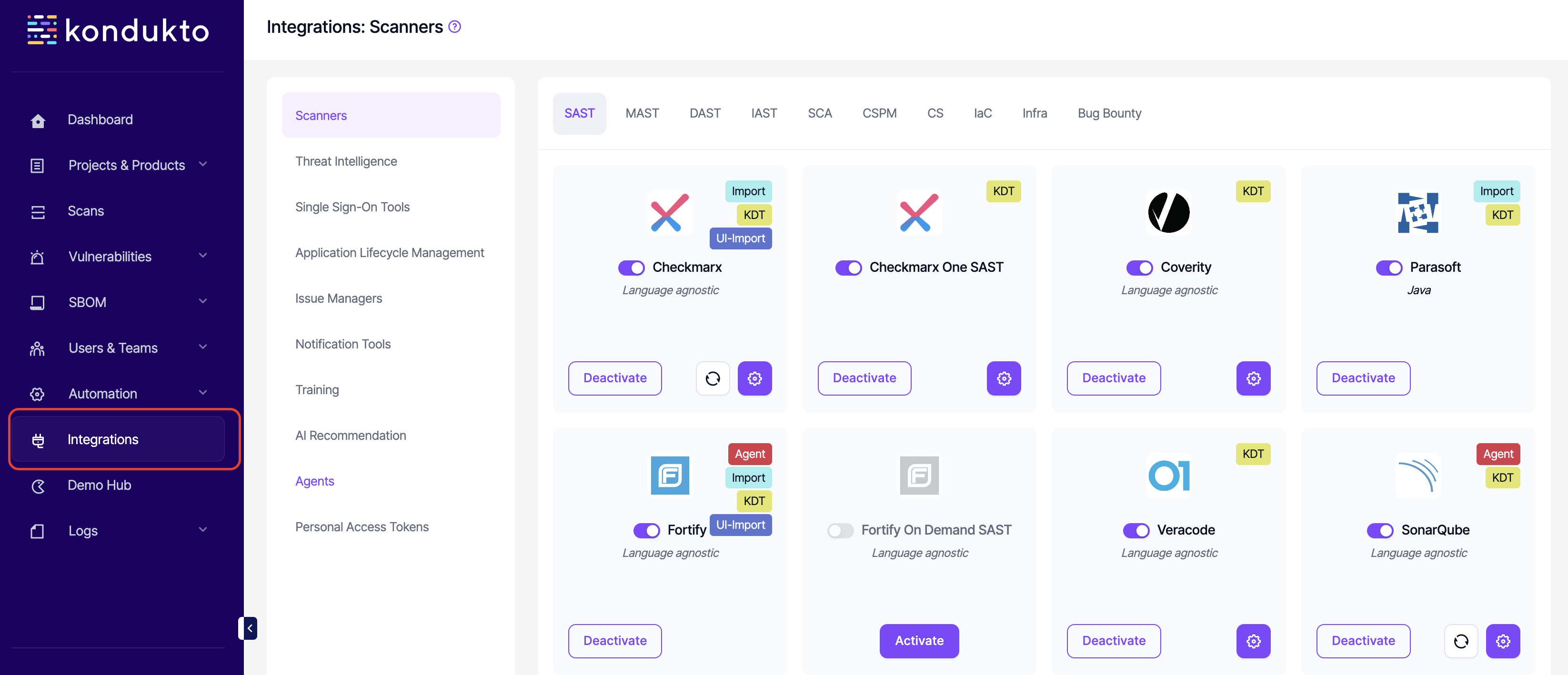
- Integrations: Write: This permission controls the user's ability to edit existing integrations and add custom integrations.
