Issue Assignment
Issues can be manually assigned to issue managers after reviewing vulnerabilities and automatically as soon as the scans or imports are completed.
There are two tabs available under the Issue Assignment section of a project.
Settings
Settings tab allows making the required configurations to be able to create tickets on the issue manager manually. This configuration is sufficient if issues will be directed to the issue manager after a manual review.
When the "grouping issues" feature is enabled, Kondukto will automatically group vulnerabilities discovered by SCA tools that belong to the same component into one ticket on the issue manager.
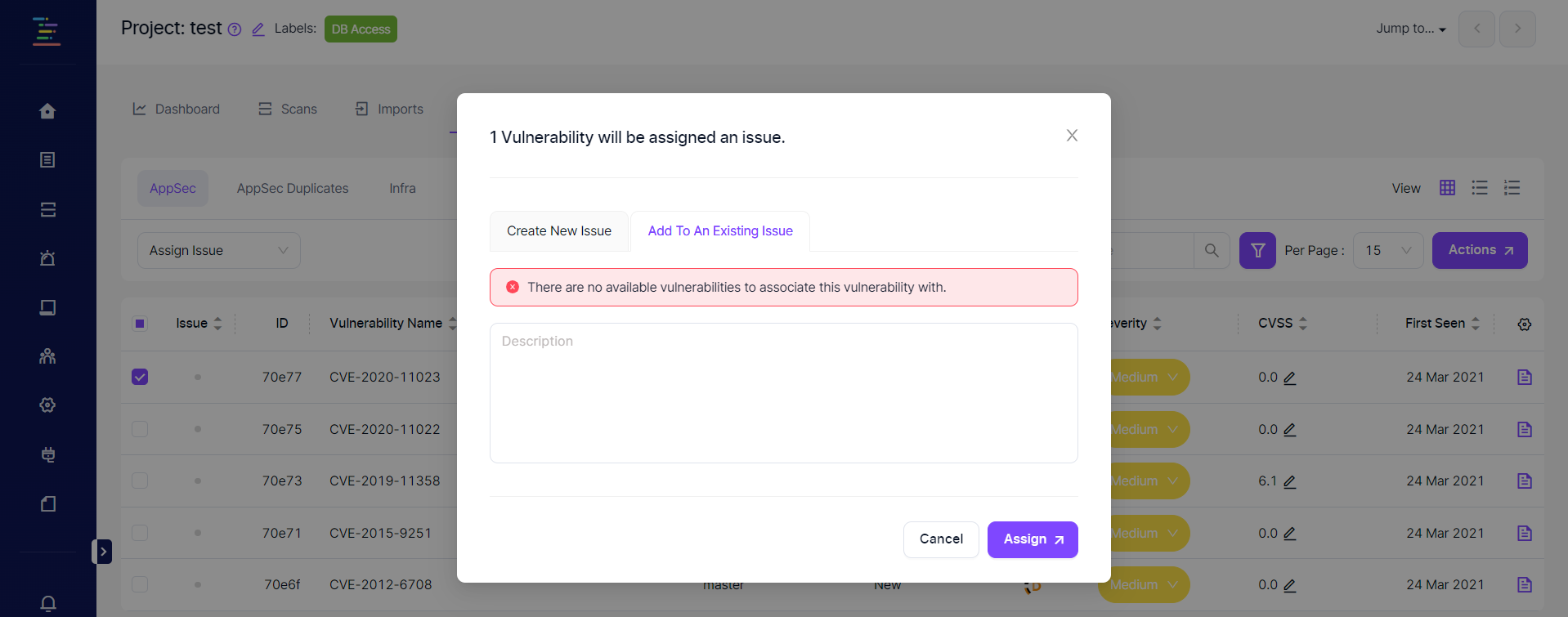
Enabling this feature will also allow adding an SCA vulnerability to an existing ticket on the issue manager rather than creating a new ticket for the vulnerability. In the screenshot below, the error message pops up since there are no SCA vulnerabilities with a ticket.
Push flags on Kondukto as labels feature allows creating labels in the Issue Manager for flags linked to vulnerabilities on Kondukto when creating a ticket for the vulnerability.
Automation
Automation tab can be used to make Kondukto create tickets automatically after each scan or import whenever there is a vulnerability that matches the defined conditions.
In the Validation Scan step, the user can opt for performing automated validation scans once the issue is marked as closed on the issue manager to ensure that the vulnerability has been fixed.
There are two options to choose from, which are ;
- Run a validation scan each time an issue is closed.
- Run a validation scan at a specific time each day, depending on whether one or more issues have been closed in the last 24 hours.
The second step relates to the assignee to whom the issues will be assigned to the issue manager.
When the "Committer when the committer is known." box is checked, Kondukto will first try to assign issues to the committer found on the software development platform. If the attempt fails, the issue will be assigned to the user specified in the field below.
The "Specific user" field indicates the user to which issue will be assigned when the committer of the vulnerability is unknown (which is the case for all findings other than SAST and IaC findings). The user must be a licensed Kondukto user to appear in the drop-down menu.
When an issue can't be assigned to the committer or a specific user, Kondukto will try to assign the issue to the issue responsible selected for the team working on the project. For cases where none of the above is applicable, Kondukto will assign the issue to the token owner generated on the issue manager.
In the third mandatory step to open issues automatically, specific criteria can be created to pinpoint the type of vulnerabilities for which issues will be created.
