Vulnerability DB
This interface allows for an in-depth examination of the details of all historical vulnerabilities. In this section, all vulnerabilities identified in the scans executed since the inception of the platform are listed.
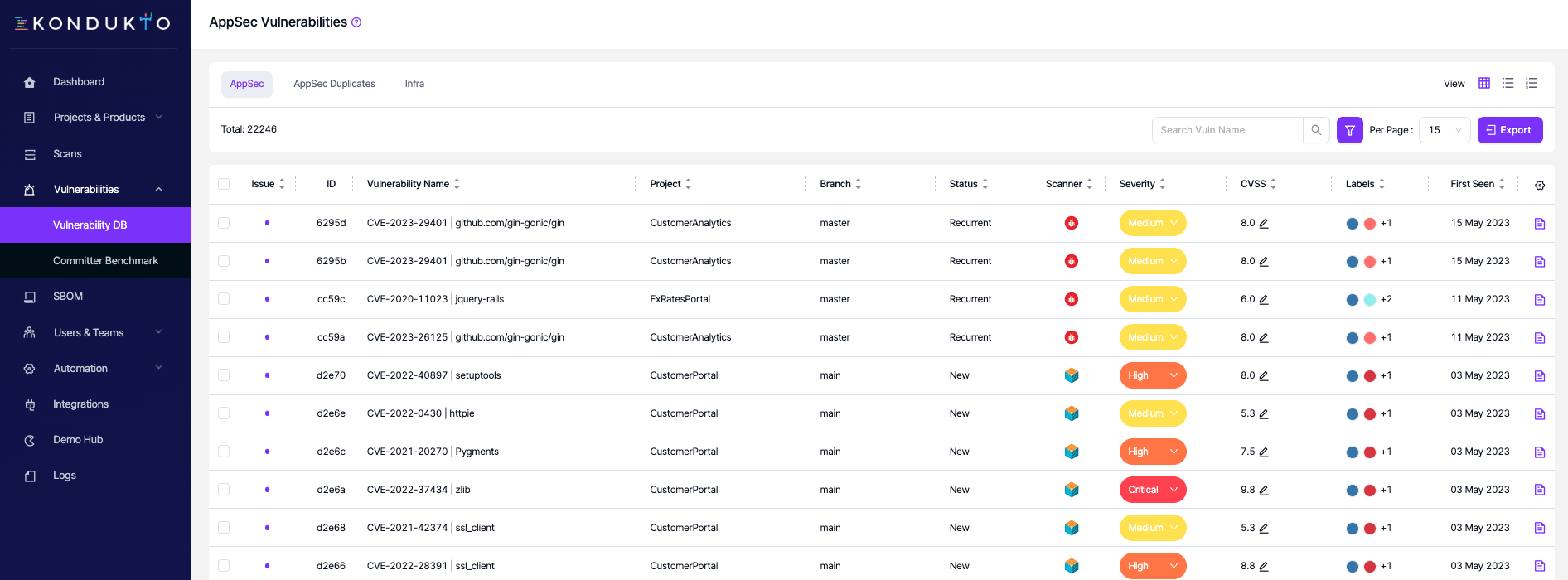
If vulnerability merging is activated in the Global Settings, a consolidated view of vulnerabilities is displayed, excluding any duplicates. If this setting is not enabled, all vulnerabilities will be displayed without exception.
Advanced filtering options can be accessed via the search box, located in the top row, which is highlighted in purple.
By clicking on the export button situated in the top row, each table, formed through sorting and filtering, can be exported in CSV format.
The severity of vulnerabilities can be manually adjusted by clicking on the pencil icon located under the Severity column.
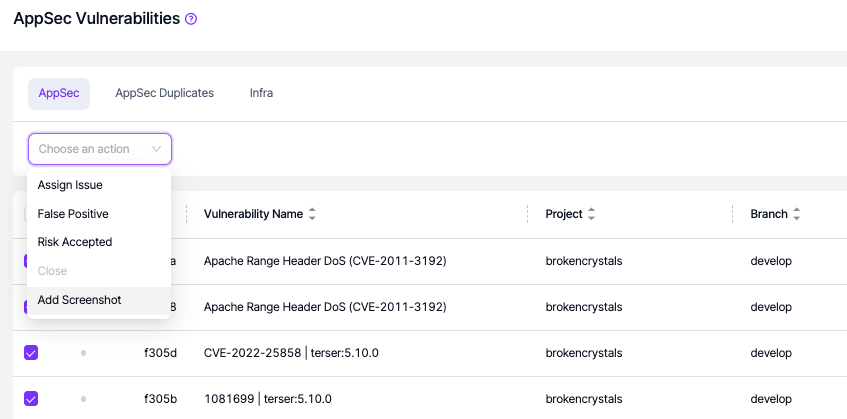
By selecting the vulnerabilities, collective action can be taken on the selected vulnerabilities.