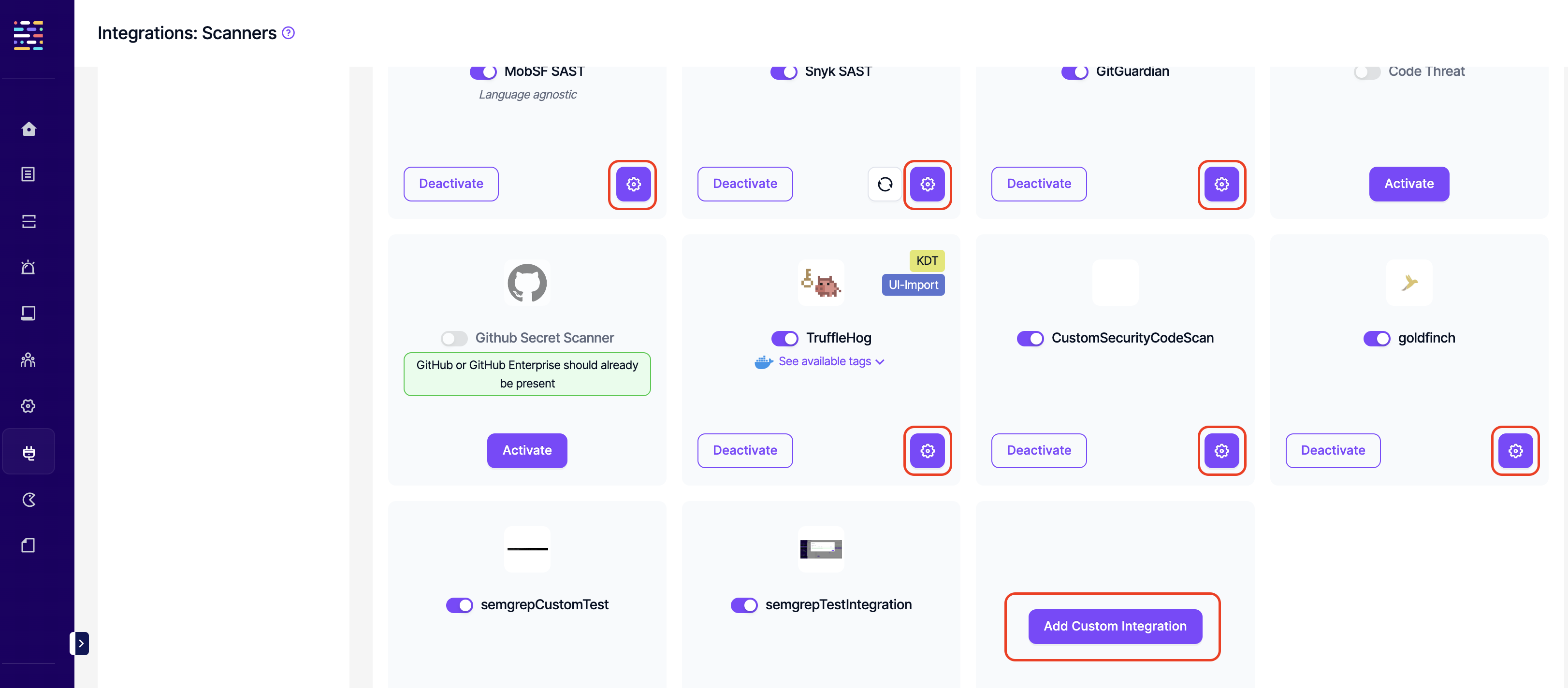
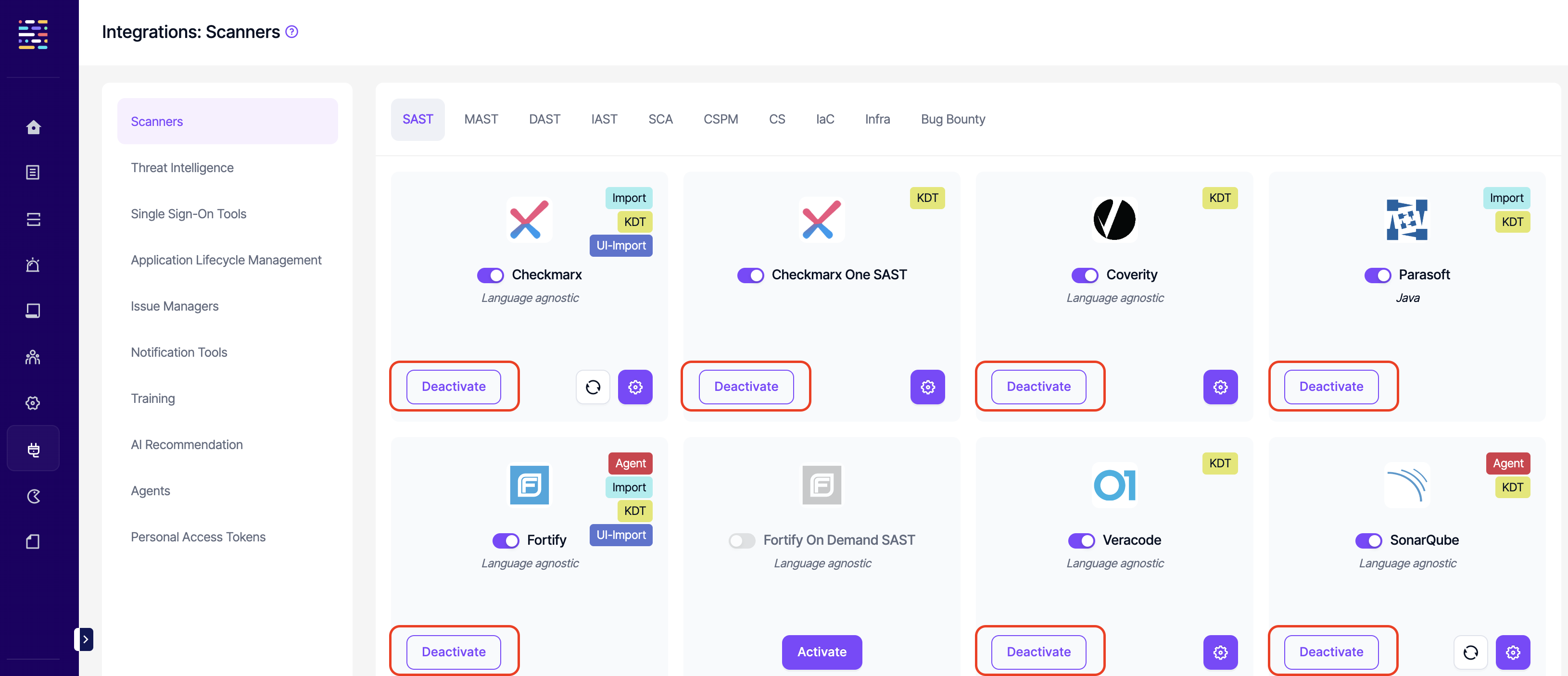
- Integrations: Delete: This permission controls the user's ability to deactivate existing integrations.
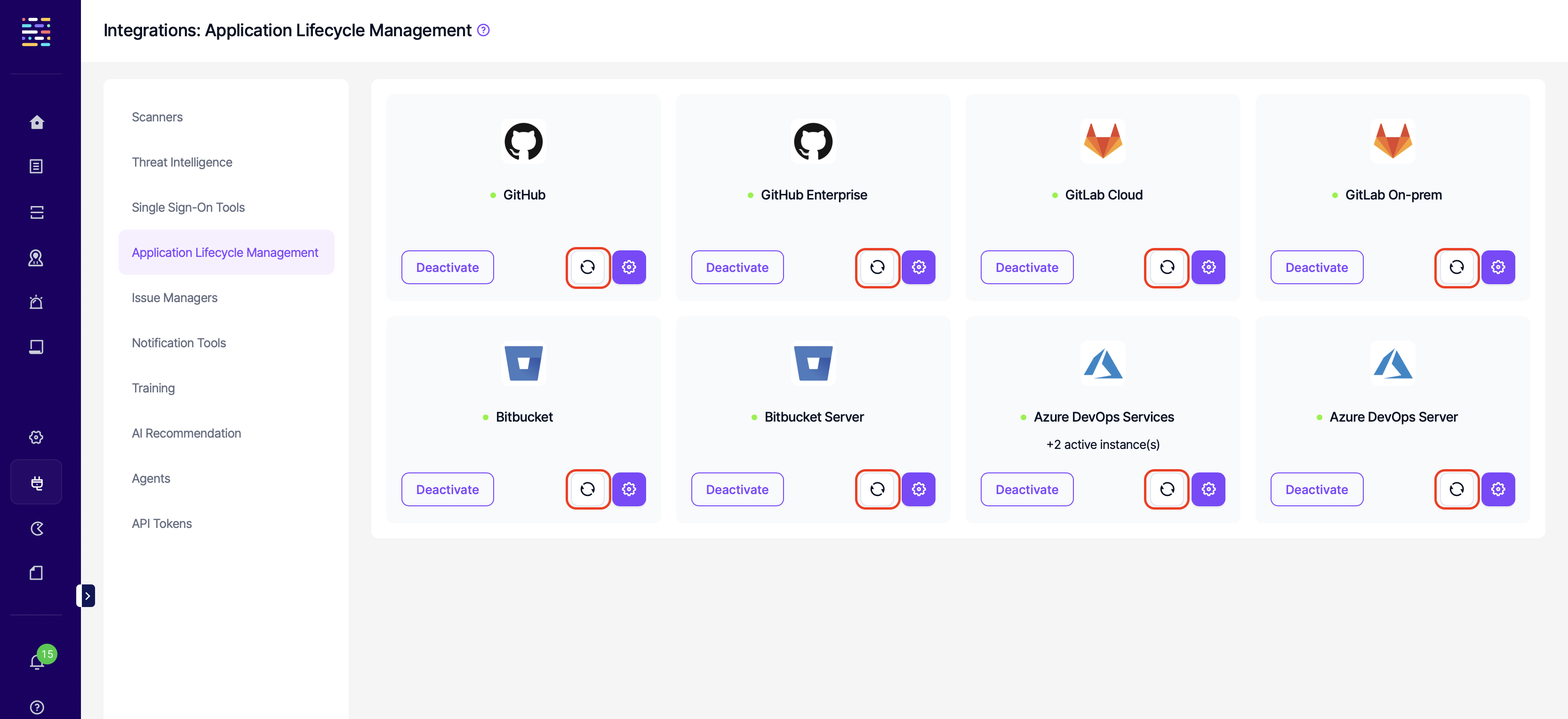