A new modal opens when clicking the "+Add Custom Criteria" button.
Criteria can be set using OWASP Top-10, PCI Requirement or Stride Threat Modeling categories, Severity level, CWE names, or ID.
It is possible to set combined conditions using AND statements.
In the example below, issues will be opened for vulnerabilities discovered in the default branch by the Nuclei scanner that falls into OWASP A1 or A2 categories with high and critical severity.
If for some reason Kondukto was not able to close the associated issue on the issue manager as soon as the vulnerability's status was transitioned to Closed on Kondukto, Kondukto will run a scheduled job and try closing the issue on a daily basis at 12AM.
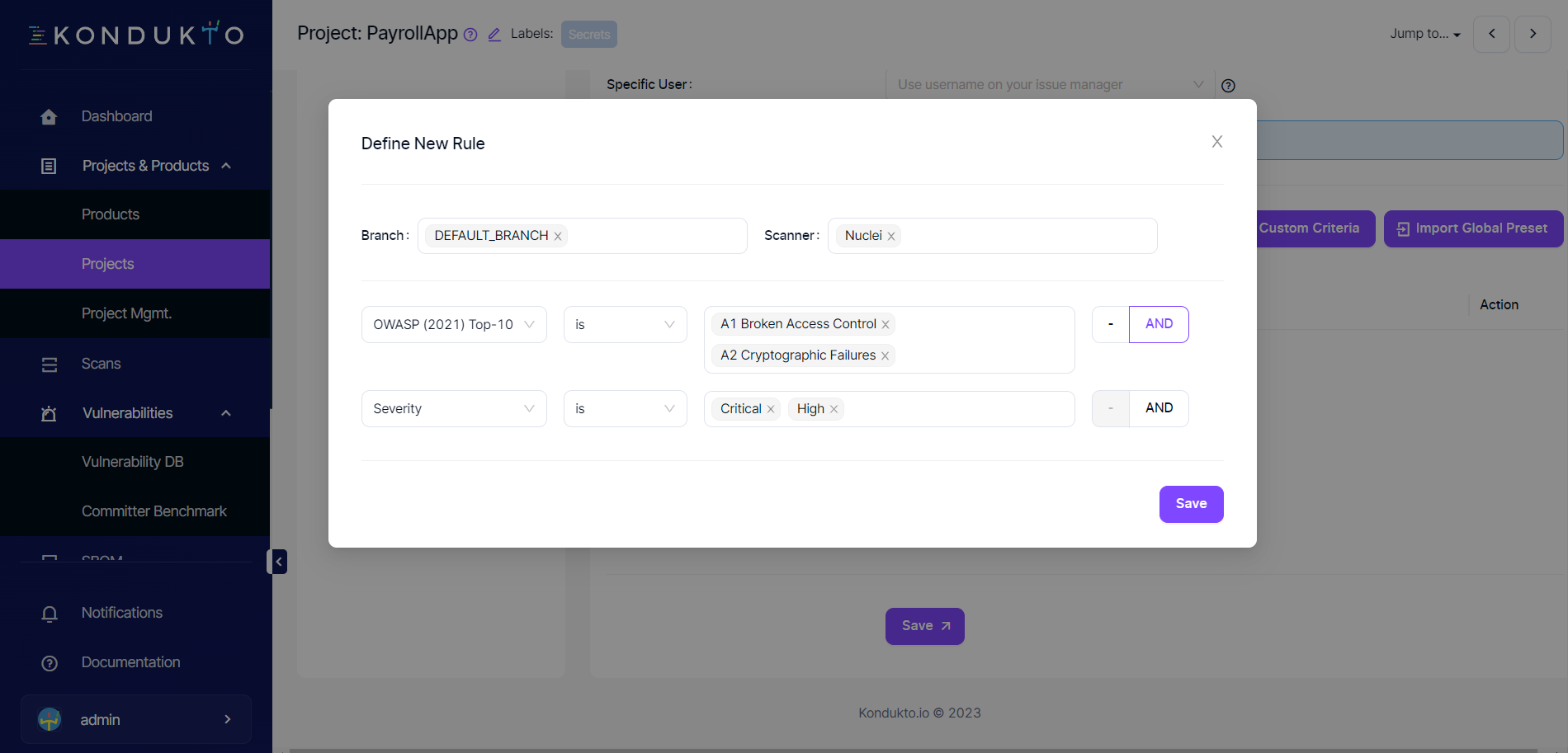
When the Save button at the lower right corner of the modal is clicked, the modal closes, and the issue criteria entered can be seen in the table. Presets created globally can also be imported to the project by clicking the Import Global Preset button.
Issue Assignment Hierarchy
Certain users can be assigned as issue responsible within the teams. When a team is assigned to a project, the issues are automatically assigned to this issue responsible based on the issue assignment criteria entered on the platform.
If the committer when committer is known box is checked under the Issue Assignment section in Project Settings, this will supersede all other users for vulnerabilities with a known committer.
If a specific user is also selected under the Issue Assignment section in Project Settings, this specific user supersedes the issue responsible for the team.
So the hierarchy is as follows for cases when all three are selected;
- Committer of the vulnerability
- The specific user selected under Project Settings
- Issue responsible selected in the team
For cases when none of the above is applicable, Kondukto will assign the issue to the token owner generated on the issue manager.
Updated 8 months ago