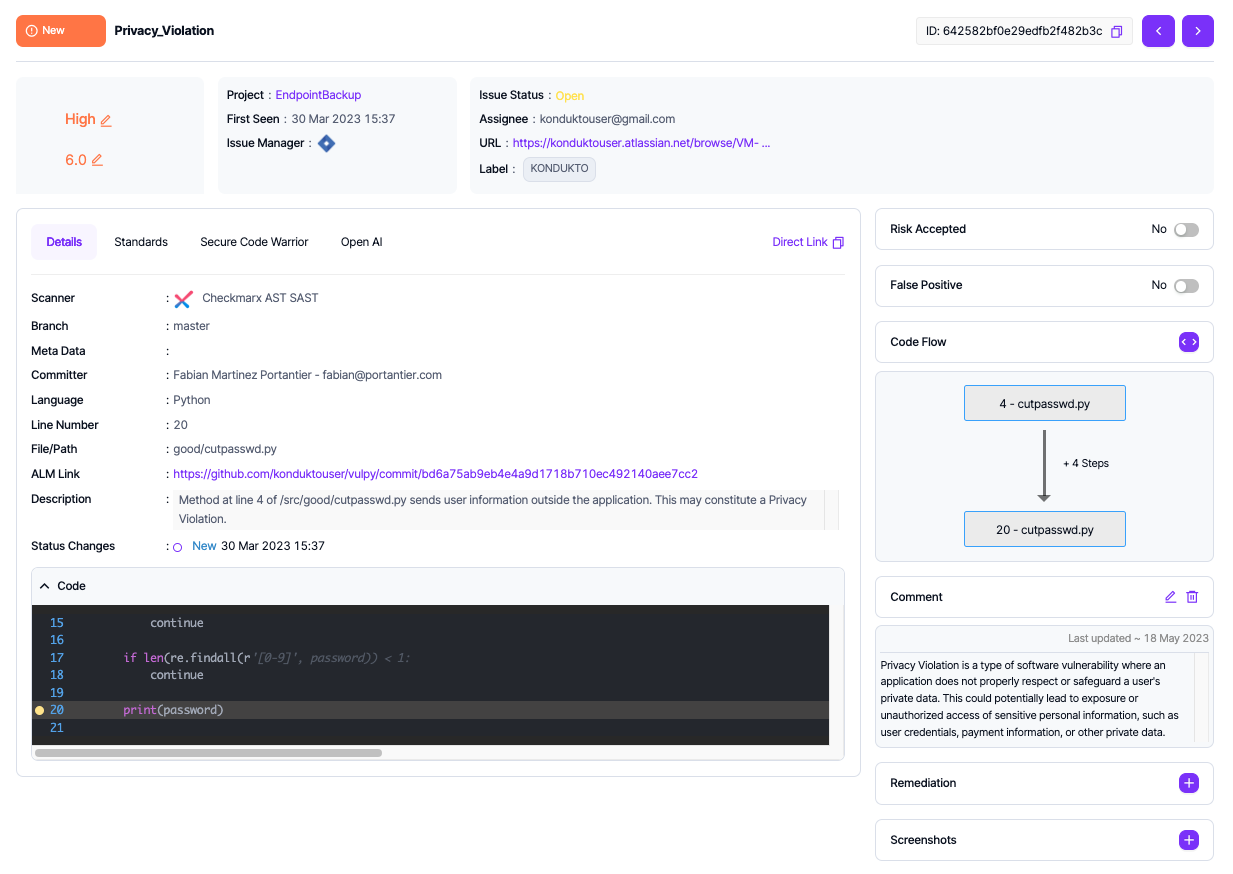
By clicking on the page icon on the rightmost side of each row, further details of the vulnerability can be accessed. The details provided vary based on the tool that identified the vulnerability. Selections for "False Positive" and "Risk Accepted" can also be made in the drawer displaying the vulnerability details.
Further information on the industry standards related to the CWE ID of the vulnerability can be found in the Standards tab.
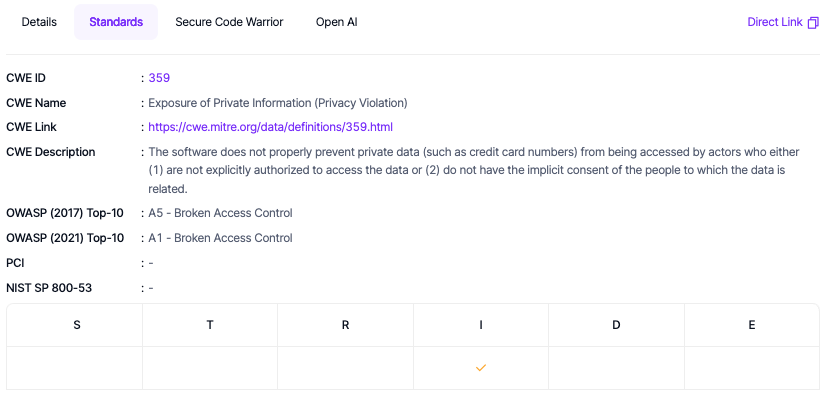
The STRIDE section shows users the potential risks associated with each vulnerability. One vulnerability can be associated with multiple risk factors under STRIDE.
The letters in the STRIDE method stand for the following ;
S: Spoofing
T: Tampering
R: Repudiation
I: Information Disclosure
D: Denial of Service
E: Elevation of privilege
In case the vulnerability carries a risk in one of the categories above, the column will be marked with a tick icon on it.
Vulnerability Deduplication
From the Global Settings, the merging of vulnerabilities can be toggled on or off. For each vulnerability, Kondukto assigns a unique hash and checks for any existing vulnerability with the same hash whenever a new scan or import is completed.
The scanner deemed decisive in determining whether a vulnerability is closed must be selected, as Kondukto relies on scan results to execute validation scans and close vulnerabilities. Vulnerabilities from the prioritized scanner are designated as master vulnerabilities, with identical vulnerabilities from other scanners listed as child vulnerabilities of this master vulnerability. The only exception to this rule arises when an issue for a vulnerability has already been opened. In such cases, despite the priority of scanners, vulnerabilities identified later by other scanners will be categorized as child vulnerabilities.
Master vulnerabilities are the only ones displayed on dashboards, and only they are taken into consideration when opening issues, running validation scans, sending alerts, and checking security criteria. Kondukto automatically merges separate listings of the same vulnerability by the same scanner, thus reducing the number of vulnerabilities to manage.
Updated 8 months ago