- Integrations: Application Lifecycle Management: This permission controls the user's ability to fetch projects from the ALM tools under the Integrations menu.
SUPPRESSION PERMISSIONS
- FP Requests: Read: This permission controls the user's ability to view FP requests. This permission can not be removed unless all other FP requests related permissions are also removed.
- FP Requests: Write: This permission controls the user's ability to submit FP requests.
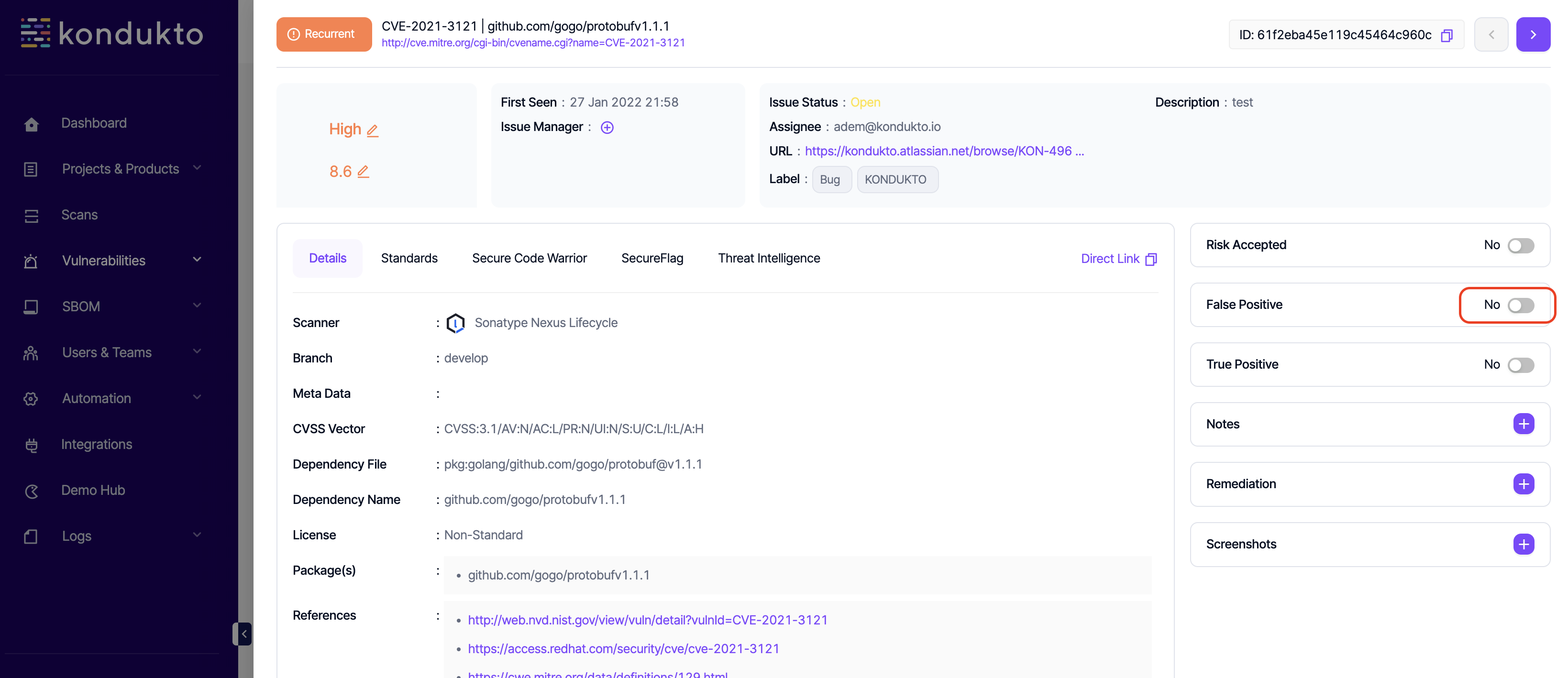
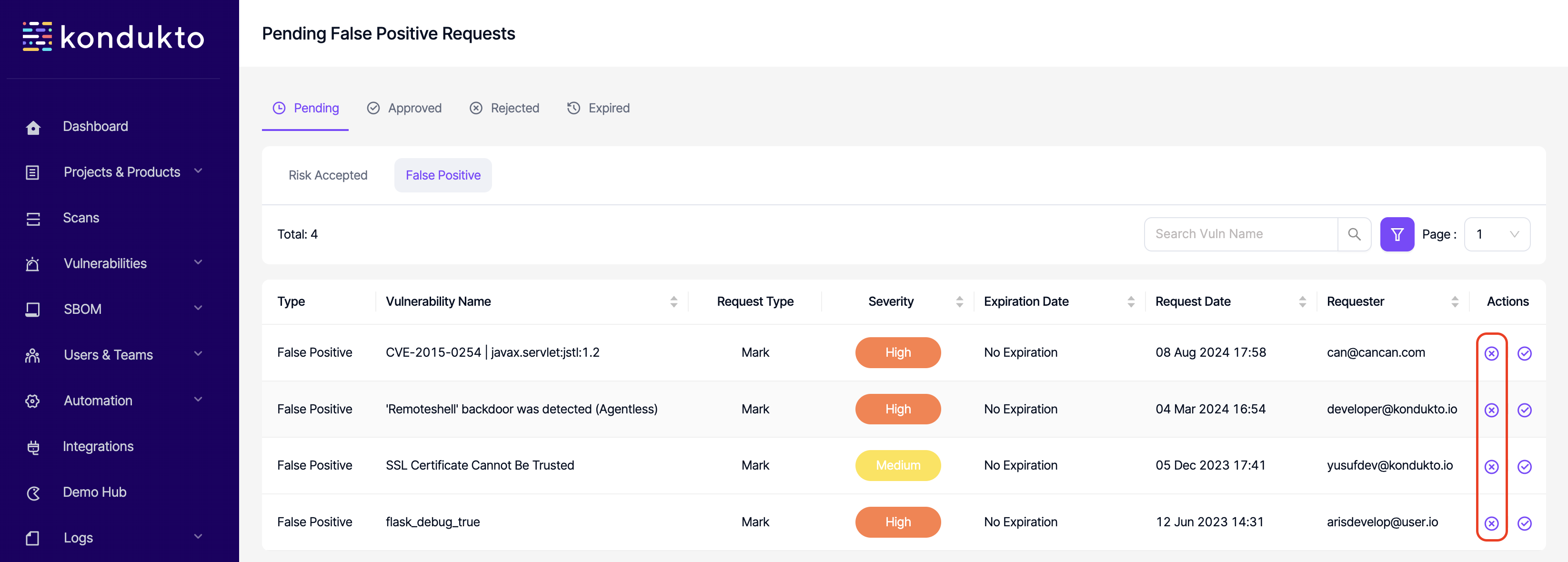
- FP Requests: Delete: This permission controls the users' ability to cancel pending FP requests made by themselves.
- FP Requests: Approve: This permission controls the user's ability to approve FP requests.
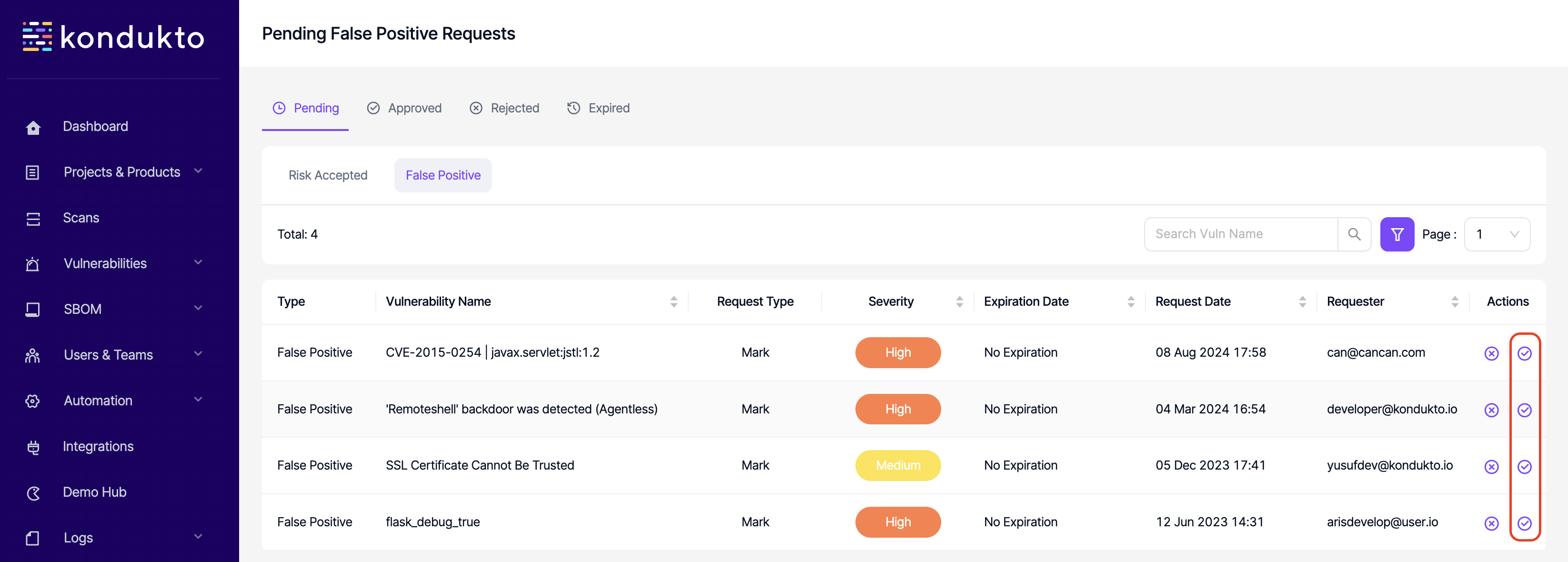
- FP Requests: Reject: This permission controls the user's ability to reject FP requests.
- FP Requests: Auto-approve: This permission controls the user's ability to mark vulnerabilities as FP without further approval.
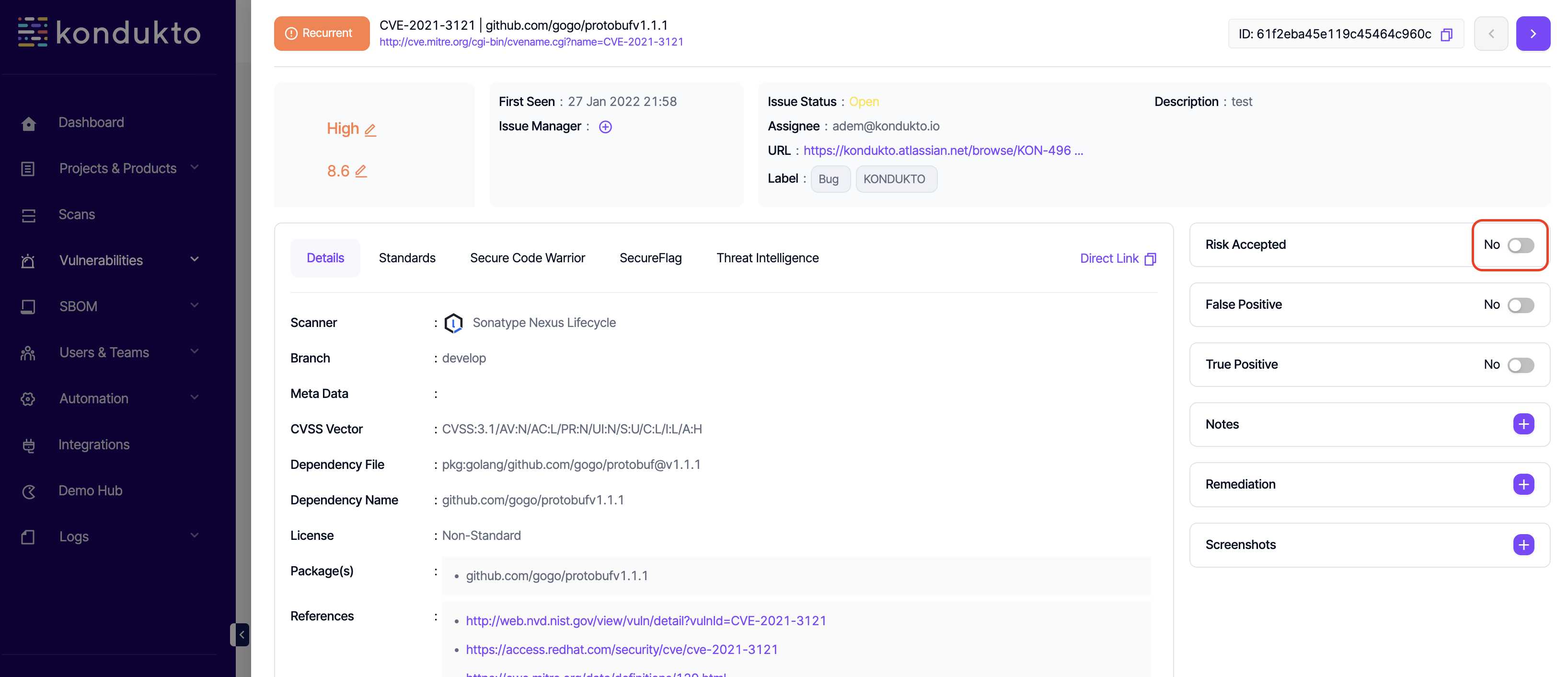
- RA Requests: Read: This permission controls the user's ability to view RA requests. This permission can not be removed unless all other RA requests related permissions are also removed.
- RA Requests: Write: This permission controls the user's ability to submit RA requests.
- RA Requests: Delete: This permission controls the users' ability to cancel pending RA requests made by themselves.
- RA Requests: Approve: This permission controls the user's ability to approve FP requests.
- RA Requests: Reject: This permission controls the user's ability to reject FP requests.
- RA Requests: Auto-approve: This permission controls the user's ability to mark vulnerabilities as RA without further approval.
Updated 9 months ago
